Employee Phishing Simulations 101 — Why, how and when to run them
From dodgy email attachments claiming to be an invoice that you’ve already paid, to "password expired" messages directing towards a strange login page, businesses are targeted with endless types of phishing attacks on a daily basis, ranging from the downright obvious to the surprisingly authentic.
With employees being 40% more likely to encounter a phishing scam since 2021, now is a good time for decision-makers to assess and strengthen staff awareness by ‘phishing their own pond’ through internal attack simulations — but how exactly do these work?
Whether you're debating the idea of running an internal phishing campaign or scratching your head on how to get started, this post will give you a quick beginner's guide on:
- What a phishing simulation is
- Why phishing simulations are so important
- How phishing simulations work
- The best practices for launching a simulation
- How to get started without breaking the bank
What is a phishing simulation?
A phishing simulation — otherwise known as a phishing test — is where a fake malicious email is sent by an organisation to their own staff in order to assess their response to a real-world phishing attack.
For example, an organisation might be concerned about the increase of fake Microsoft emails arriving in their employees’ email inboxes, so decides to run quarterly phishing simulation campaigns in order to identify which users are susceptible to these types of attacks and are in need of additional phishing awareness training.
-2.png?width=760&name=Untitled%20design%20(33)-2.png)
Want to better understand how helpful phishing simulations can be to your organisation? Check out another article here, we've pulled together industry research and reports, to let you know why phishing simulations have become a trusted and popular way to protect your business data.
Why are phishing simulations important?
There is a common misconception that phishing is easy to spot and that only less technically-savvy people will fall victim — but this is far from the truth. In fact, more than 80% of reported cyber incidents are tied to phishing attacks, most of which are delivered through email.
Almost 20% of all employees are likely to click on phishing email links and, of those, 67.5% will enter their credentials on a phishing website.
In order to combat these threats, staff need to understand the telltale signs of an attack, the common techniques criminals use and what to do when they believe they’ve received a phish. Check out the Top 4 Phishing Simulation Threats for 2023 to keep pace with the current cybersecurity trends. Phishing simulations help employees achieve that by training them to recognise, avoid and report potential threats.
How do phishing simulations work?
Phishing simulations are often launched as part of a wider human risk management approach and are administered periodically using different techniques and messaging. In most cases, the simulation is administered by the business’s IT team, and run as follows:
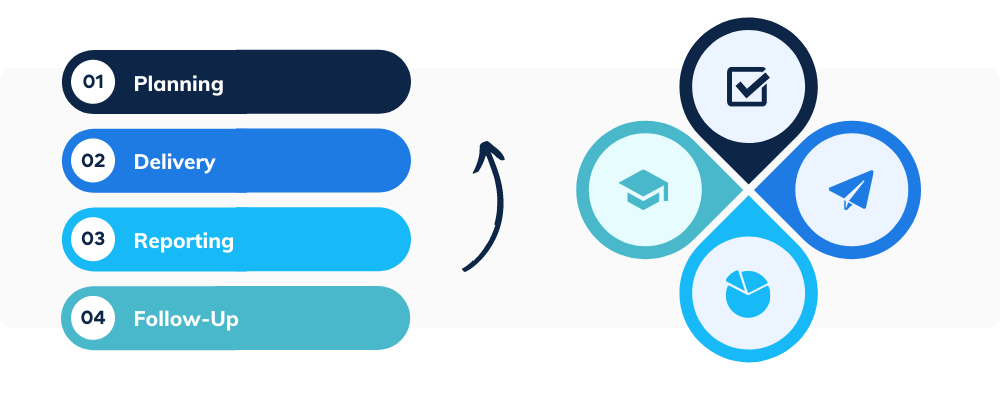
- Planning — Before launching any phishing simulations, the body of the campaign is outlined by the administrators, including which staff will be targeted, how often and which techniques and templates will be used.
- Delivery — Employees are then sent their first simulated phishing email, which might purport to be from a colleague who is perhaps chasing an unpaid invoice, or an email service provider claiming that their password is due to expire and needs urgent action.
- Results — The simulation tracks whether the employees engage with the email, usually by tracking whether the user clicked the ‘dangerous’ link or downloaded the ‘harmful’ attachment, as well as who reported the email.
- Follow-up — If the user does click the link or download the attachment, they’re directed to a landing page that breaks the news and explains which telltale signs they missed, often through a follow-up training session.
Need a step-by-step walkthrough of how to set up an effective phishing simulation? Check out our blog post here.
Best practices for running a phishing campaign?
A phishing campaign needs to accurately emulate the tactics and techniques that are used by real attackers, using hooks that will have the most emotional impact on the target. Real phishers use a bunch of different tricks to dupe people, but most attacks revolve around:
- Fear — e.g. having an account deactivated unless you reset your password
- Anxiety — e.g being asked to make an urgent wire transfer by the CEO
- Reward — e.g. entering a prize draw to win additional annual leave
- Hope — e.g. downloading an attachment to see who won that quarterly incentive
As well as using the right tactics in your messages, it's even more important to make sure that there is a well thought out approach for planning, delivering and tracking the ongoing simulations.
Here are the core best practices to follow at each stage of your campaign: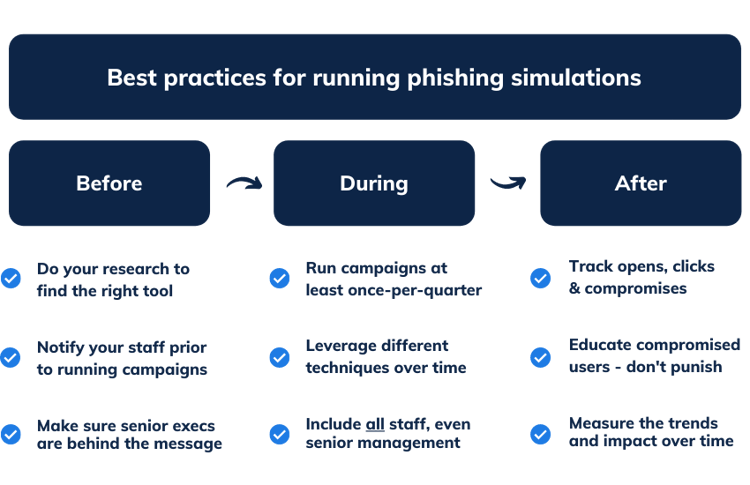
Before the simulation
Find the right tool
There is a seemingly neverending list of phishing tools out there, from open source to proprietary, to simple-to-use vs highly advanced. It’s important to find the right fit for your business by answering questions about budget, requirements, integrations, as well as by reading peer reviews and forums.
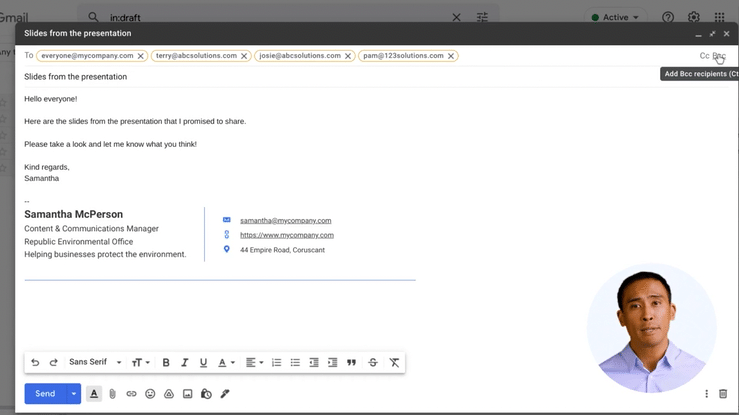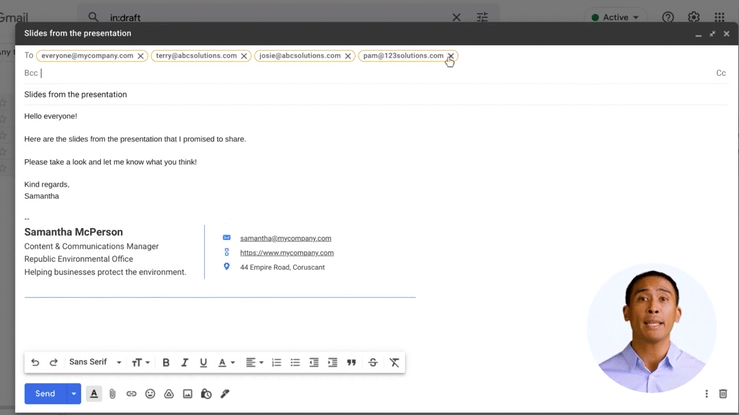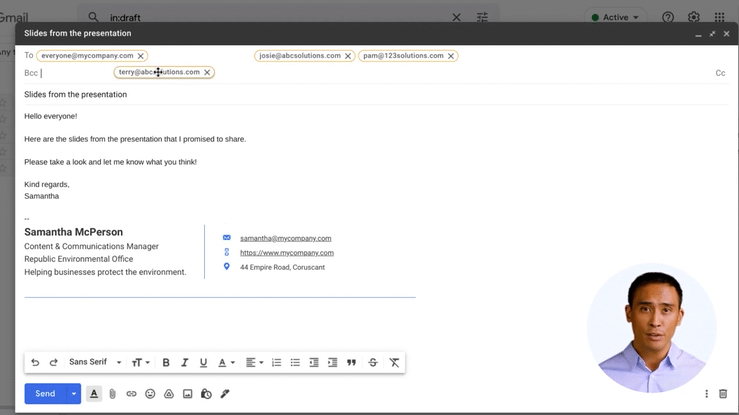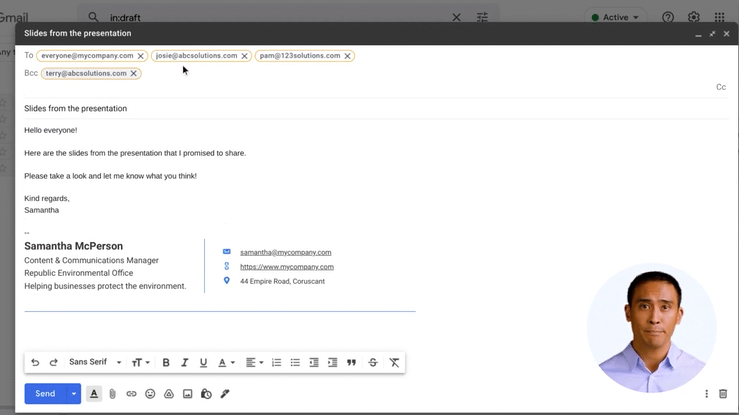
After all, many of the tools out there might look similar, but there are key differences that can make or break the impact of your campaigns and the accuracy of your results. We suggest finding a phishing tool that nails these basics:
- Is easy-to-use — Good security shouldn't mean sacrificing productivity. Try to find a tool with no installations, good functionality and helpful support docs.
- Has pre-loaded templates — The last thing anyone wants is to be researching a rabbit hole of phishing templates or battling with a drag and drop editor.
- Is automated — Simulations should be ongoing to help monitor human risk, so having a hands-off way of running these tests will help prevent a drop-off.
- Has great reporting — You'll need a way of understanding how phishing risk has changed over time, along with insights into user segments and trends.
There are plenty of independent review websites out there, such as Capterra, that can help you dig down into what the best threat simulators are.
Notify your staff
Deploying phishing simulations without first explaining to your staff why the business is looking to run these campaigns can be a surefire way of creating an ‘us VS them’ mentality between senior management and the wider business.
It’s important to explain why these efforts help keep the company, its employees and its customers safe, otherwise, people might feel caught out for doing something wrong, rather than finding value in learning from their mistakes in order to avoid falling victim.
Have managers from each department notify their teams on why these campaigns are being run, how they work and where to report suspective phishing attempts, and implement ways of having open conversations with staff about these types of threats on dedicated channels, such as Slack or Teams.
Get buy-in from the top
If you want employees to really get behind the value of running internal phishing simulations, then a clear and consistent message needs to come from the top down. After all, combatting phishing attacks isn't just a problem for the IT folks, it's the responsibility of everybody within the business.
Making sure that executives and managers of each department fully understand the aim of these simulations and know how to deliver a consistent message to their teams will truly help towards embedding a cyber security culture, rather than creating a new function that might just end up lost amongst the noise.
During a simulation campaign
Keep them going
Phishing simulations should be run in an ongoing campaign format in order to help you gauge early-stage risk and then, over time, measure how successful your efforts have been in reducing susceptibility to these threats. Running ongoing simulations also helps monitor risk amongst the userbase, which is especially important among new starters.
Try to make sure each member of staff is receiving a phishing simulation at least once per quarter to help track risk while keeping education at a high, without going into overkill and annoying people.
Keep them guessing
Real-world attackers are constantly using new techniques to scam people, so it’s important to keep employees on their toes by leveraging whatever common or trending techniques are out there.
Let’s take the fake invoice phishing scam, for example — this is one of the most common types of attacks out there that employees should certainly be tested on at some point, but cyber criminals also leverage topical news, like breaches and pandemics, to dupe people in new and unsuspecting ways.
Test employees with different types of messages and social engineering techniques to get a true reflection of risk while giving them full training on attacks they could potentially run into.
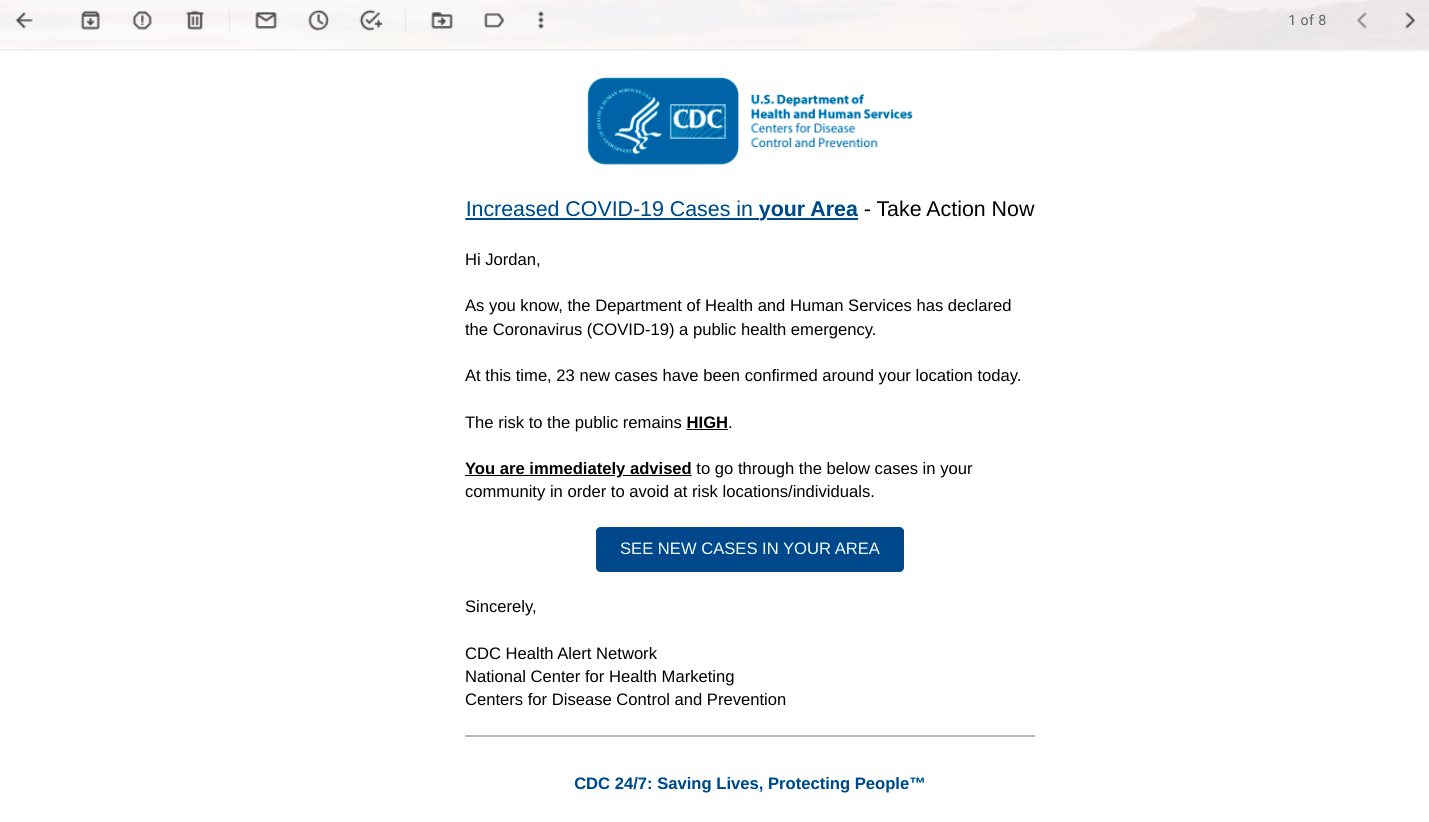
Below is an example of a trending phishing attack, taken from usecure's uPhish simulator, which replicated a highly popular scam during the height of the COVID-19 pandemic where cyber criminals were impersonating health organisations.
Keep everybody involved
Senior management often holds the keys to the kingdom and can be the most frequent target in many cases, so it’s vital to make sure they’re tested in just the same way as the wider organisation.
Whaling (otherwise known as CEO fraud), for example, is a highly targeted phishing attack that is aimed at senior executives, often with the aim of gaining access to sensitive data or getting high-value wire transfers approved.
Keeping senior management involved will also support your message that this is a company-wide responsibility, regardless of department, role or seniority.
After a simulation
Track the essentials
After each simulation, it’s important to look at the key performance metrics to make sure that you’re aware of where the risk is increasing or decreasing across the organisation.
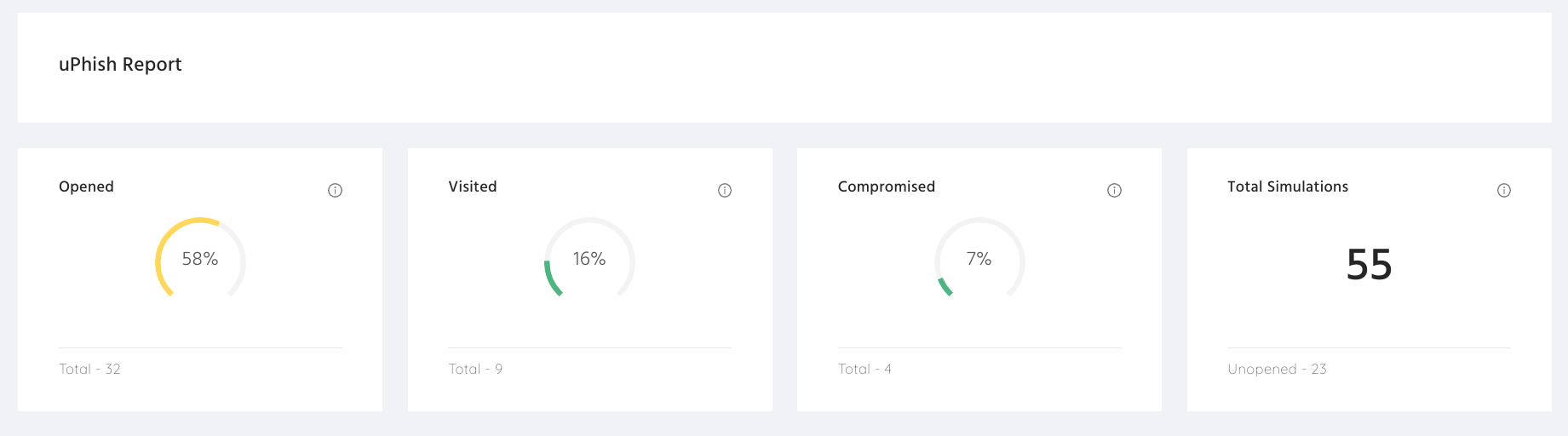
The dashboard above shows the typical metrics that are tracked during a phishing simulation, including:
- Open rate — How many people opened the simulated phishing email
- Click rate — How many people clicked a link in the phishing email
- Comprise rate — How many people either gave away their credentials (e.g. on a fake sign-in page purporting to be their email provider) or how many downloaded the ‘harmful’ attachment that could have contained ransomware (e.g. a fake invoice)
It's also a good idea to track the report rate of simulations — i.e. how many people reported the phishing email — in order to identify and reward those who demonstrate good security behaviour.
Educate and reward - don’t punish!
During your early phishing campaigns, it’s highly likely that at least some users will become compromised, with some businesses even seeing more than one-third of their staff take the bait in an early phish.
It’s important to set the tone by handling these types of results in a way that doesn’t invoke fear or irritation amongst staff and, instead, sparks an opportunity for people to strengthen their phishing radar and aim for progress.
Do’s
- Provide additional training to users who become compromised
- Reward users who regularly report simulated (and real) phishing emails
- Share overall company results with the rest of the organisation
Dont’s
- Don’t punish users who fail a phishing simulation
- Don’t single out a specific user or department who fails a simulation
- Don’t neglect users who fail a simulation — train them!
- Don’t share the results of specific users
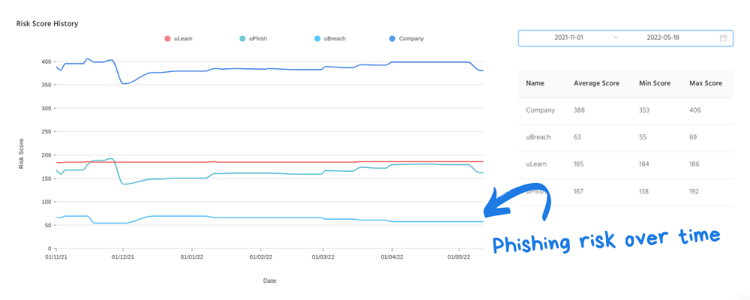
Measure the impact over time
Spotting trends and measuring ongoing results is essential for determining whether or not phishing awareness is improving. This should involve comparing results from multiple campaigns over time to see how many users are being compromised in simulations compared to previous months.
How to get started
Finding the right phishing tool can be a challenge and can often be a stumbling block for why companies end up delaying their campaign, which then puts the business at risk of falling for a real attack in the meantime.
With usecure's uPhish simulator, you're able to:
- Launch phishing campaigns in minutes without any installations
- Save countless hours with readily-made phishing templates
- Easily track which users are at risk with a real-time reporting dashboard