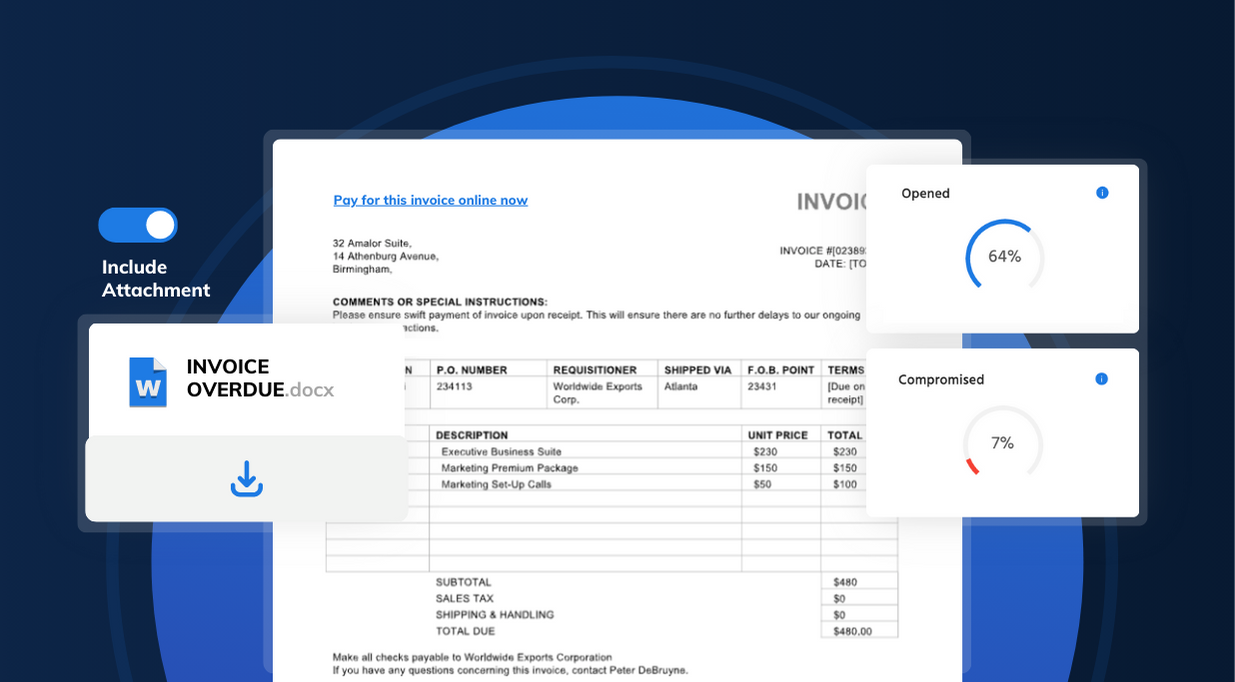
The Three Stages Of a Phishing Attack - Bait, Hook And Catch
Spear phishing is the most dangerous form of phishing. Unlike generic, template-based attacks, spear phishing involves finding out information about the target in order to customise the phishing message to make it more likely to work
A spear phishing attack begins with the cyber criminal finding information about the target, then using that target to build a connection, and thirdly using that connection to make the target perform an action. Read on to learn more about the bait, hook and catch: the three stages of a spear phishing attack.
Step 1: The Information (Bait)
The first of the three steps of a phishing attack is preparing the bait. This involves finding out details about the target, which can be as simple as knowing that they use a particular service or work at a particular business. This is one of the reasons why data breaches where no ‘sensitive’ information is compromised can be so dangerous: if a service leaks a list of just email addresses of its users, criminals will be able to know that all the owners of those email addresses use that service and can target them with emails that pretend to be from that service.
In more sophisticated spear phishing attacks, cyber criminals can harvest details from your social media profiles in order to build a highly customised spear phishing message that is highly likely to convince you of its genuineness.
Step 2: The Promise (Hook)
Once the attacker has acquired the necessary information to use as bait, they then need to lay out the hook. In order to actually make the target perform an action, the attacker needs to promise something or scare them into action.
In many scams the hook involves making the target believe that one of their accounts have been compromised, creating a sense of urgency and making the target act quickly - perhaps without thinking. The attacker can then redirect the target to follow a link to a page where they can harvest the victim’s details.
Step 3: The Attack (Catch)
The third phase of phishing is the actual attack. The cyber criminal sends out the email, and prepares for the prey to fall for the bait.
What the attacker’s next action will be will depend on the nature of the scam. For example, if they used a landing page to gain the victim’s email password, they can then log in to the victim’s email account in order to harvest more information and start sending further phishing emails to the victim’s contacts.
Learn how usecure helps businesses drive secure behaviour with intelligently-automated cyber security awareness training.
How can I defend my organisation against phishing attacks?
To protect your business from phishing, it is essential to understand the threat. Why would someone target your business? What data do you hold that’s valuable? What financial transactions do you perform that a cyber criminal could try to get their hands on with a forged invoice?
1. 2 Factor Authentication
Multi-factor authentication is absolutely essential for protecting your accounts against phishing. It adds a second line of defence, meaning that even if you fall for a phishing attack and give away your email password, you’ll still be able to stop the attacker from accessing your account.
2. Security Awareness Training
As phishing can be carried out in so many different ways, there isn’t a simple technical solution that would be able to stop it. Humans will always be the risk factor when it comes to phishing. This is why training is absolutely essential.
Your employees should be taught how to look out for the signs of phishing, and that they should always exercise extra care when following links from unexpected emails. Enrolling your users on security awareness training courses, will help mitigate the threat of phishing emails.
3. Simulated Phishing
While employee training is essential, phishing simulation allows you to see how your employees perform when faced with a real-world scenario. Simulations allows your employees to see how easy it is to fall for a phishing email, and is highly effective at raising awareness as employees are far more likely to remember falling for a simulated phishing email than they would simply taking a training course.
Simulate phishing attacks and test your employees
Learn how to perform a realistic phishing simulation and test your company's vulnerability to phishing attempts in a real-world scenario.