Kevin Lancaster Joins usecure’s Board to Accelerate North American Channel Growth
Kevin Lancaster joins usecure as a Non-Executive Director, strengthening our North American channel growth and accelerating...
Resource Center
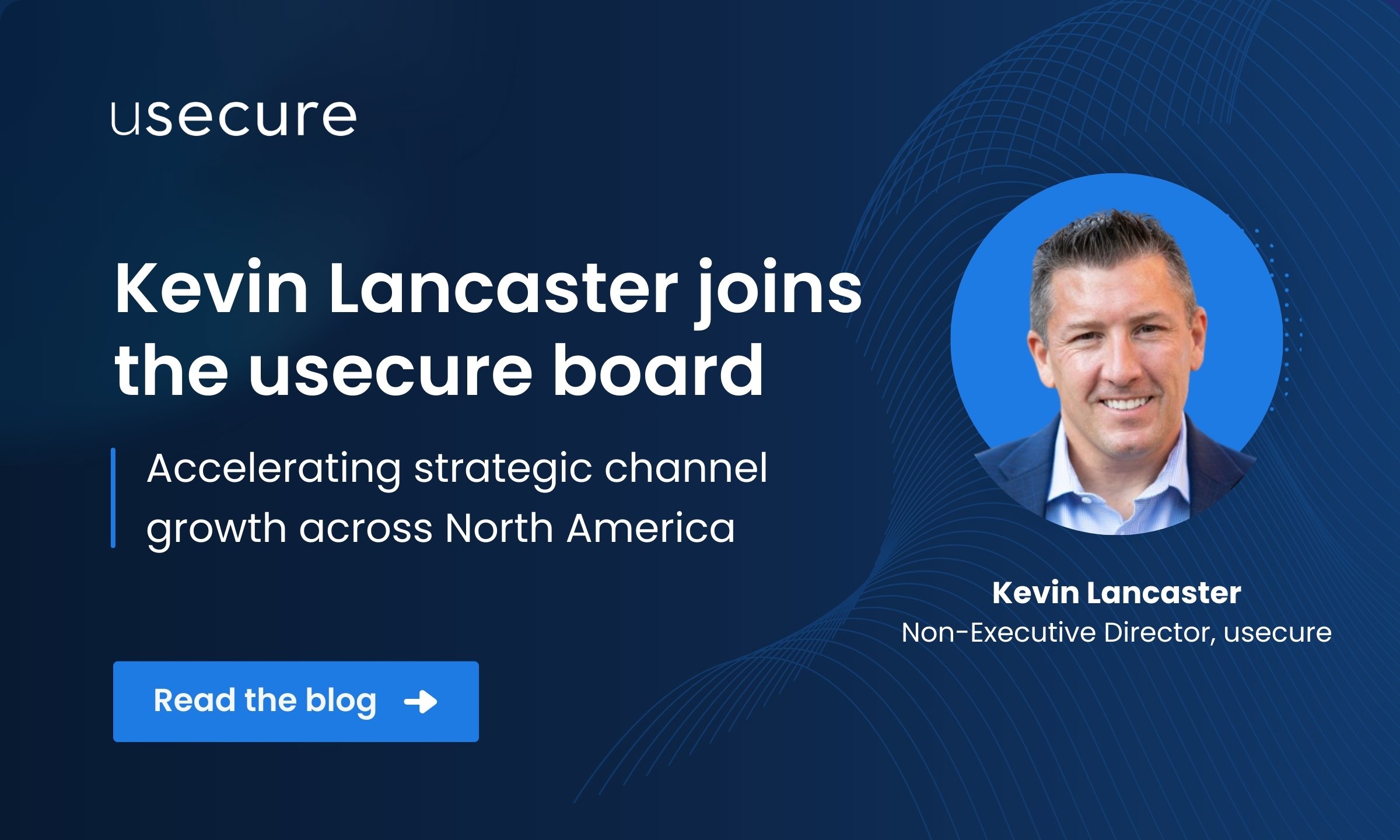
Kevin Lancaster joins usecure as a Non-Executive Director, strengthening our North American channel growth and accelerating...
-2.png)
Seasonal scams rise sharply from Black Friday through the new year. Explore targeted training, realistic phishing simulations and...
-3.jpg)
Ten Channel experts share quick tips on using AI to stay competitive in 2026.
.png)
Watch usecure’s final 2025 webinar on-demand. Explore key cybersecurity lessons, human risk trends, and 2026 predictions - plus a...
.jpg)
usecure Sponsors Channel Program’s Holidaze 2025 The most festive event of the MSP year is here — and usecure are proud to be part...

Learn what the EU’s Digital Operational Resilience Act (DORA) means for SaaS vendors in the years ahead, how it affects...

Discover November's updates: new AI courses, fraud awareness resources, and platform improvements to help partners and customers...
.png)
Join usecure’s final 2025 webinar to explore key cybersecurity lessons, human risk trends, and 2026 predictions - plus a first...

Discover October's latest updates from usecure, including enhanced phishing simulations, new training resources, & tools for...

The Harrods data breach affecting 430,000 customers highlights how human error and vendor risk drive cyber threats. Learn what...

Join Cybersecurity Awareness Month 2025 to reduce human cyber risk with practical resources and training, emphasizing the...

Discover how Infinity Group achieved 99% phishing resilience and cut human cyber risk by 60% with usecure's automated training and...

Discover how the Gucci, Balenciaga, and Alexander McQueen data breaches highlight the growing impact of human risk in...
.png)
Missed the live session? Watch our on-demand webinar to learn how to stop phishing attacks from spreading across your business -...

Discover how SMBs can strengthen cybersecurity from the inside out — and gain recognition through SMB1001 certification.
%20(1).png)
AutoPhish now includes Productivity Tools to deliver more relevant phishing simulations, improving engagement, detection, and...

Discover September's updates for MSPs, including smarter prospecting guides, advanced phishing simulations, and new compliance...
-2.png)
Proven two-step strategy for MSPs to convert prospects faster using usecure’s Domain Scan and Human Risk Report. Drive urgency,...

Explore what’s new at usecure in August, from workplace safety training and smarter platform tools to exciting partner giveaways...

Discover the top 3 cybersecurity trends MSPs must act on in 2025 — from rising human risk and stricter global regulations to...
.png)
Discover how to turn prospects into paying customers faster using usecure’s free tools - from instant Domain Scans to automated...

usecure joins Channel Daze 2025 to celebrate MSPs with 10 days of giveaways and over $17,000 in prizes. Register now for your...

Qantas' recent data breach highlights the growing impact of human error in cybersecurity. Explore what went wrong and how...
.png)
usecure, a leading human risk management solution, today announced the successful closing of its Series A investment with Kennet...
.png)
usecure celebrates top rankings in G2's Summer 2025 Report, showcasing strengths in Security Awareness Training and Dark Web...

Master GDPR compliance with our practical guide. Explore mandatory obligations, recommended best practices, and optional...

Discover the latest updates in security training tools, including new courses, faster deployment options, and enhanced phishing...
.png)
A record 16 billion passwords have been leaked in the largest data breach to date. Learn how this impacts your business, how...

usecure has been named Most Valuable Vendor of the Year – EMEA at Pax8 Beyond 2025, recognizing our impact on MSP growth,...
-2.png)
Learn how usecure's Report Hub enables compliance leaders to measure awareness, prove effectiveness, and reduce risk through...
-3.png)
Join Start Tech’s Ian Groves and usecure’s Lorna Burman to see how Start Tech automated security awareness and scaled delivery....
.png)
Transform policy management from a compliance checkbox to a proactive human risk strategy with uPolicy's modernized platform....

Discover the latest updates for MSPs in June, including a comprehensive sales playbook, new training courses, updated phishing...
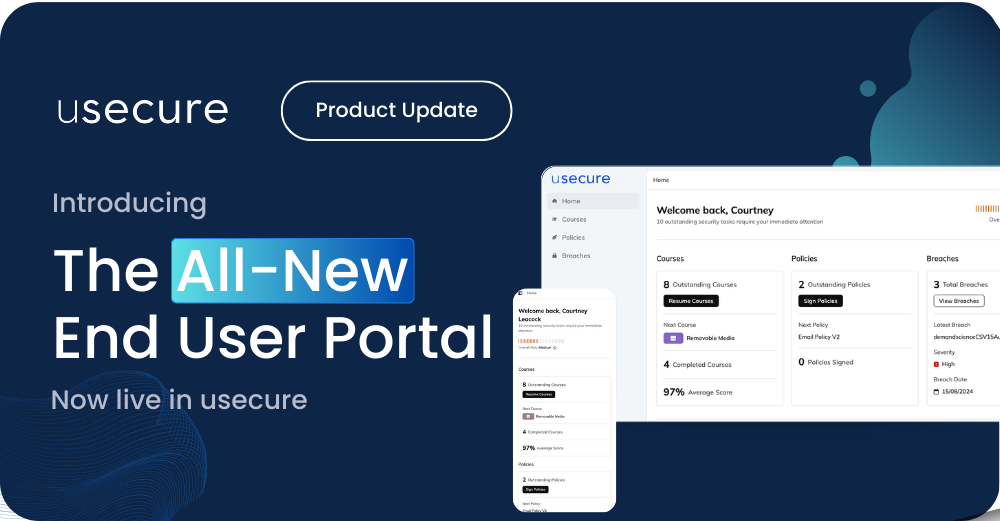
The redesigned End User Portal gives you faster access to your training, policies, and breach alerts — all in one, mobile-ready...

Discover the three key cybersecurity standards shaping the UK nuclear energy sector—NISR 2003, NCSC CAF, and ISO/IEC 27001. Learn...
Learn about the M&S cybersecurity breach and how it exposes the growing human risk in cybersecurity. Discover how employees can...

We’re now updating 3 Auto Enrol courses every month—plus rolling out new languages and replacing outdated videos, all with zero...
-3.png)
Discover how MSPs can leverage Report Hub to turn Human Risk Reports into recurring revenue by showcasing consistent value and...

Discover how MSPs can onboard clients in minutes with usecure. Learn to automate training, cut admin time, and deliver real...
.png)
Discover how over 4,200 organizations are transforming human risk strategies through consistent and effective Security Awareness...

Discover the latest updates in Security Awareness Training, including new courses, phishing templates, and the comprehensive 2025...
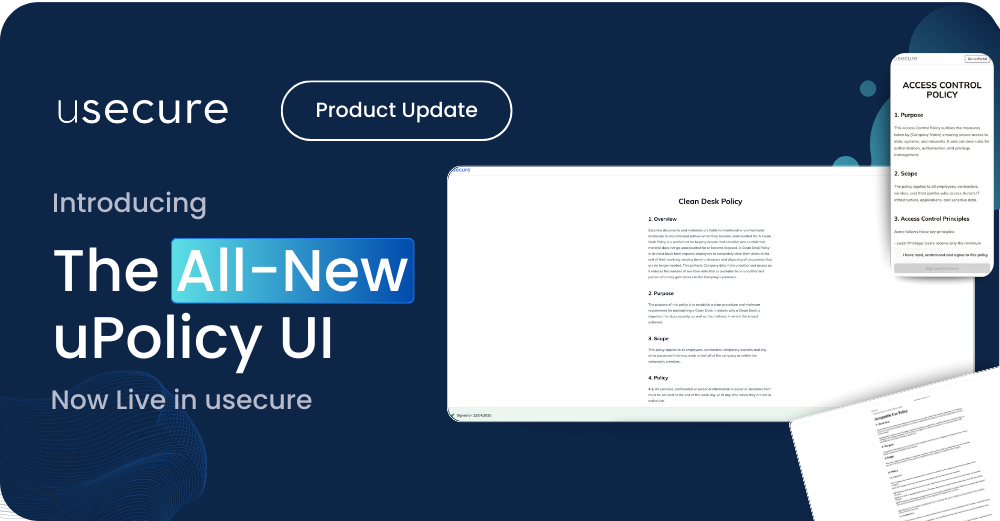
Discover the new, faster, and streamlined Policy UI at usecure, designed to enhance user compliance through a modern,...

Discover SMB1001 — a practical, scalable cybersecurity framework built for SMBs. Learn how it works, why it matters, and how...
.png)
Learn how MSPs can deploy fresh, realistic phishing simulations to boost client security and resilience with minimal effort....
.png)
Experience a faster, smarter, and more intuitive course UI with usecure's latest update, optimizing your training on any device.
.png)
Watch our on-demand webinar to understand updates to global regulations, what they mean for MSPs and how to turn compliance into a...
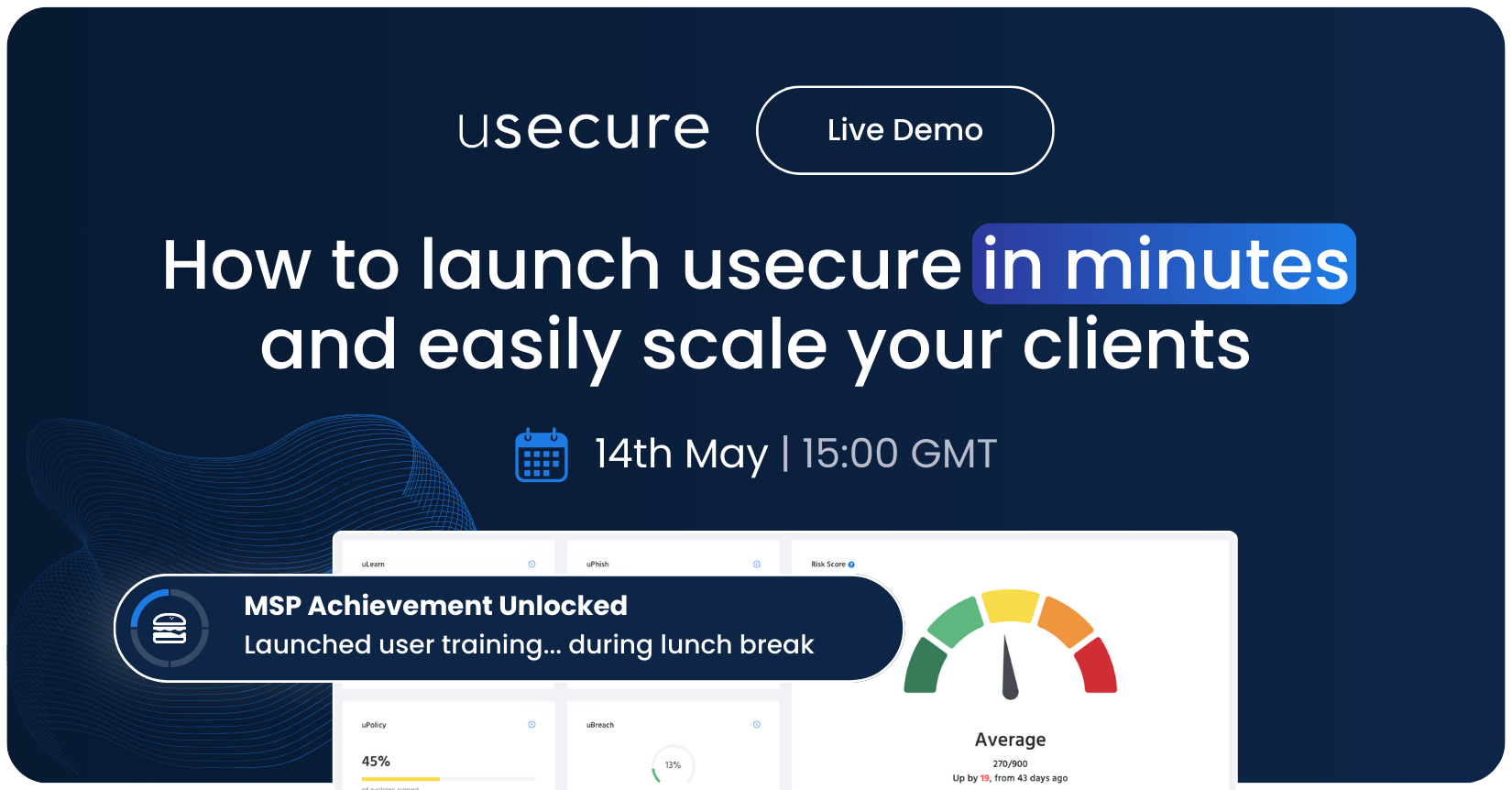
Scale faster. Deploy smarter. Join us for a webinar that shows how easy it is to get started with usecure - whether you’re new to...

Discover April's MSP product updates, including new AI safety courses, phishing templates, platform enhancements, and more. Stay...
.png)
We’re excited to announce that usecure is now live in the Sherweb Marketplace! Cybersecurity isn’t just about firewalls and...
.png)
usecure’s G2 Spring 2025 Report highlights top rankings in Security Awareness Training and Dark Web Monitoring, showcasing our...
-1.png)
In our recent session we covered how you can articulate usecure's value and stand out in a crowded MSP market. Catch it on-demand...
.png)
As regulations like NIS2 evolve, MSPs must stay ahead of compliance requirements and emerging cyber threats to protect clients,...
.png)
Mitigate AI and Shadow IT risks with proactive governance, employee education, and robust security monitoring to safeguard your...

Discover March's updates: new training courses, phishing templates, platform enhancements, and the 2025 Cybersecurity Content...
.png)
Apple’s removal of Advanced Data Protection in the UK raises privacy and security concerns for individuals and businesses, urging...
-1.png)
Learn how to differentiate your MSP, and position security & compliance as your competitive advantage to win more clients and...

Stay updated with February's key partner updates: new courses, enhanced Auto Enrol features, phishing templates, and the new 2025...

Discover why global brands like Vodafone and Mizuno trust usecure for tailored cybersecurity solutions across various industries,...
.png)
Stay ahead in cybersecurity with our 2025 Partner Content Calendar, offering structured plans and timely updates to enhance your...

Stay compliant with AI security by understanding risks, implementing governance policies, and utilizing uPolicy for streamlined...

Discover how Human Risk Management (HRM) offers a proactive, data-driven approach to reducing cybersecurity risks through targeted...

Discover how Human Risk Management (HRM) supports compliance with global cybersecurity standards. Learn how key HRM components...

Discover usecure's latest updates for January 2025, including G2 recognition, new courses, templates, and platform enhancements to...

usecure celebrates major recognition in G2's Winter 2025 Report, excelling in security awareness training and dark web monitoring,...

Stay secure with iOS 18.2 by addressing critical security vulnerabilities and implementing proactive device management in your...

Explore usecure's December updates with platform enhancements, new courses, festive templates, and a review of 2024's key...

Discover the latest enhancements in usecure's November update, featuring improved uBreach Pro capabilities, new NIS2 and US...
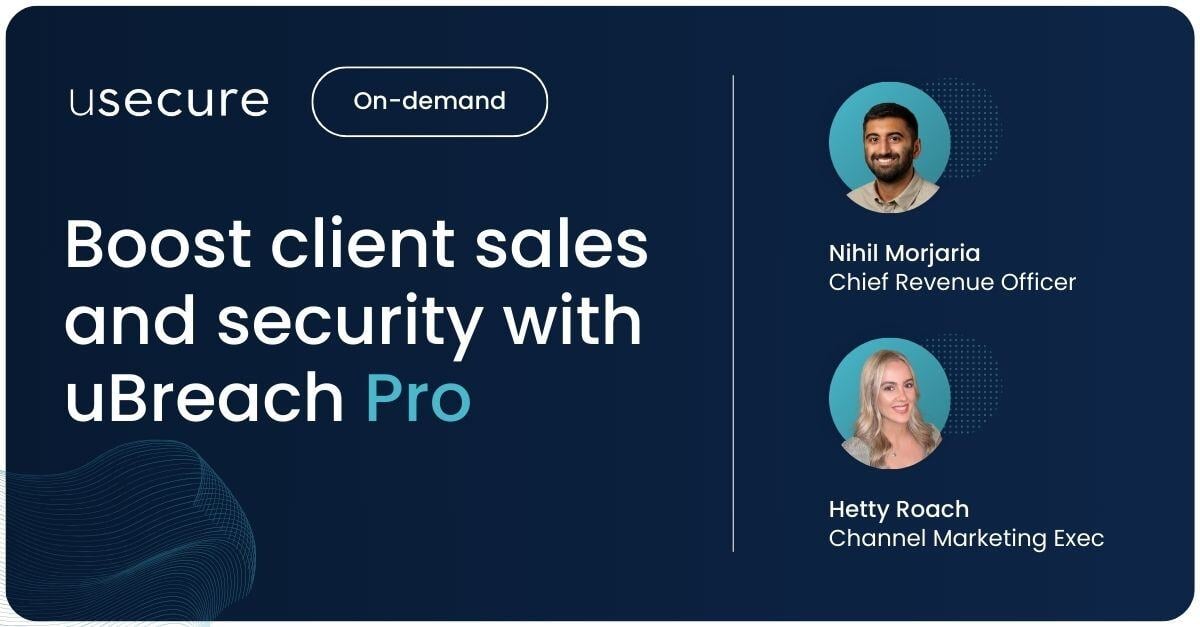
Explore the game-changing capabilities of uBreach Pro, a proactive dark web monitoring tool designed specifically for MSPs.

Discover how HumanKind reduced cyber risk by 61% through usecure's comprehensive human risk management platform, enhancing staff...

Discover how Penleigh and Essendon Grammar School reduced cyber risk by 52% in just 12 days with usecure's tailored cybersecurity...
-2.png)
New from usecure: Holiday cybersecurity toolkit for MSPs. Includes phishing templates, courses, and Black Friday resources

Are you ready to take your MSP services to the next level? This 30-minute session will show you how uBreach Pro can do just that.
%20(1)-2.png)
Catch our recent vendor highlight with Pax8, where we discuss the features and benefits of usecure and our human risk management...
.png)
Our very own Lorna Burnam made it on to IT Channel Oxygen's 2024 Influencers list, check out what she had to say in her recent...

Join usecure at Giacom's MSP Cloud Live Event - connect with industry experts, and discover the latest in cloud solutions.
Discover how to build a simplified cybersecurity practice with experts from usecure, Crayon and DNSFilter.
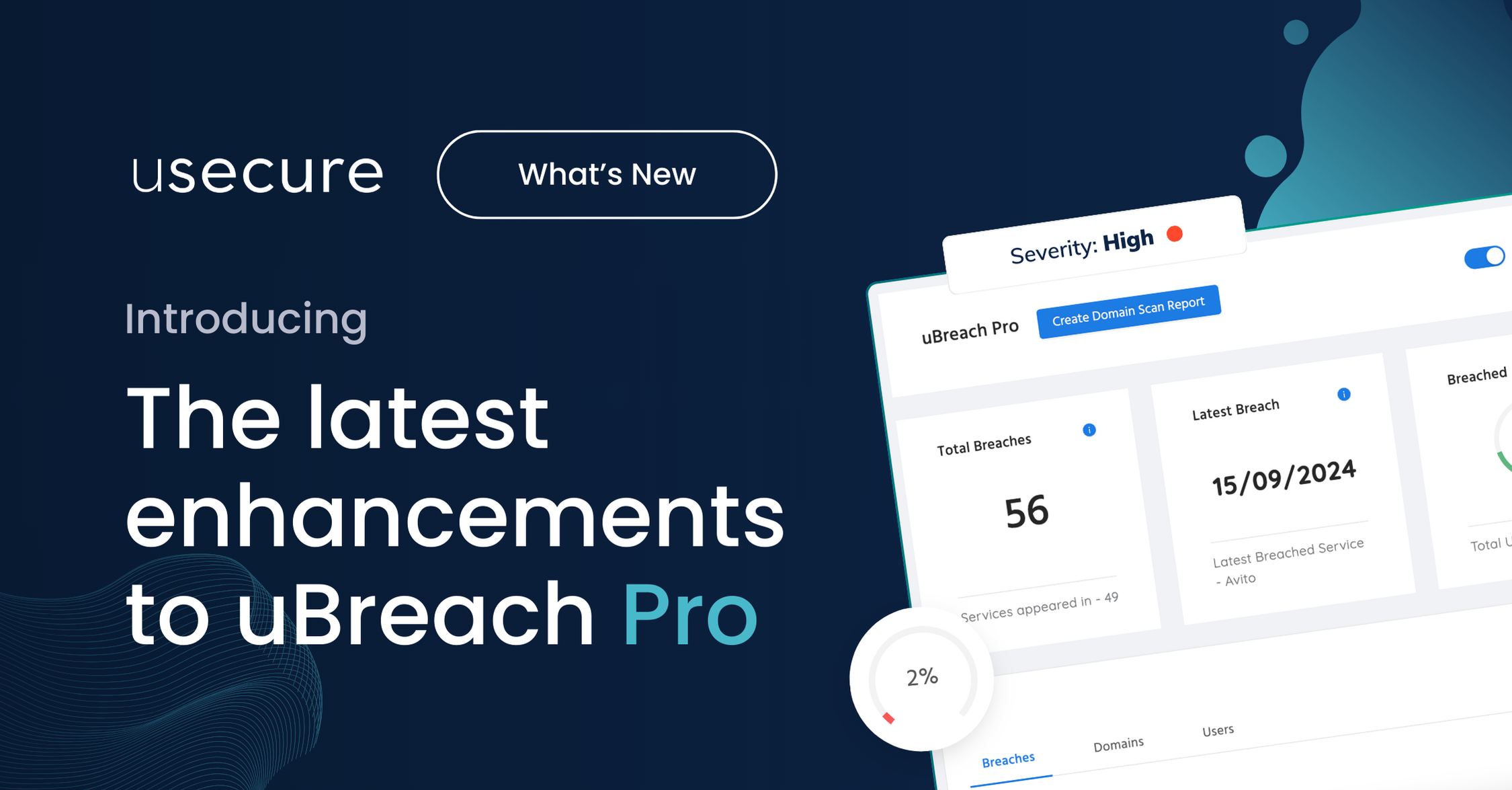
We’re thrilled to announce exciting updates to uBreach Pro, usecure's cutting-edge dark web monitoring platform tailored for MSPs.

usecure has been awarded three prestigious Category Leader badges from Channel Program.

Here's what's new on the usecure platform this October: US Election Scams, Infostealer Malware, Colorado Privacy Act, and more.

Ahead of the NIS2 Directive deadline, understand how to prepare and use the right strategies for enhancing your organisations...

Join usecure at CompTIA EMEA Member & Partner Conference - connect with peers & thought leaders for cybersecurity success with...

Join usecure at Managed Services Summit Manchester - transform your cybersecurity with HRM to stay resilient in today's rapidly...

Discover how Winning Group reduced phishing risk by 90% in 6 months using usecure's human risk management solution, boosting...

Discover how Mentor Group achieved ISO/IEC 27001 audit success with Usecure's human risk management solution. Learn how tailored...

Discover how Usecure helped Heffron reduce human risk scores by 50 points in just six months. Learn how automated phishing...

Learn how usecure helped IT Visionaren, an MSP in Sweden, deliver cybersecurity training to hundreds of end users with minimal...

Learn how usecure helped IT Visionaren, an MSP in Sweden, deliver cybersecurity training to hundreds of end users with minimal...

Discover how Usecure's automated HR management solution streamlined cyber training for a global MSP's 20+ clients, reducing...

Discover how a financial services firm reduced their human cyber risk by 91% with usecure through tailored cybersecurity...

Learn how MSPs use usecure to automate human risk management. Discover how features like uLearn, uPhish, and custom reports help...
.png)
Learn how to protect your business from phishing attacks with 7 simple steps. Discover key strategies, industry-specific risks.
.png)
Discover 5 essential strategies to protect your business from dark web threats. Learn about dark web monitoring, proactive...
.png)
Discover how effective policy management can protect your business from compliance risks and security breaches.

Learn about our new courses on the Sarbanes-Oxley Act, Effective Communication in Cybersecurity and Voice Cloning Scams, and view...
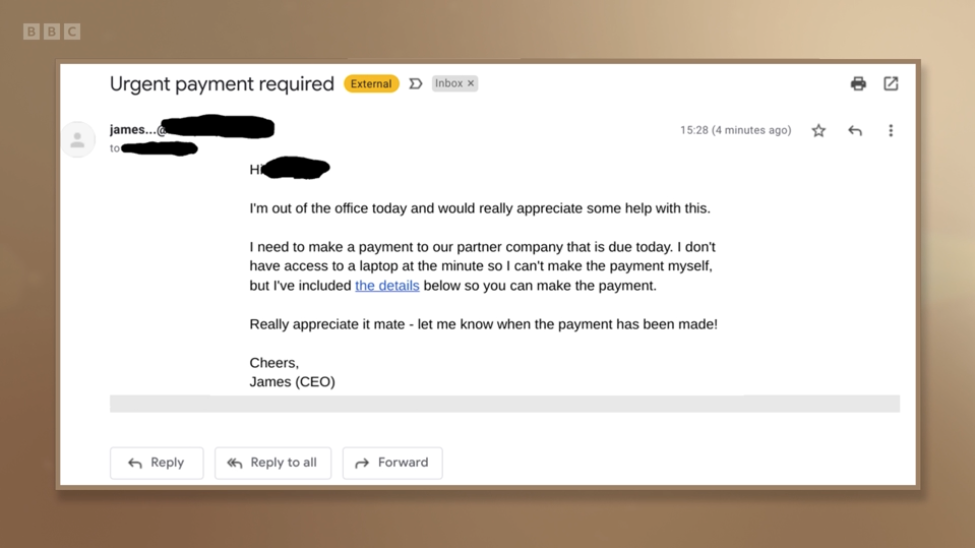
usecure was recently featured on BBC’s Morning Live during a segment dedicated to raising awareness about the growing threat of...
.png)
Explore the most notable data breaches of 2024. Discover data breach trends, learn why monitoring the dark web is crucial and how...

Discover 10 effective strategies to reduce human error in cyber security. Learn how to strengthen your organisation's security...

Animated micro-phishing course, Typosquatting training, UK Anti-Bribery training and more: Find out what's new on the usecure...

Along with 31 other channel vendors, we're partnering with Channel Program to bring you 10 days of incredible prizes.

Discover the importance of CIS Control 14 and its 9 essential safeguards in enhancing security awareness and skills within your...

Here's what's new on the usecure platform this July: training on India DPDP Act and PCI DSS, and 250+ new simulated phishing...

Discover the increasingly popular CIS Controls framework. Deep dive into the 18 Controls and 153 Safeguards and learn about the...

Here's what's new on the usecure platform this June: Role Based Access for admins, and new courses on text pests, IVR scams, FTC...

We are thrilled to announce that Kris Zentek has joined usecure as our new Chief Product Officer.
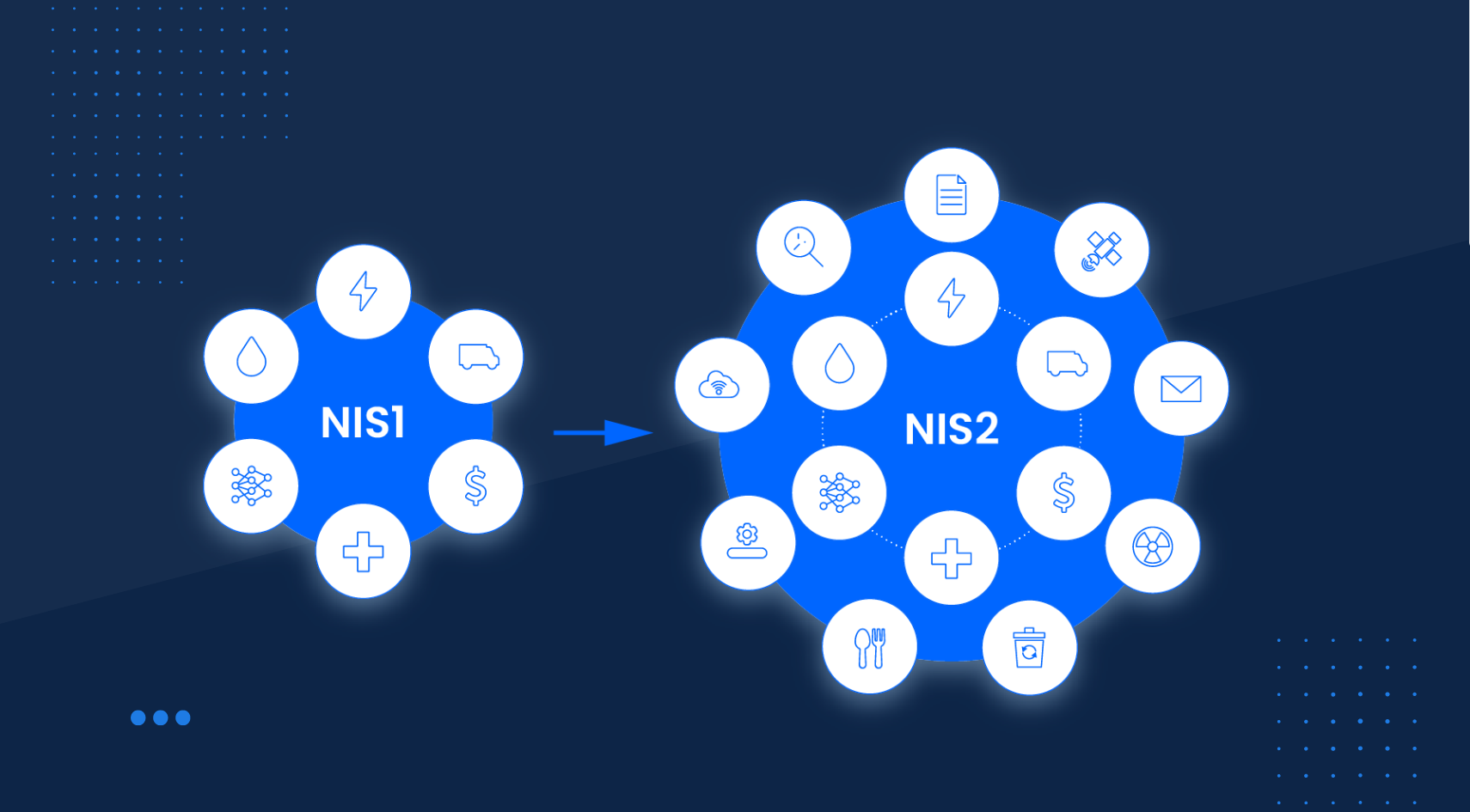
Explore the enhanced NIS 2 Directive, the EU's updated cybersecurity framework designed to strengthen security across its member...

New courses on scams targeting finance employees, additional phishing templates for Irish brands, and more in your usecure partner...

usecure, the leading human risk management solution for managed service providers (MSPs), is excited to announce its strategic...

Explore the top cybersecurity threats of 2024, get to know the latest trends and learn how to shield your organisation with...

April 18, 2024

Here's your usecure MSP Update for April 2024: New AI tools & HIPAA courses, new email designs, and the events where you'll be...

Explore the key updates of PCI DSS from v3.2.1 to v4.0, learn the highlights of the latest version, how to achieve compliance with...

Find out what's new for usecure partners this March: attachment phishing simulations and training, QR code courses, BYOD policy...
.png)
Learn how a cybersecurity risk assessment is run, and what it can mean for your business in terms of financial, protective, and...
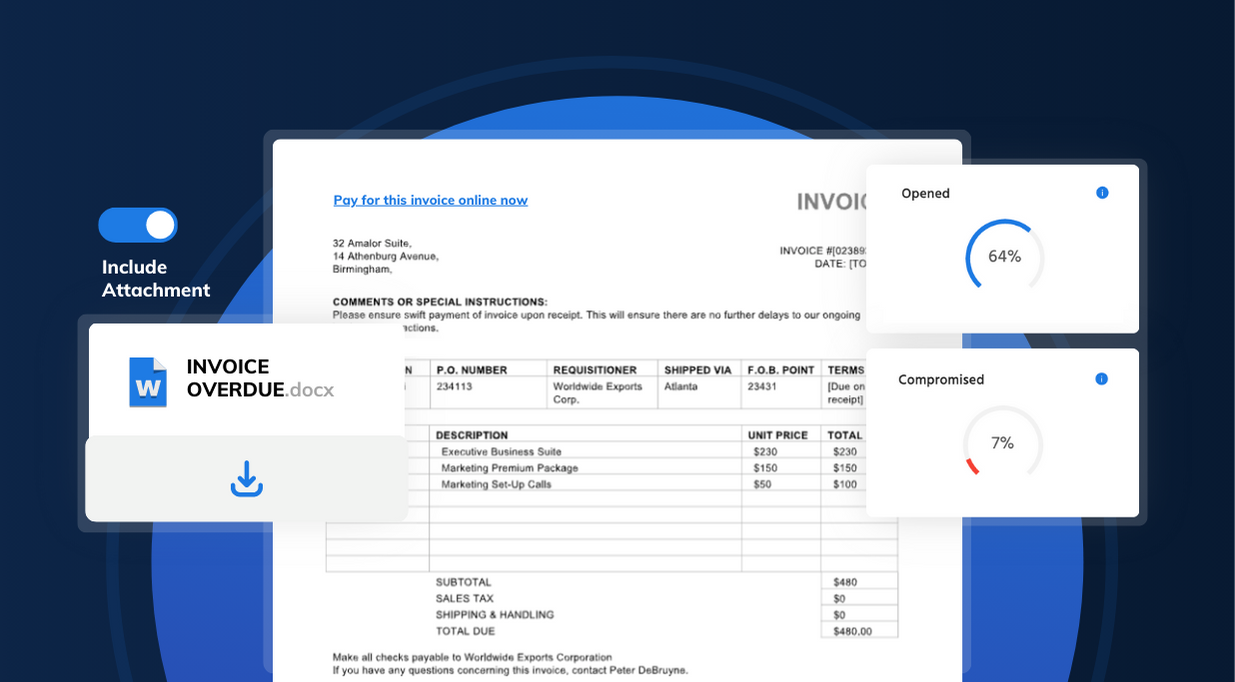
Introducing the latest update to usecure's phishing simulation feature – attachment-enabled phishing simulations in uPhish.

Here's what's new on the usecure app this February: the uBreach Pro advanced dark web monitoring tool, MFA Fatigue course, bulk...

Learn what you should do to protect yourself from the massive leak of 26 billion data records.

Explore the intricacies of MFA fatigue attacks, learn its manifestations, the potential victims, and preventive measures to...
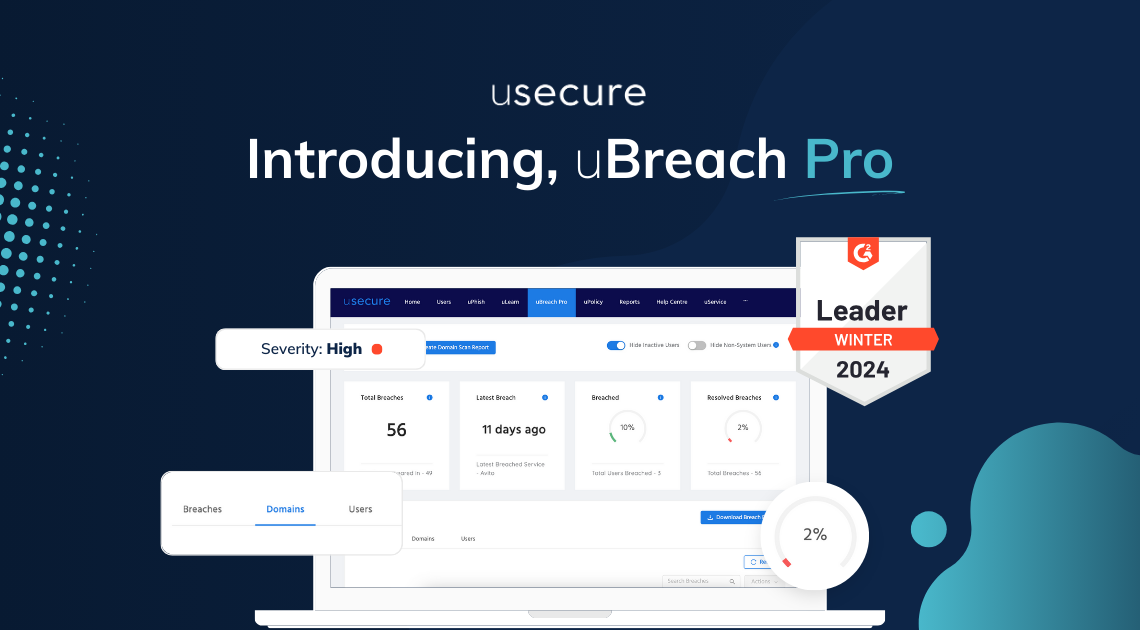
uBreach Pro is the advanced dark web intelligence service for MSPs, combining a proactive solution for eliminating dark web...

This blog offers an in-depth exploration of each strategy and practical tips for effective implementation to help you enhance your...

Last month we released a new QR code simulated phishing feature for uPhish, accompanied by a number of new templates based on...

Read on to discover six best practices businesses should employ to ensure the safety of customer data and compliance with various...
December 22, 2023

Discover the dangers of QR code phishing and learn how to safeguard your personal and business information.
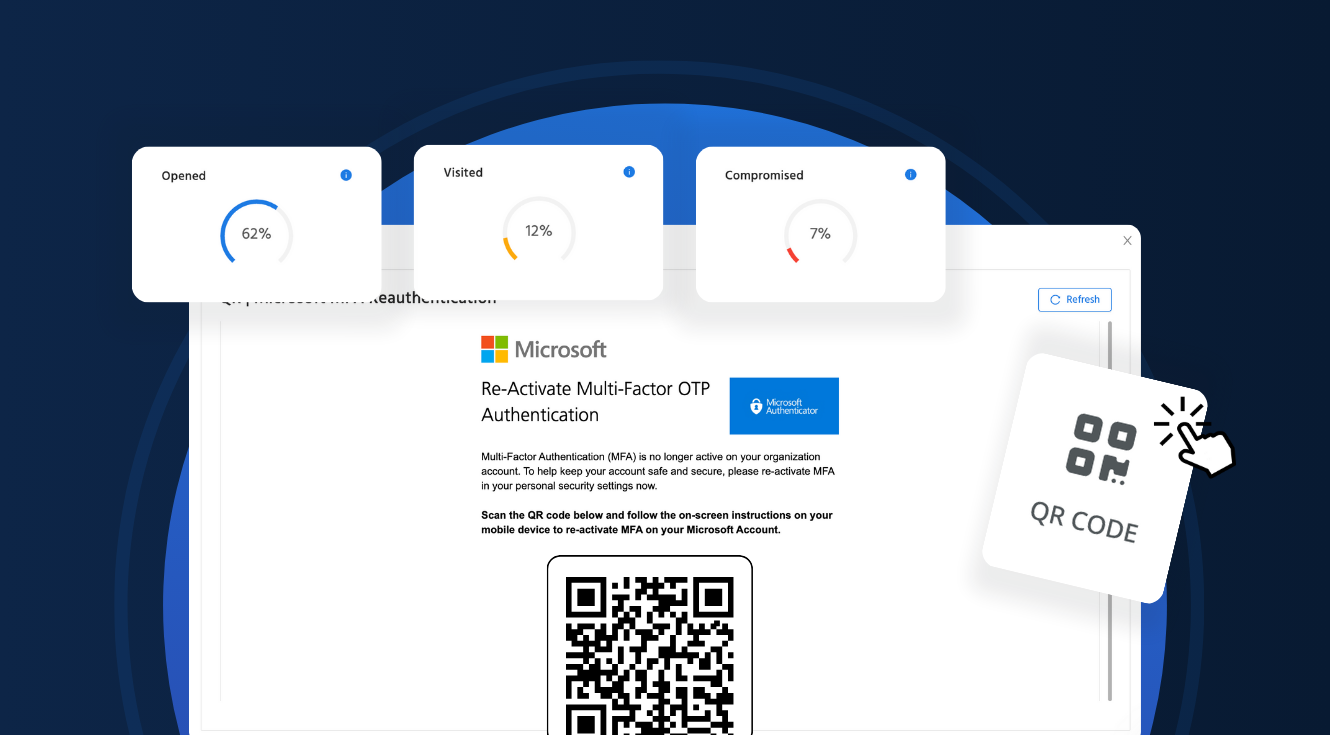
Easily embed QR codes into your usecure phishing simulations to assess employee vulnerability towards the growing threat of...

Bulk enrolment in the Course Library, Consumer Duty training and Micro Phishing course for uPhish - learn about everything new on...
.png)
Learn what steps you can take to help your users defend their email inboxes, devices and company data from phishing scams this...
%20usecure.png)
Dive into the world of insider threats, unravel their tactics, and gain valuable insights on safeguarding your business...
.png)
Simplify the complex world of regulations and standards. Explore the power of our employee training and policy management tools...
.png)
Learn why training on the new UK FCA's Consumer Duty is essential for financial services companies, and how to create an effective...

Here's all that's new on the usecure platform in November 2023: Single Sign On (SSO) support, a New Zealand Privacy Act 2020...

Explore New Zealand Privacy Act. Discover the purposes, scope, requirements and penalties for non-compliance. Learn the 5 easy...
.png)
Learn the importance of financial data security for SMEs and the important 8 steps to safeguard your data!

Here's your October newsletter for usecure partners - learn what's new on the usecure platform this month.
.png)
A convenient guide for small businesses to prevent and effectively manage data breaches after the event.
%202023%20India.jpg)
Discover how DPDP Act mandates consent-based usage. Learn about its principles, scope and requirements, as well as how to increase...
.png)
Discover how usecure earned a top spot in Capterra's Germany 2023 HR Trend Report for efficient, user-friendly Policy Management...

Email Thread Hijacking and PCI DSS courses, an update to Gap Analysis, changes to how inactive users are handled and more - here's...
.png)
Explore different types of spoofing attacks, learn strategies and tips to prevent them and discover the importance of employee...
%20.jpg)
Dive into GDPR principles and requirements. Learn the hefty consequences of non-adherence and explore how usecure can elevate your...
.png)
Learn the significance of human risk management via the lens of the Northern Ireland police data breach. Discover best practices...

August 11, 2023

Here's what new on the usecure app this month: Staying Safe From AI attacks course and selected platform upgrades and improvements.

We are excited to announce that usecure will be exhibiting at ChannelCon 2023, hosted by CompTIA, held in Las Vegas from August...

Understand ISO 27001, its principles, structure, clauses and benefits. Learn the importance of employee data security training and...

A comprehensive guide to understanding and complying with Quebec's Law 25, covering its requirements and impacts, as well as...

This month we've released courses on AI-driven phishing attacks and deepfakes attacks, and we are taking part in two exciting...

10 days, 2 sponsors and 2 prizes per day, 4 grand prize drawings, and 30 sponsors throughout! It’s the MSP summer #ChannelDaze!
.png)
Unmasking the deceptive threat, shield your business from deepfake-powered attacks and safeguard your reputation in the age of...

Join usecure and QBS:MSP in this quick sales session that unlocks the MSP secrets for selling usecure's human risk management...
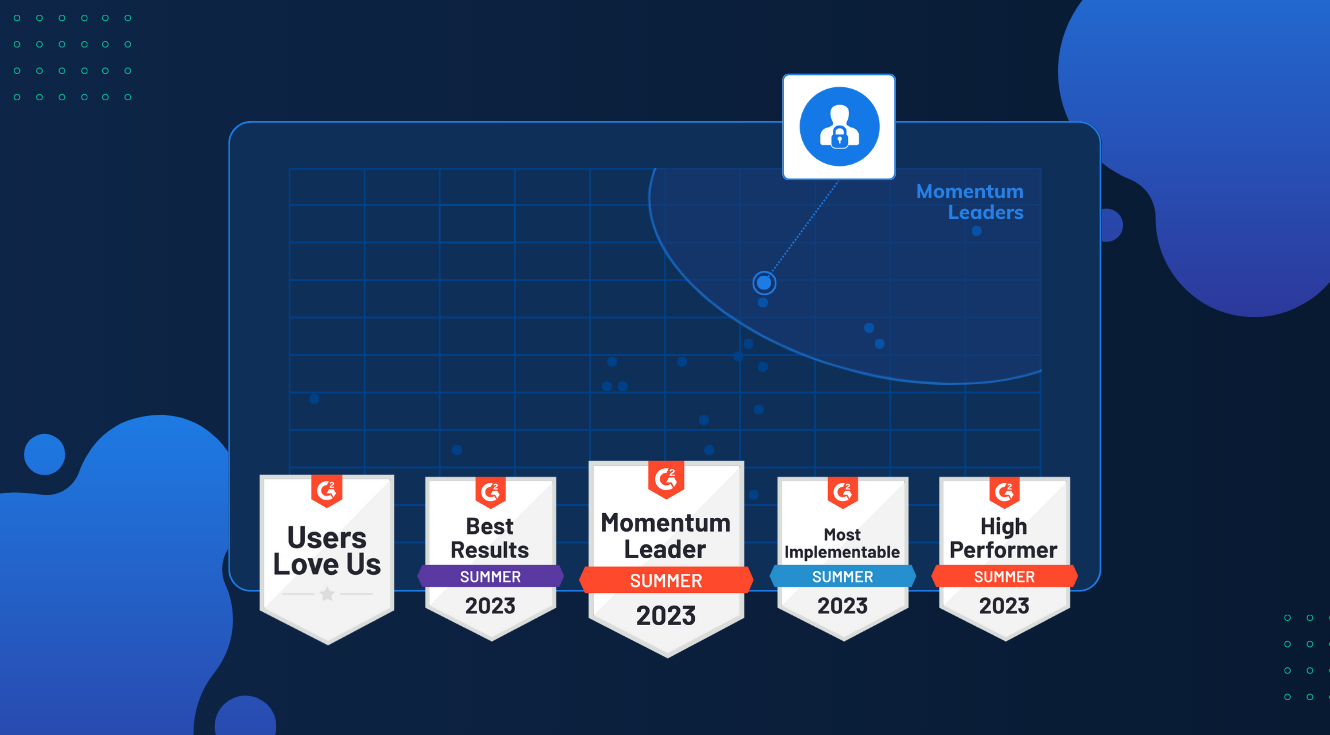
We are delighted to share that G2, the largest B2B tech review platform in the world, has awarded usecure with the Momentum Leader...

Equip your team with the essential knowledge and tools to effectively safeguard against the ever-evolving threat of AI-powered...

Here's what's new on the usecure app in June: HIPAA Privacy Rule course, and various quality-of-life improvements.
.png)
Stay ahead of the game with our useful guide to dark web monitoring in 2023. Protect your business from cybercrime and keep your...

New releases on the usecure app include a new video player for uLearn courses, a new high-risk user course on social engineering...
.png)
Protect your company's sensitive data from cybercriminals lurking on the dark web. Discover the benefits of using a dark web...
.png)
Protect your clients, elevate your cybersecurity game, and stand out from the competition! Learn why MSPs should partner with a...

Find out all that's new on the usecure platform this month.
.png)
Discover how stolen employee credentials on the dark web can harm your business, and learn practical tips to safeguard your...

Worrying about employee credentials being leaked on the Dark Web? Read this blog post to learn where you can find leaked employee...
.png)
From data breaches to illegal activities, learn how the Dark Web can harm SMBs and what SMBs can do to protect themselves.

Here's a round-up of everything new on the usecure app this month: Custom Product Names, Risk Report PDF Export, and C-Suite...

Learn about the top 10 best practices for phishing simulation and protect your organisation from cyber-attacks. Improve your...

Learn about the new features, courses, translations and platform improvements available now on the usecure app.
%20(1)-1.png)
Learn how to protect your organisation from phishing attacks with simulation training. Discover the benefits and different types...

Data Privacy Week is the perfect time for MSPs to reach out to customers about human risk management. Download your free resources...
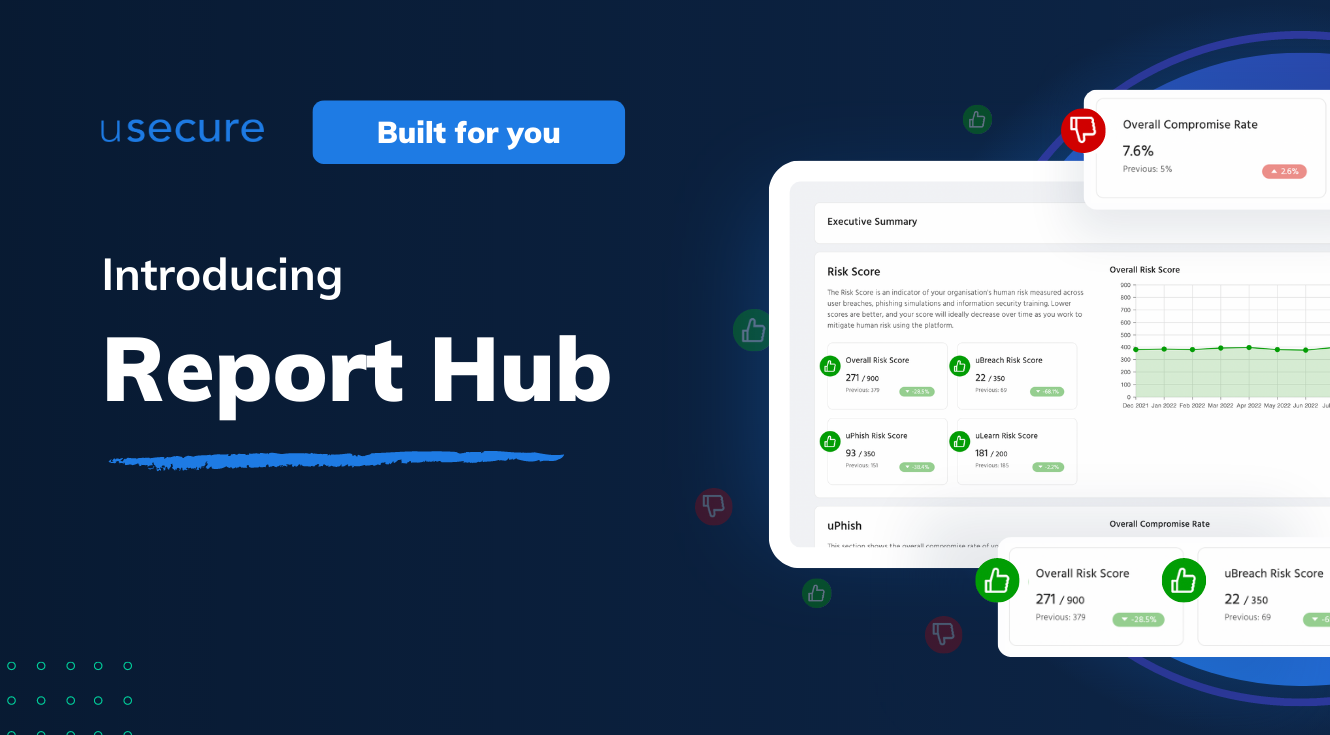
Introducing Report Hub — Get deeper insights into human risk, review areas for improvement and gain more control over stakeholder...

Hope to lower your phishing simulation cost? Get an in-depth understanding of these 4 key factors that will determine the money...

Phishing simulation is an important part of any cybersecurity programme. Having the right tips and best practices can help you...

Based on industry reports and research, we have rounded up 4 major cybersecurity threats that will significantly impact your...

Train your high-risk users with our new course on passwords and authentication, and check out the regional voiceover options now...

Evaluate the effectiveness of phishing simulations based on the latest evidence supported by scientific research and industry...

This month we've launched a new Google Workspace integration - and partnered with Channel Program to bring you an exciting review...

A step-by-step walkthrough of phishing test setups. Research-proven pro-tips for effective phishing tests and accurate employee...

Be usecure's VIP guest at CompTIA EMEACon (31st Oct-1st Nov). This £295 value is yours at no cost when you register with promo...

Join usecure at this October's Channel Pitch - the exclusive interactive livestream event where you can exert your ANONYMOUS...

Learn about the new usecure Partner Playbook, your CSAM Resource Pack, the events we'll be attending and our new G2 awards in this...
-1.gif)
A phishing simulation test is a powerful and essential tool that helps you train your employees to fight against real-life cyber...
%20(7)-1.gif)
Phishing attacks have been used to steal money and sensitive information from companies across the world. Here are the most...

A clear and actionable 7-step roadmap for implementing security awareness training. Build customised training in a time-saving and...

Learn about and add your feedback on upcoming ideas in the Product Roadmap, and assign Direct Managers to ensure line managers are...
What are the phishing statistics you need to know in 2023? In this article, we cover how phishing attacks have increased, which...

In case you missed us, here are some of the events usecure attended over the past few months, as well as some upcoming dates where...
%20(6).gif)
CEO fraud is one of the most common scams targeting end users. Here's how CEO fraud scams work - and how you can keep your...

Access expired trial accounts, restore deleted users, download all course certificates for a user and educate your clients with...
%20(10).png)
After two years of online events, ChannelCon 2022 is back in person — and we're thrilled to be announcing that usecure is taking...
%20(4).gif)
Whaling attacks pose a threat to every senior executive. Here's how to stay safe from this dangerous type of phishing email.

Here's your round-up of the most important usecure partner news for this July.
%20(3).gif)
Spear phishing emails are one of the most dangerous cyber scams. Here's how spear phishing emails are made, what they look like,...
%20(2).gif)
Phishing emails are the #1 cyber threat - here's how your business can keep itself safe with the right tools, training and...
usecure is thrilled to be recognised as a high performer in the Security Awareness Training category in G2's 2022 Summer Grid®...

We've put together our list of the 10 best phishing template examples to send to your employees, based on how common and...
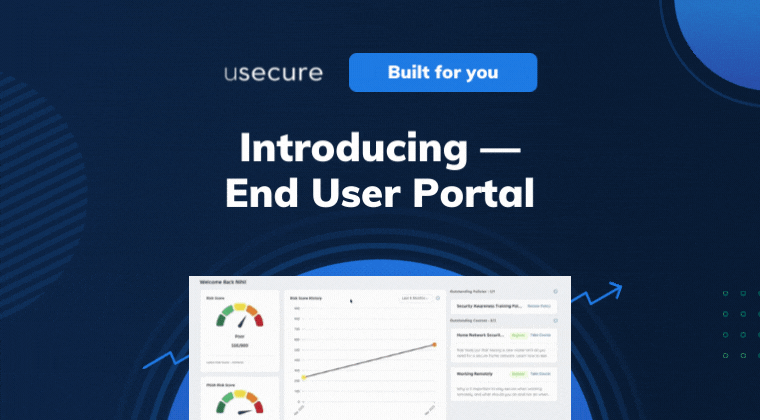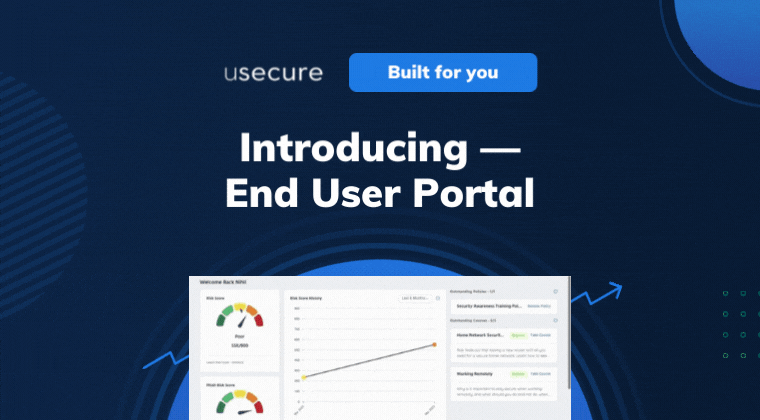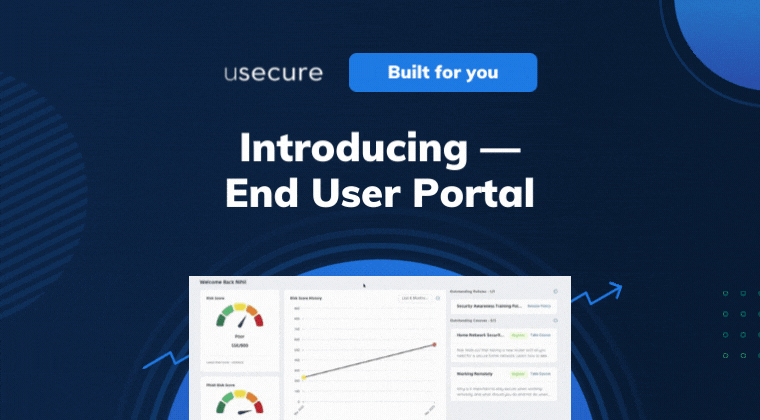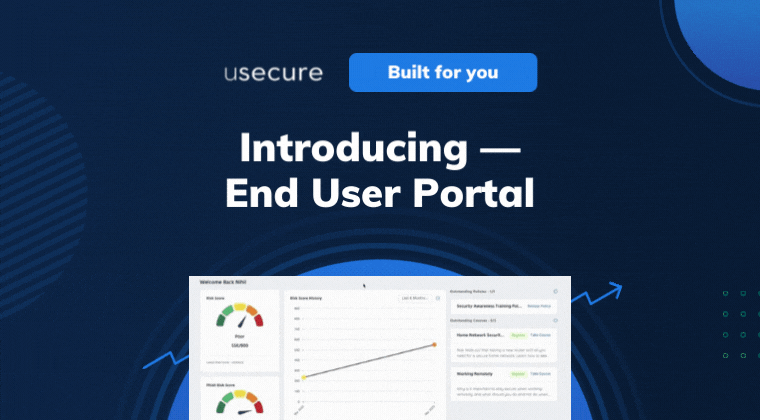
With the End User Portal, staff can understand their cybersecurity posture at any one time, as well as catch up on missed courses...

usecure is thrilled to announce that it has been recognised as a UK 'Innovative Vendor' finalist in the 2022 CompTIA Spotlight...
.png)
What are phishing emails, what do they look like, and how do you stop them? Find out all you need to know about phishing scams and...
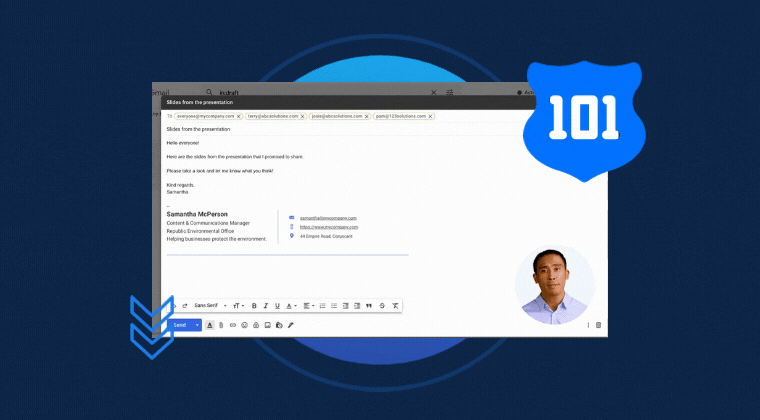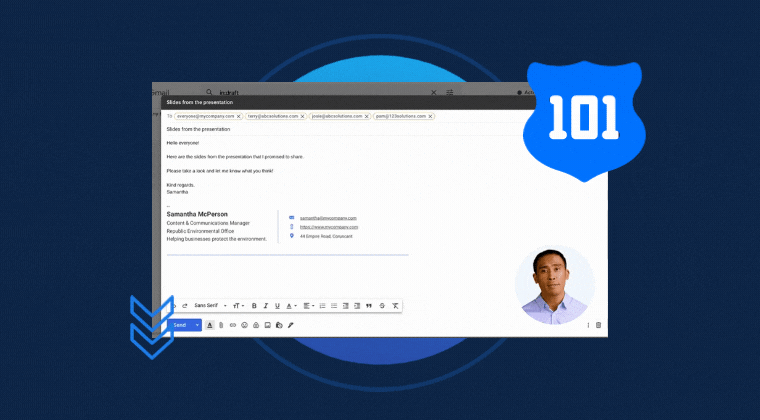
Learn what employee phishing simulations are, how they help assess and reduce human cyber risk, and how to launch your first...

Here are the main types of phishing attack that could target your business - and what your company should do to stay safe.

The latest updates to usecure include easier management of customer access in Course Builder, visibility over users' upcoming...
%20(3).png)
Andrew Atthowe from S2 Computers explains why usecure is the perfect fit for MSPs when it comes to strengthening your clients'...

Read about our new course on cyber security during the Russian invasion of Ukraine, and listen to our CEO on the next evolution of...
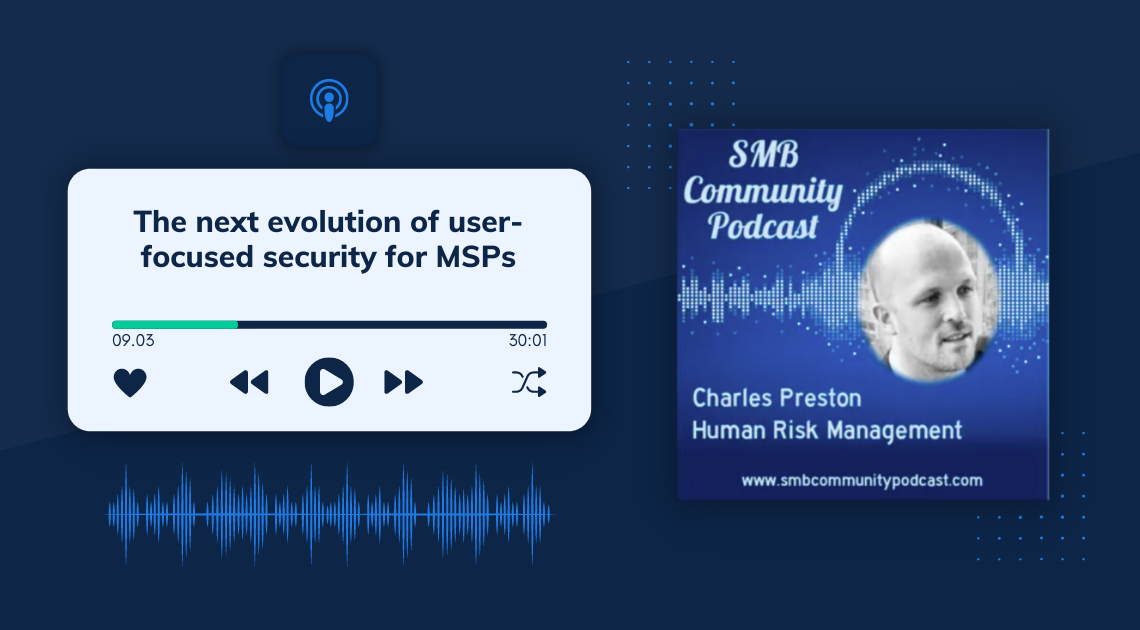
In this 30-minute chat with SMB Community Podcast, we discuss why Human Risk Management (HRM) is the next evolution of...
Following Russia’s invasion of Ukraine, security bodies across the world are advising businesses to follow more stringent cyber...

usecure has is now listed on The Tech Tribe. Grab your free Tribal Perk, exclusive for The Tech Tribe's MSP members.

Find out what's new in March: video-based Auto Enrol, VPN and Videoconferencing security courses, and a white-labelled HRM...