The top phishing statistics to know in 2023
Cyber Crimes are one of the most prevalent, and dangerous types of threats that organisations around the world are currently facing. But how bad is the threat landscape looking?
How to recognise phishing attacks?
How to keep your business data safe?
Take a proactive approach against cyber attacks
Latest cybercrime trends
To help you stay on top of the latest trends, we’ve pulled together the most recent statistics from around the world to give you a glimpse at the breadth and seriousness of this threat and what you can do to ensure you're protected.
- Social media have become the new target for cybercriminals
Nowadays, employee phishing emails can be hyper-personalised, sophisticated, hard to detect, and surprisingly cunning for even the most security-savvy individual.
A recent report by Check Point Research (CPR) has found an emerging trend of social engineering scams shifting away from shipping companies and tech giants toward social media networks. In Q1 2022, social networks were the most targeted category, followed by shipping. - Security threats sharply increased during the pandemic
Zscaler indicated that, between January and March alone in 2020, the number of blocked suspicious messages targeting remote workers increased by 30,000% and the number of COVID-19-related spear-phishing attacks rose by 667%.
They also found that, since the outbreak, there were more than 130,000 suspicious newly registered domains (NRDs). Cyber crooks registered new domains to take advantage of words and themes associated with current events and to evade detection from reputation blocklists. - Phishing remains the most popular type of cybercrime
Among all different kinds of cyberattacks, phishing remains the biggest threat to individuals and businesses. Phishing is a type of online fraud that involves tricking people into providing sensitive information, such as passwords or credit card numbers, by masquerading as a trustworthy source.
In our increasingly technological world, phishing attacks are evolving at a quicker pace than many of us seem to realise. The days of deploying a large mass of generic and fraudulent emails to endless recipients are often being replaced with newer tactics.
According to APWG’s Phishing Activity Trends Report published in February 2022, phishing attacks hit an all-time high in 2021. With more than 300,000 attacks recorded in December, these incidents have become more than three times as common as they were less than two years ago.
Popular types of phishing
Phishing is the most common form of cybercriminal activity suffered by UK businesses and charities, according to the government’s Cyber Security Breaches Survey 2022, 83% of them have been targeted by phishing scams. Let’s look into the following 5 popular types of phishing attacks.
- Business email compromise (BEC) and email account compromise (EAC) phishing
BEC/EAC is a sophisticated scam targeting both businesses and individuals performing transfers of funds. The scam is frequently carried out when a subject compromises legitimate business email accounts through social engineering or computer intrusion techniques to conduct unauthorized transfers of funds.
BEC and EAC losses have surpassed $43 billion globally from
2016-2021
Cybercriminals have seen an incredibly high ROI. The Federal Bureau of Investigation (FBI) said in their Public Service Announcement that "business email compromise (BEC) and email account compromise (EAC) losses have surpassed $43 billion (£36 billion) globally from 2016-2021."
Their latest Internet Crime Report also showed increasing numbers of sophisticated scams targeting both businesses and individuals to perform the transfer of funds. “In 2021, the IC3 received 19,954 Business Email Compromise (BEC)/ Email Account Compromise (EAC) complaints with adjusted losses of nearly $2.4 billion (£1.99 billion).”
Obviously, the fastest and most cost-effective way of stealing money from individuals and businesses is still by using malicious but normal-looking emails. - Spear phishing
Spear phishing describes fraudulent emails sent to a particular person. Criminals have already collected some personal data of an individual, such as their name, company name, job title, email address, etc. They target victims who put personal information on the internet. They might view individual profiles while scanning a social media platform. From a profile, they will be able to find a person’s location, neighbourhood environment, friends list, email address, and any posts about new products that were recently purchased.
With the personal data on hand, the cybercriminal can address the individual by name and ask them to open a malicious attachment or click on a link that takes them to a spoofed website where they are asked to provide user names, passcodes, bank account numbers, sort codes, PIN numbers etc.
Security challenges under remote working new normal
Microsoft’s New Future of Work Report said that security threats increased during the COVID-19 crisis at Microsoft’s commercial customer organizations. The report stated that 80% of security professionals have experienced an increase in security threats since shifting to remote work. Among this 80%, 62% say that phishing attempts have increased more than any other type of threat. - Whaling phishing
A whaling attack (also known as CEO fraud) is a method used by cyber frauds to disguise as a senior player in an organization to require an employee to do them a favour, with the aim of stealing money or sensitive information or gaining access to their computer systems for criminal purposes.
Whaling emails are sophisticated, they play on employees’ willingness to follow instructions from their seniors. Recipients might suspect that something is amiss but are afraid of confronting the sender.
"Whaling attacks using executive impersonations in Q1 2021 have increased by 131% from Q1 2020", according to the email security company GreatHorn. Their report also suggested that "59% of organizations say an executive has been targeted for whaling attacks and 46% of these executives have fallen victim to these attacks." Targeted executives also received whaling emails once every 24 days.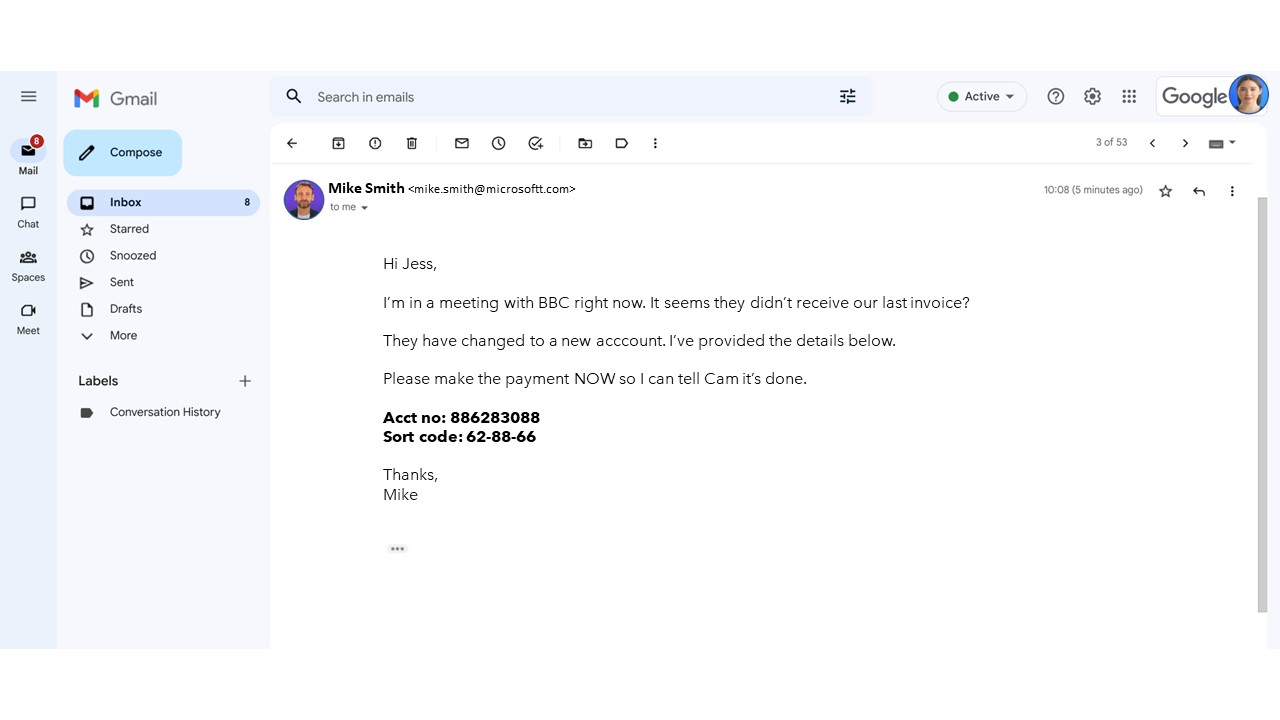
- Disguising documents and hyperlinks
The old cyber criminal's favourite of disguising malicious email attachments as invoices remains the most popular tactic for luring users into opening the bait. Other tactics that have cropped up heavily in recent years include disguising attachments sent as scanned documents from office printers, email delivery failure messages, order and payment confirmations, highly specific flight confirmations, and even a fake HMRC tax refund hyperlink. - Impersonated brand phishing
Brand impersonation is an attack that impersonates a trusted company, a brand, or a domain to trick victims into responding and disclosing personal or otherwise sensitive information.
The first quarter of 2022 saw a dramatic increase in phishing attacks. Cybersecurity vendor, CheckPoint revealed in their 2022 Q1 Brand Phishing Report that phishing attacks impersonating the professional social networking site made up over half (52%) of all attempts globally in the first quarter of 2022. This represents a 44% increase compared to the previous quarter, Q4 2021 when LinkedIn was the fifth most impersonated brand.
"Following LinkedIn, the most frequently impersonated brands in phishing attacks were DHL (14%), Google (7%), Microsoft (6%), FedEx (6%), WhatsApp (4%), Amazon (2%), Maersk (1%), AliExpress (0.8%) and Apple (0.8%)."
CPR suggested, “Employees, in particular, should be trained to spot suspicious anomalies...” Educating the staff to fight against cyber crooks is now top of mind for senior IT practitioners and the good news is, we’ve got what you need to help you stay away from the cyber risks. With our proactive solution – uPhish, you will be able to assess your employees’ vulnerability; get help in determining appropriate training to provide, thereby preventing security breaches for your company.
How to recognise phishing attacks
Sometimes, it can be hard to know for sure if you’ve received a phishing email. Especially when you come across professional-looking, well-written emails that seem like they are sent from companies you know and trust. However, as long as you exercise caution, and look out for the following telltale signs, you are likely to avoid falling victim to these scams.
Poorly written emails
One of the most common signs of scam emails is poor spelling and grammatical mistakes. Most organizations have the spell-check feature turned on for outbound emails. Thus, it’s unlikely to see emails originating from a professional source contain bad spelling or incorrect use of grammar.
Emails sent from a public email domain
Another simple way to identify a potential phishing attack is to look for discrepancies in email addresses, links, and domain names. Most businesses have their own email domain and company accounts. Watch out, if the domain names don’t match the business’s name.
Emails include suspicious links or attachments
All attachments should be opened with caution. If the attachment has an extension commonly associated with malware downloads or has an unfamiliar extension, it may be a red flag. Remember to always virus-scan attachments before opening them.
Messages with a sense of urgency
More often than not, malicious emails threaten negative consequences; or utilise urgency to encourage immediate actions. Readers might not examine the content thoroughly and a phishing operation may pass undetected.
How to keep your business data safe?
According to the government’s Cyber Security Breaches Survey 2022:
● 82% of senior management rate cyber security as a ‘very high’ or ‘fairly high’ priority, an increase of 77% in 2021.
● 72% of charities rate cyber security as a ‘very high’ or ‘fairly high priority'.
● 50% of businesses and 42% of charities say they update the board on cybersecurity matters at least quarterly.
Security awareness training
Phishing reports and statistics are beyond a warning sign of just how serious and prevalent phishing campaigns are. Training and educating employees on the risks of phishing attacks and how to spot the telltale signs are proven ways of lowering the threat.
One of the most effective ways of seeing how susceptible your end users are is with simulated phishing campaigns. For more information on how important it is to raise awareness of phishing scams, give our free phishing simulation trial a go.
Take a proactive approach against cyber attacks
Usecure’s powerful anti-phishing product – uPhish, enables organisations to deploy mock-phishing attacks on their employees to help the business understand their staff’s vulnerability and what types of relevant training should be provided.
The admins who are responsible for deploying these simulated phishing campaigns are able to use readily-made email phishing templates. uPhish comes packed with an extensive library of pre-made templates, allowing you to quickly deploy realistic campaigns with ease. You're also able to choose which templates you would like to exclude (both custom or pre-made), what groups of users you would like to exclude, and whether users should only receive simulations during work hours.
Try uPhish now before weaponised emails reach your employees!

.png)