How to run an effective phishing simulation?
Why should I deploy phishing simulations?
When the Global Risk Report 2022 published by the World Economic Forum emphasised that 95% of cybersecurity issues can be traced to human errors, we know that there's a pressing need to educate and strengthen our workforce. This article is a step-by-step walkthrough of how to set up a phishing simulation.
Step 1: Set goals for each phishing simulation
Step 2: Choose a phishing scenario and a landing page
Step 3: Craft an email to go with the landing page
Step 4: Configure phishing simulations settings
Step 5: Evaluate simulation results
Step 6: Support compromised employees
Step 7: Plan for the next phishing simulation
Set up your phishing simulation now
Step 1: Set goals for each phishing simulation
Setting goals gives you a clear direction of what to achieve in every phishing simulation. With these goals in mind, you can align your focus more easily. Goals also serve as criteria for you to judge if your phishing simulation is successful.
Goals for phishing simulations should be within a well-defined area. For example, "Improve employees’ awareness of phishing threats" may sound legit as a goal, but you won't get to know if their awareness has been truly improved, unless they report the phishing emails. Therefore, you may like to have a more specific goal like, "Increase reporting rate of phishing emails."
Step 2: Choose a phishing scenario and a landing page
Many phishing simulators allow you to choose a landing page to create a scenario. You should determine which brand you’d like to imitate and choose a corresponding landing page.
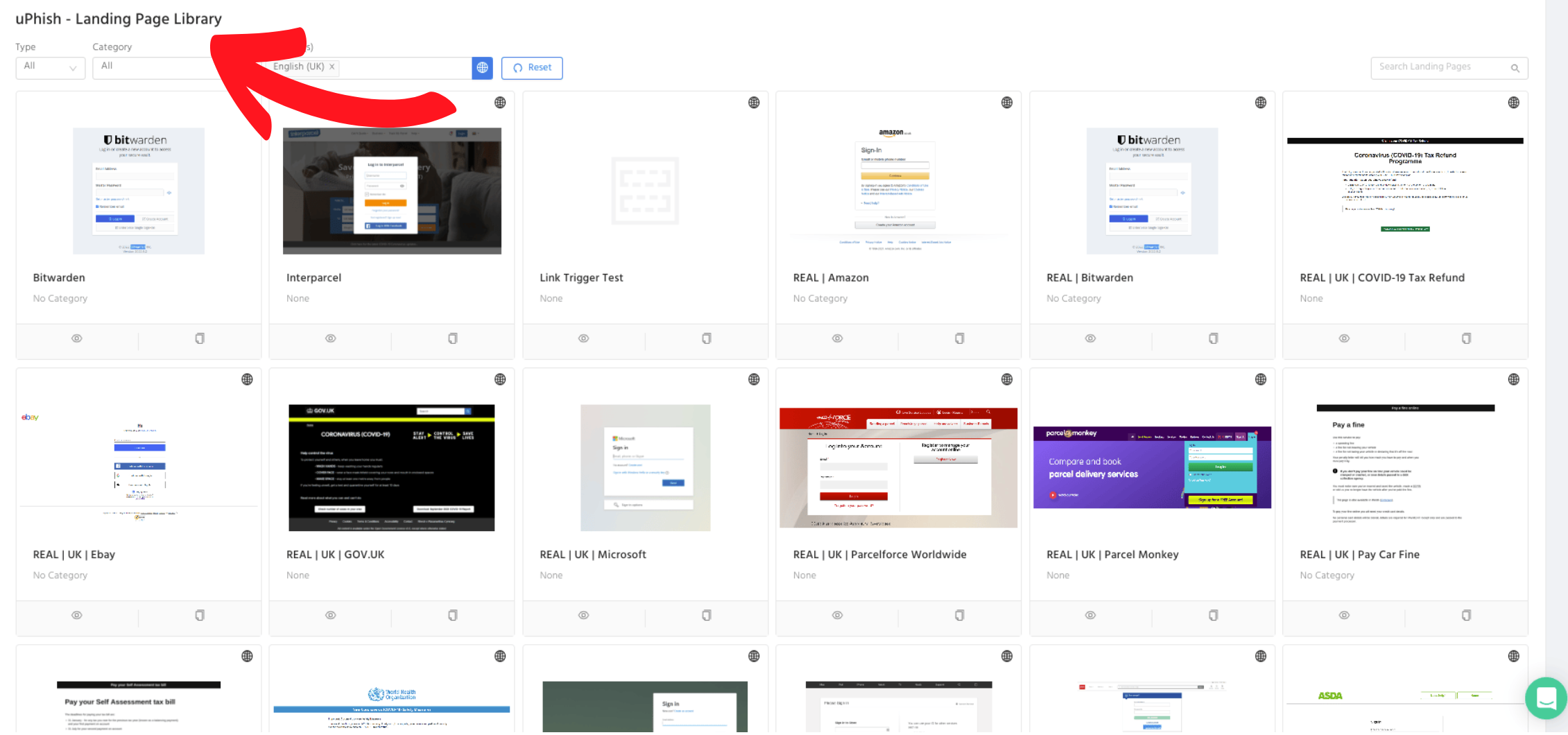
On the landing page, decide what kind of data you’d like to test your staff to compromise, such as user names and passwords. The latest Brand Phishing Report (Q3 2002) conducted by Check Point revealed that the top 10 most impersonated brands are the world’s most famous names, such as DHL, Microsoft and LinkedIn. The imitation of popular brands has done a successful job of luring employees to compromise valuable business data.
Step 3: Craft an email to go with the landing page
A nicely crafted phishing email can give your employees a real challenge. The purpose of a phishing email is to distract them from questioning the authenticity of communications. To achieve this, applying psychological triggers can be effective. A scholarly article written by psychology expert, Rennie Naidoo, suggested that urgency and trust are the two major factors that trick people into believing in scams.

“A phishing email is designed to pressure the user into a time limit or deadline.” It’s useful for you to hint at rewards for prompt actions and penalties for delayed actions. In your header, try to create urgency, and use “your final notice”, “alert” or similar phrases to push employees to take action immediately.
“Trust plays an important role in influencing cognitive and affective processes and establishing compliance behaviour. ” People tend to believe in brands that they are familiar with. You should create trust in the email. If you are imitating a famous bank, in the email content, try to use the bank's logo, font and colour scheme. This will instil your employees' trust in believing the email’s validity.
Step 4: Configure phishing simulation settings
There are hundreds of phishing simulation tools but the configuration is similar. Most of the platforms have the following settings, let’s go through this together.
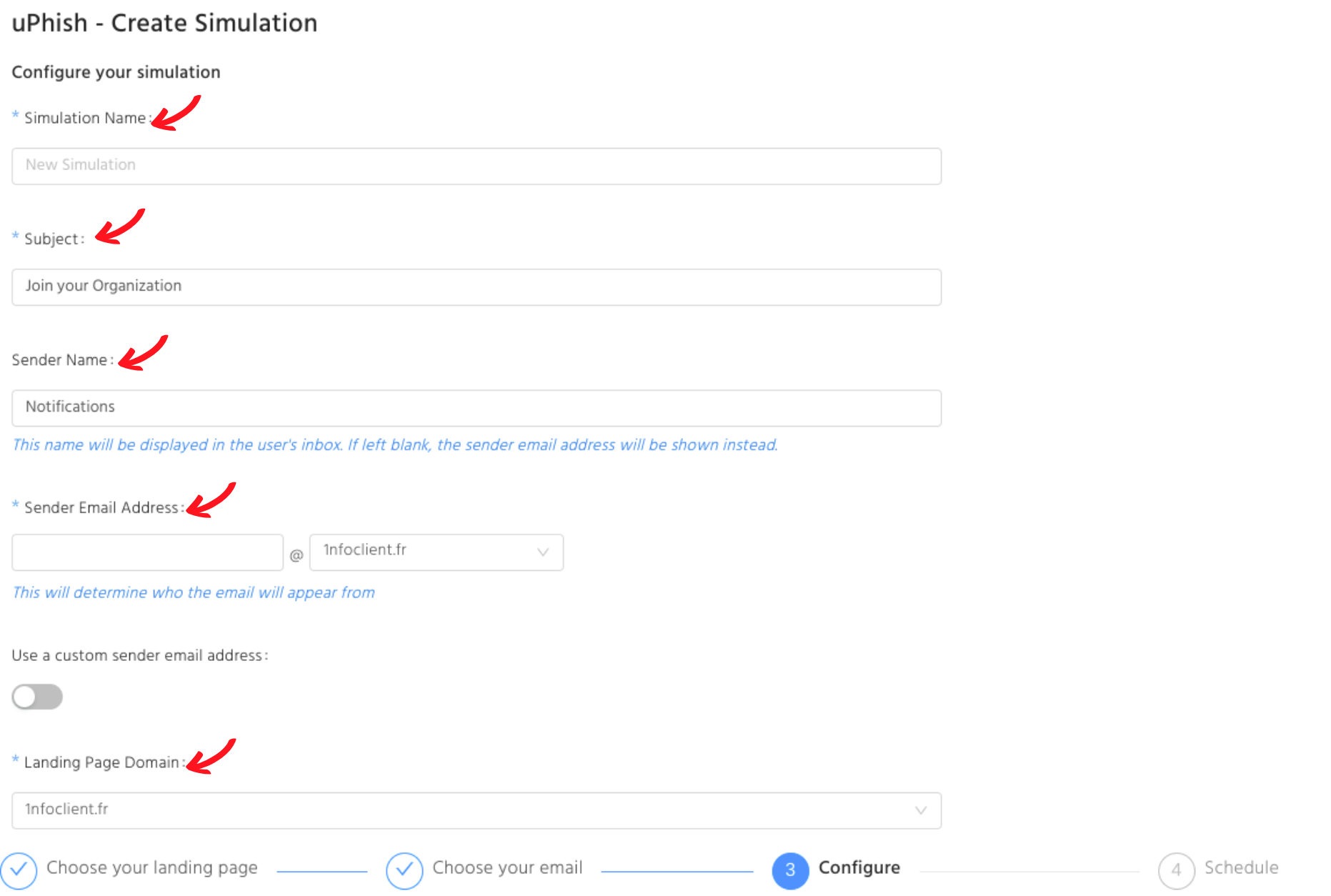
Choose your audience
Generally, you will be provided with the flexibility to choose specific departments or individuals as the simulation's recipients.
Recently, a news article published by Forbes Technology Council stated that we should offer a special care to new employees. Since these people are more likely to be targeted by criminals because they are unaware of the subtle signs that something is amiss with their communication style.
However, in order to build the strongest human defence, it’s recommended to hold every department accountable for cybersecurity.
Get other details consistent with the phishing scenario
To best mimic a brand, small details in the email, such as the landing page URL, the sender’s name and email address should appear to be consistent with the phishing scenario that you have chosen.
Naming your simulation files
Descriptive file names are an important part to keep track of phishing records. A short description, simulation theme, recipient’s name and the launch date are some elements to consider in naming your phishing simulation files.
For example: RegularPhish_DHLtheme_MarketingDept__20221026
Choose the right timing
What time of the day should you send over the phishing email? According to the findings provided by the international employment website, indeed.com, sending emails at the right time makes a difference in improving open rates, maximising click-through rates and increasing website visits.
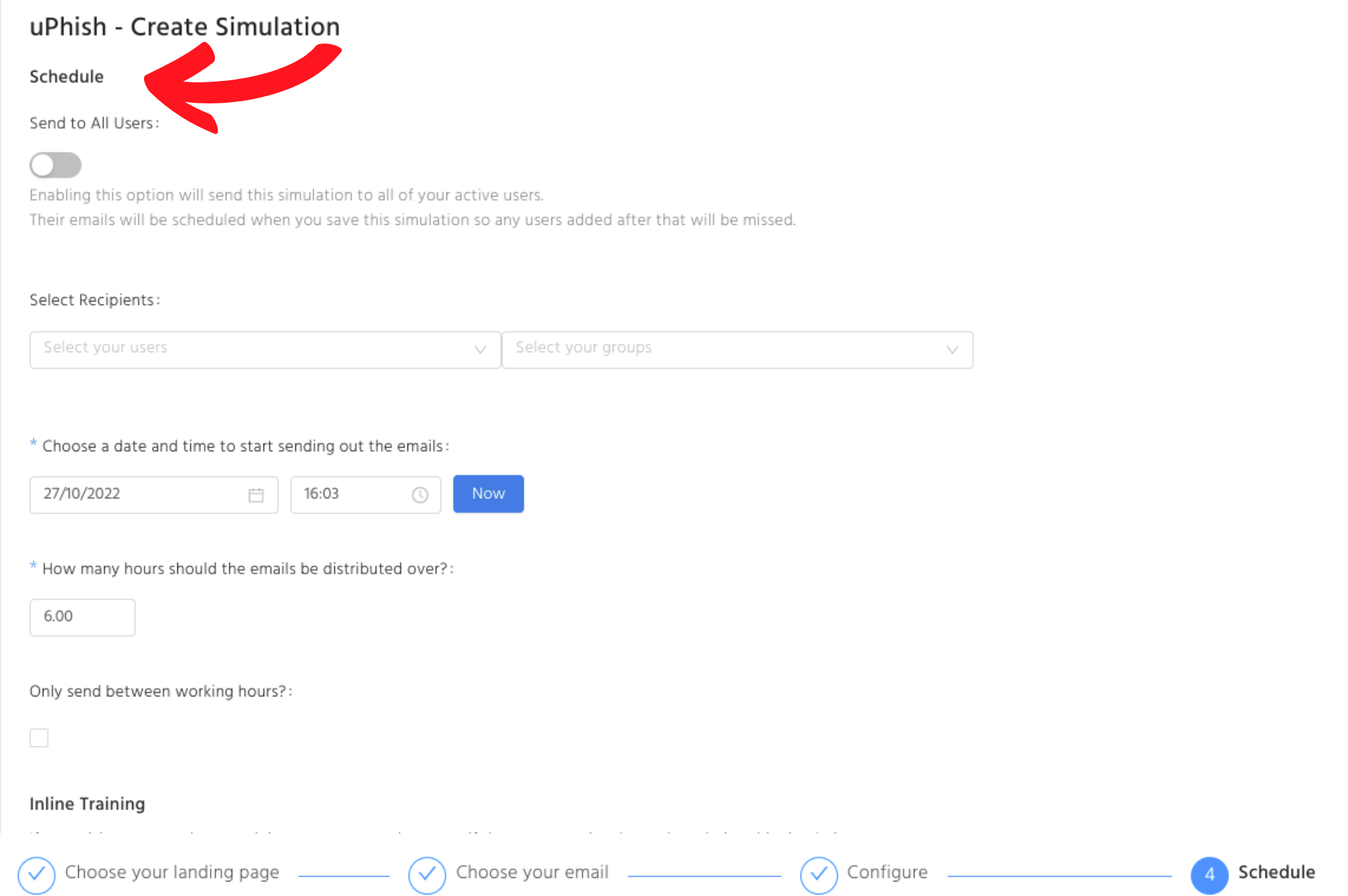
9:30 am to 10:00 am on a working day is the best time to send out your phishing emails, indeed.com suggested. As this is the time that employees are starting work and opening their messages.
Most employees get off work between 4-5 o’clock and they tend to check their emails again at the end of the day. Thus, 3:00 pm to 4:00 pm is another good time to deliver the emails.
Step 5: Evaluate simulation results
Tracking your ongoing phishing campaign results is important. As the phishing programme admin, you will receive regular updates from the phishing simulator.
Quantitative statistics, such as email open rate, click-through rate, number of compromised staff and email report rate are valuable data. Preferably, you would like to see the first 3 numbers trend down in ongoing simulations because this means your staff are getting more aware of phishing threats and avoiding interacting with these emails. For the email report rate, you would want to see it trending up because that shows your staff know the correct way to deal with phishing attempts.
Qualitative observations, such as employee sentiment, feedback and interactions with colleagues are beneficial to your company too. Although these are not data that the software can provide, it’s worth paying attention to, because they give you an all-rounded behavioural assessment.
Step 6: Support compromised employees
Prompt reaction to support the compromised employees is crucial. Most phishing simulators have an automated feature for sending immediate feedback and additional training to users who are phished. More effort should be made to help users who have repeatedly phished records. Review the emails with them, show them the red flags and indicators they missed and provide additional training materials to help them achieve success in the future.
Helping your staff in a friendly and supportive manner can largely encourage them to make a progress.
Step 7: Plan for the next phishing simulation
Learn from the phishing simulation results, educate your employees, and focus on planning the next phishing test. Keep calm and carry on, as the CISO of Groupe SEB, Stephane Nappo said, “Fix the basics, protect first what matters for your business and be ready to react properly to pertinent threats.” A continuous phishing simulation effort will empower your employees when fighting against cyber security threats.
Set up your phishing simulation now
The Business Cost of Phishing Report (October 2022) conducted by Osterman Research revealed that the dynamics of phishing attacks are changing. The ability of sophisticated phishing attempts to bypass current detection mechanisms reaches 79%. Empower your employees today, train them up and turn them into your security assets.
usecure Demo Hub
Fancy a free trial for phishing simulations? Try out our free-of-charge 14-day trial or book an on-demand demo to learn how usecure’s phishing simulation automates ongoing training and tracks your employees’ performance through meaningful metrics.