The 16 Billion Password Leak: What Businesses and Teams Need to Know
Brief Overview of the Incident
According to Cybernews, a newly disclosed leak has exposed over 16 billion login credentials, including data for platforms such as Apple, Google, Facebook, GitHub, and various government services across more than two dozen countries. The breach highlights how exposed human behaviour can become the entry point for major cybersecurity threats.
In this blog, we’ll cover:
More than 16 billion usernames and passwords have been leaked — not from a single hack, but from data compiled by infostealer malware that silently harvests credentials from infected devices.
Researchers discovered 30 structured datasets, each containing tens of millions to billions of records. Much of the data is recent and described as “weaponizable,” containing detailed fields like URLs, usernames, and passwords — making it highly actionable for attackers.
Potential Business and Human Impact
With billions of credentials now exposed, the risk to individuals and organizations is substantial. While investigations into specific downstream attacks are ongoing, similar breaches have historically led to the following outcomes — all of which are likely to follow here:
-
Targeted Phishing and Scam Attempts
Structured login data makes it easier for attackers to craft convincing messages that impersonate trusted brands, platforms, or colleagues — aiming to extract further credentials or install malware. -
Account Takeovers
Stolen credentials can be used to access personal or business-critical accounts, especially if multi-factor authentication isn’t enabled. -
Credential Stuffing Across Platforms
Cybercriminals commonly automate login attempts across multiple services, taking advantage of widespread password reuse. -
Business Email Compromise (BEC)
If leaked data includes corporate email addresses, attackers may attempt to impersonate staff — particularly executives — to initiate fraudulent transactions or extract sensitive data.
These risks underscore the importance of proactive user monitoring, secure authentication practices, and ongoing cyber awareness.
The Human Element of Cyber Risk
This breach reinforces a critical truth: cyber attackers exploit people, not just technology. The exposed data enables social engineering at scale:
-
Personalisation at Scale
Real names, job titles, company domains — all help attackers craft credible, targeted phishing messages. -
Password Reuse
Repeating credentials across personal and work accounts multiplies exposure from a single breach. -
Exploiting Familiarity
Attackers imitate known platforms or contacts, exploiting user trust and bypassing technical defenses.
Actionable Advice for Staying Safe
Businesses can take immediate steps to help their people stay safe — both at work and at home:
- Change Compromised Passwords Immediately
Start with known exposures. Prioritise users with access to sensitive systems, shared credentials, or admin-level privileges. - Enforce Multi-Factor Authentication (MFA)
Apply it universally — not just for apps, but also for identity providers (e.g. Microsoft 365, Google Workspace) and remote access tools. - Accelerate Passkey Adoption
Where supported, transition staff to passkeys to eliminate password-based phishing risks — especially for high-risk roles. - Deploy and Standardise Password Managers
Don’t just recommend them — roll out an approved manager across the organisation, preloaded with required credentials and MFA. - Establish a Reporting-First Culture
Make reporting suspicious messages frictionless and expected. Reinforce that it's always better to report and be wrong than stay silent. - Implement Continuous Dark Web Monitoring
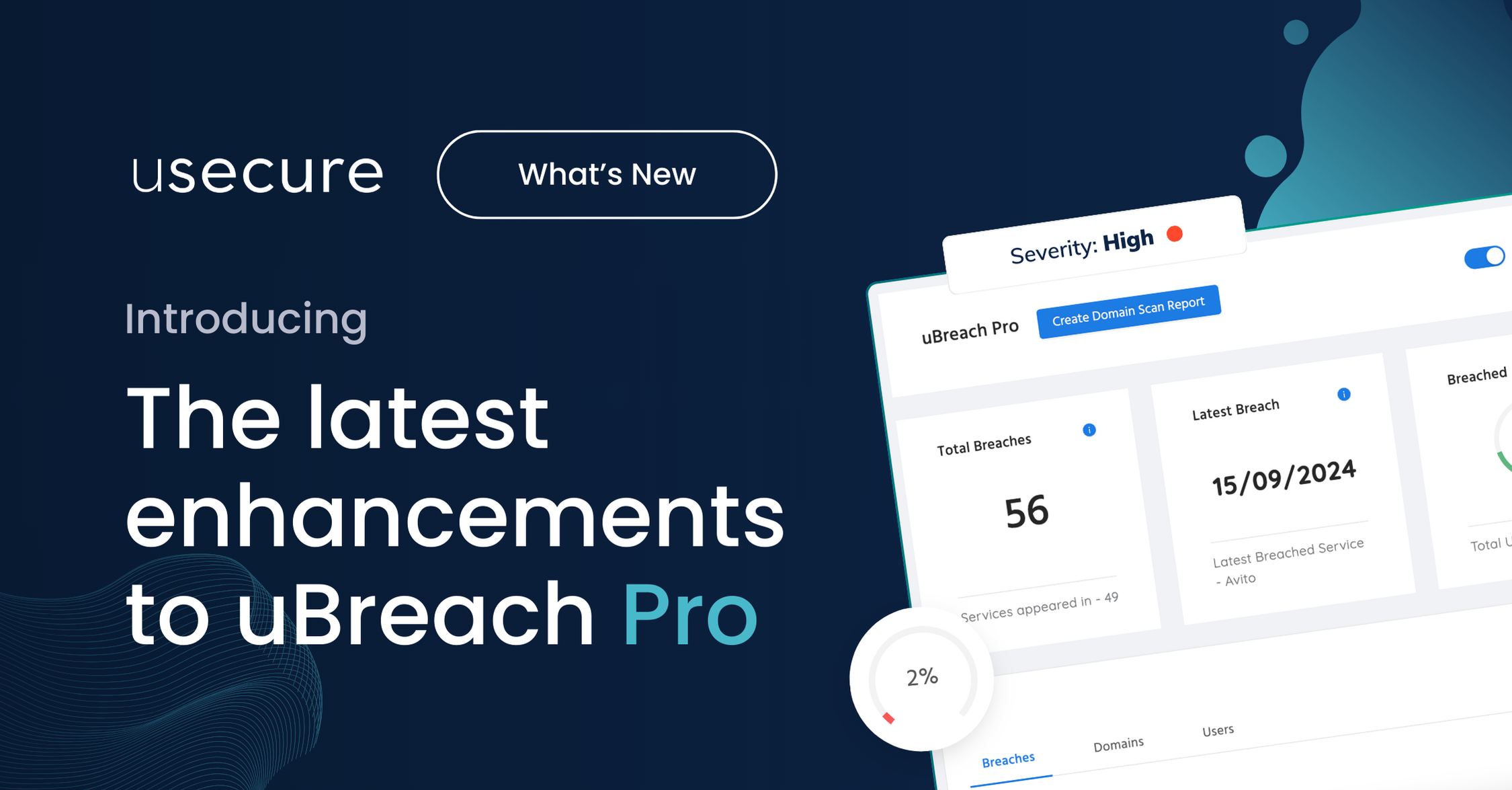
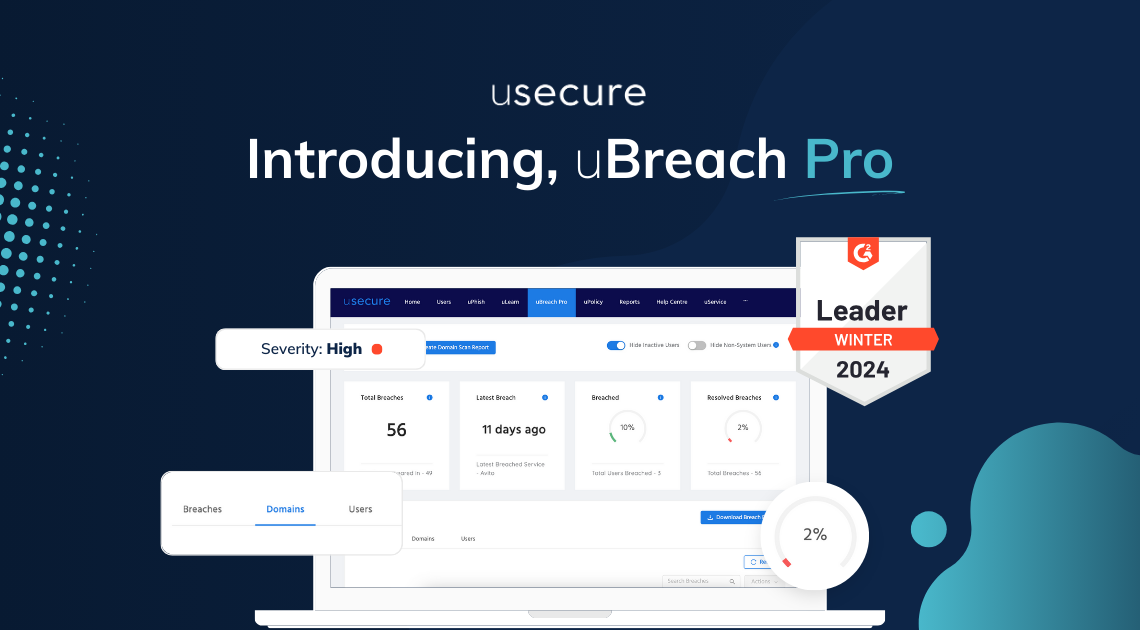
Use tools like uBreach to automatically detect when user credentials appear in fresh breach data, and link alerts directly to incident response workflows.
This breach is a clear example of how human behaviour remains the most exploited vector in cyberattacks. It’s not just IT’s responsibility — it’s everyone’s.
By empowering employees with the tools, knowledge, and visibility to stay secure in their personal lives, you reduce organisational risk, enhance incident response, and build a security-first culture that scales.
Are You Affected?
Check uBreach Now
With billions of credentials exposed, your users could already be at risk.
uBreach helps you:
✔️ Detect exposed employee data on the dark web
✔️ Alert users and admins to active breach threats
✔️ Monitor all business domains to uncover unknown risks
✔️ Demonstrate action for compliance and risk reporting
Sources: