7 Simple Steps to Combat Phishing Attacks in Your Business
Learn how to protect your business from phishing attacks with 7 simple steps. Discover key strategies, industry-specific risks.
Resource Center
.png)
Learn how to protect your business from phishing attacks with 7 simple steps. Discover key strategies, industry-specific risks.
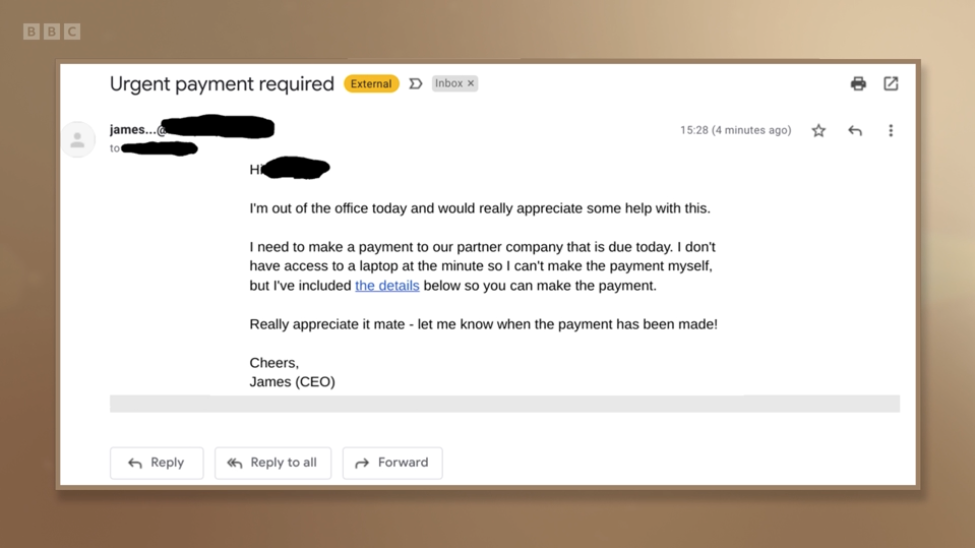
usecure was recently featured on BBC’s Morning Live during a segment dedicated to raising awareness about the growing threat of...
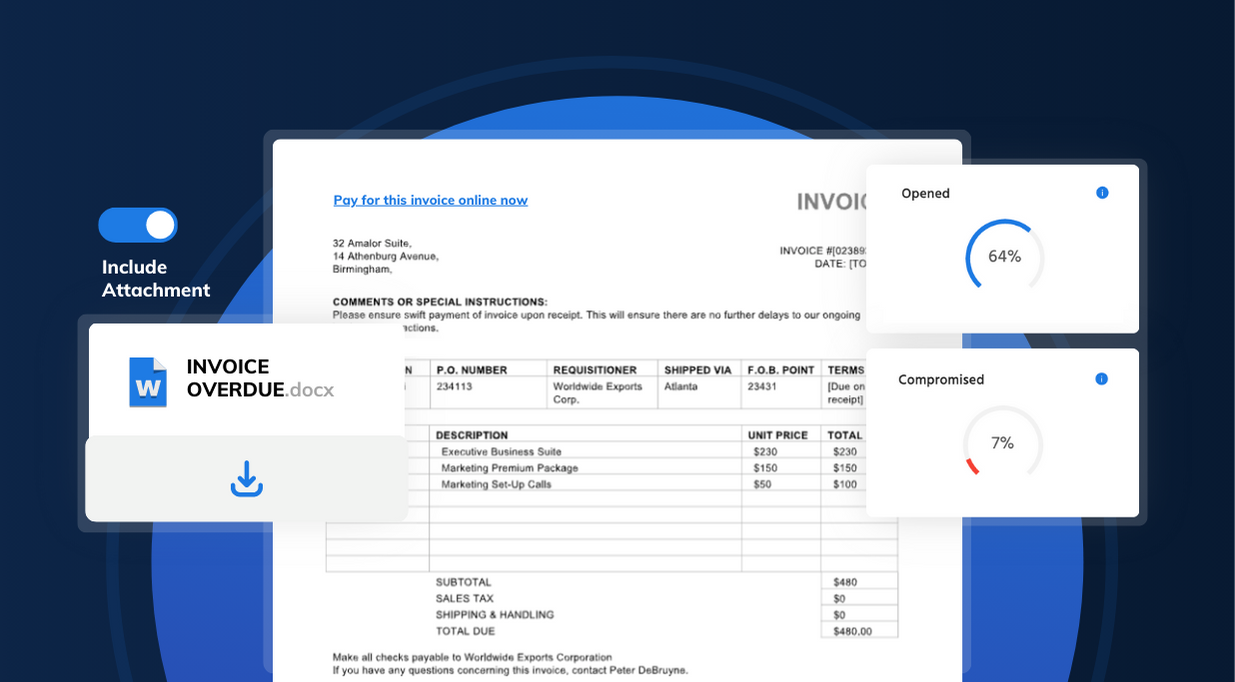
Introducing the latest update to usecure's phishing simulation feature – attachment-enabled phishing simulations in uPhish.

Discover the dangers of QR code phishing and learn how to safeguard your personal and business information.
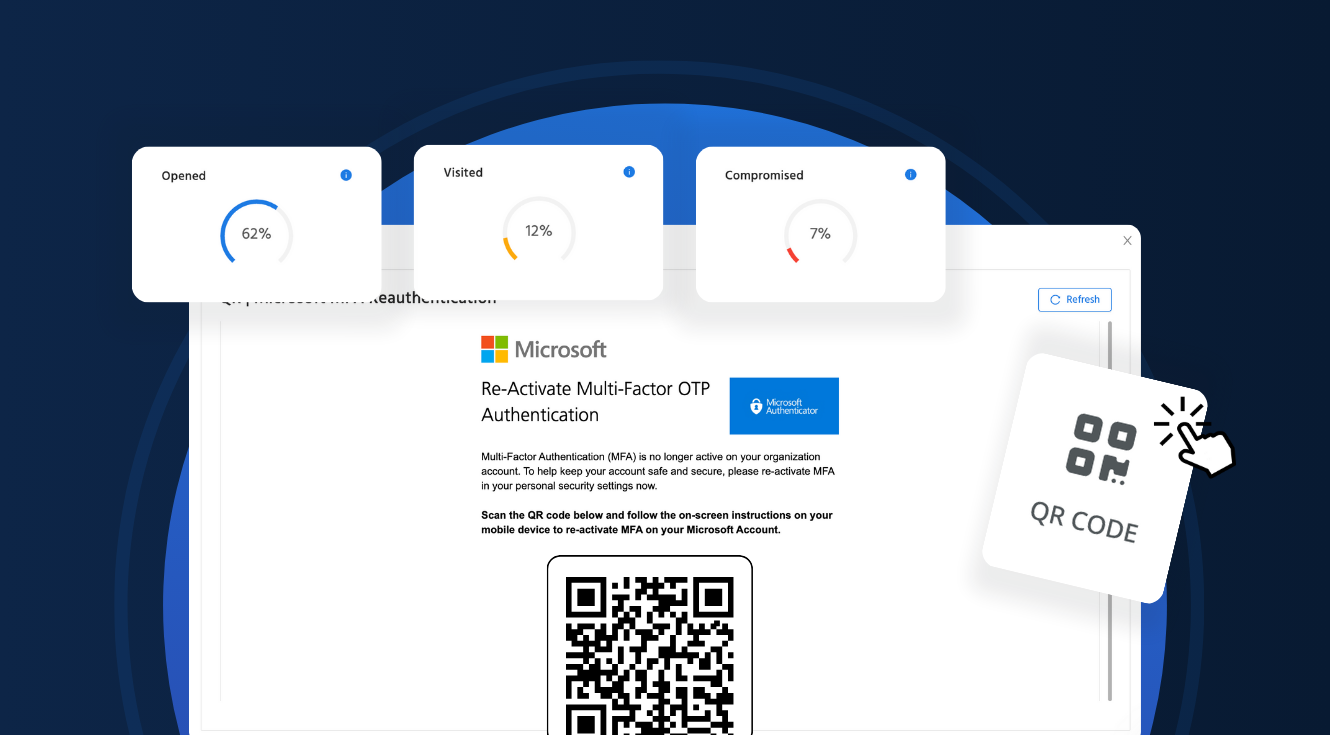
Easily embed QR codes into your usecure phishing simulations to assess employee vulnerability towards the growing threat of...
.png)
Learn what steps you can take to help your users defend their email inboxes, devices and company data from phishing scams this...

Equip your team with the essential knowledge and tools to effectively safeguard against the ever-evolving threat of AI-powered...
%20(7)-1.gif)
Phishing attacks have been used to steal money and sensitive information from companies across the world. Here are the most...
What are the phishing statistics you need to know in 2023? In this article, we cover how phishing attacks have increased, which...
%20(6).gif)
CEO fraud is one of the most common scams targeting end users. Here's how CEO fraud scams work - and how you can keep your...