The Market Trends MSPs Can’t Afford to Ignore in 2025
In the last year, conversations around cybersecurity have taken a sharp turn — it’s no longer just about basic protection but more about human risk mitigation, regulatory readiness and proof of security maturity — and MSPs are expected to lead the change.
At recent enablement sessions, we’ve been hammering home one simple message: MSPs can no longer afford to be passive on security; they need to lead. And the latest article from ChannelWeb confirms it: the market is shifting, fast!
In this blog, we’ll break down three of the most pressing trends shaping the future of cybersecurity — and how MSPs should respond to them.
Topics covered in this blog:
- Trend 1: The Increasing Risk of Human Errors
- High-Profile Cybersecurity Incidents in 2025 Caused by Human Errors
- MSP Strategy to Reduce Human Cyber Risk for Clients - Trend 2: The Rise of Toughening Cyber Rules Worldwide
- Most Common Cyber Regulatory Requirements Globally
- Key Security Solutions MSPs Should Look For - Trend 3: Clients Are Demanding Proof of Credibility from Cybersecurity Vendors
- Three Essential Criteria for Vetting Cybersecurity Vendors
Trend 1: The Increasing Risk of Human Errors
The majority of breaches today stem from human behaviour — whether it’s a misdirected email, a weak password, or a click on a phishing link.
According to Proofpoint’s 2024 Voice of the CISO report, 74% of chief information security officers (CISOs) identified human error as their leading cybersecurity concern—marking a notable increase from 60% the previous year. Supporting this, Mimecast’s State of Human Risk Report revealed that human error plays a role in 95% of data breaches, highlighting its critical impact on organisational security.
High-Profile Cybersecurity Incidents in 2025 Caused by Human Errors
While statistics point to human error as a leading cause of cyber breaches, real-world incidents drive the point home with far greater impact. In the first half of 2025 alone, a wave of high-profile breaches across industries has already rattled global enterprises.
| Organisations/ Incidents | Sectors | Human Errors | Consequences |
| Marks & Spencer (M&S) | Retail | Third-party vendor targeted via phishing | £300M profit hit, £750M market cap loss |
| Aflac | Insurance | Employees tricked by social engineers posing as tech support | Compromise of sensitive customer and health data |
| Qantas Airways | Aviation | Call centre error | 5.7 million customer records breached |
| Coinbase | Crypto | Insider bribed to grant access | Internal data exfiltrated, ransomware demands, company’s shares down >6% the next morning |
| Cartier | Retail | Credential stuffing due to reused passwords | Customer emails, addresses, and history exposed |
| WestJet & Hawaiian Airlines | Aviation | Help desk manipulation | FBI alert, potential compromise under investigation |
| Long Island School Districts | Education | Staff fell for phishing & fake login sites | 10K+ student records revealed |
| Texas Digestive Disease Consultants | Healthcare | Unsecured server exposed via employee misconfiguration | Approx. 205K patient records exposed |
| Los Angeles County | Government | Employee clicked phishing link in inbox | Multiple systems encrypted by ransomware |
| Cyber-Espionage Targeting Taiwan Semiconductors | Semiconductor manufacturing | Cyber-espionage by spear‑phishing and credential theft at suppliers | Up to 20 compromised organizations, espionage activities across supply chain |
MSP Strategy to Reduce Human Cyber Risk for Clients
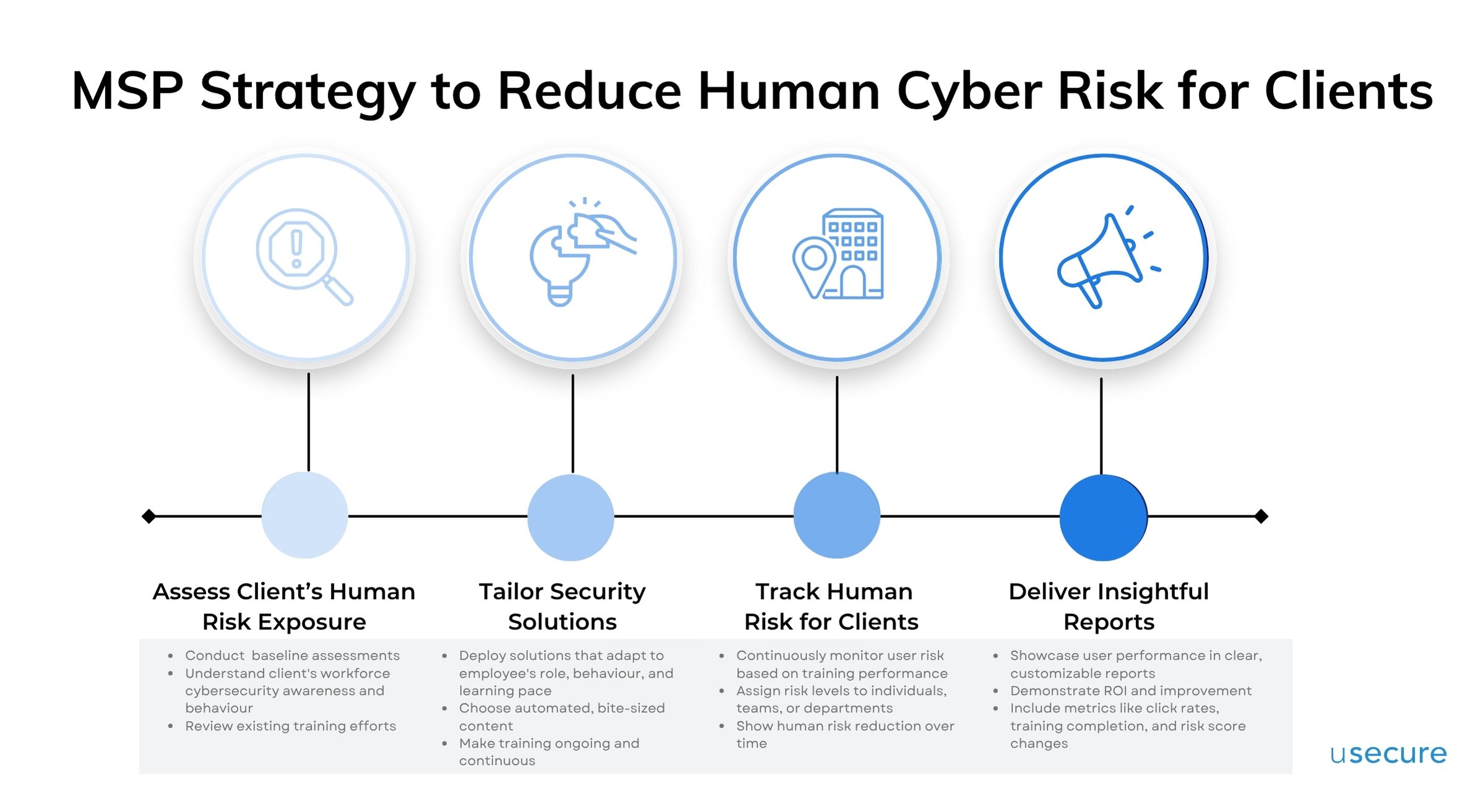
Human error remains one of the leading causes of breaches — and clients know it. Clients aren’t just looking for antivirus and patch management anymore — they’re asking: "Is our workforce adequately trained to serve as a strong defence against security threats?" They're looking to their MSPs for support in managing this risk.
MSPs should build a portfolio of solutions to address human-related cyber risks in all aspects. Follow these strategic steps to develop a client-centric human risk management offering:
Start by conducting a baseline assessment to understand where the client's workforce stands in terms of cybersecurity awareness and behaviour. Review existing training efforts, if any.
2. Deploy Tailored Security Solutions
Once gaps are identified, deploy a user-centric solution that adapts to the employee's role, behaviour, and learning pace. It is important to choose a platform that offers automated, bite-sized content to maximize engagement. To drive real behavioural change, make training ongoing and continuous. Consistency is key to building lasting security habits across the workforce.
3. Track Human Risk for Clients Continuously
Adopt a solution that enables continuous monitoring of user risk based on their training performance. Assign risk levels to individuals, teams, or departments. Share reports with clients that clearly show risk reduction over time. Use these insights to guide future training and intervention.
4. Deliver Insightful Reports
Showcase the results of user performance in clear, customizable reports that demonstrate ROI and improvement. Include metrics like click rates, training completion, and risk score changes. Use these reports as a conversation starter during QBRs and client reviews.
Trend 2: The Rise of Toughening Cyber Rules Worldwide
Across the globe, cybersecurity regulations are becoming stricter, broader, and more enforceable. Governments are no longer treating cyber risk as a purely technical issue — they now expect organisations to demonstrate accountability, resilience, and proactive defence. From the EU’s NIS 2 Directive and GDPR enforcement to the US’s CIRCIA and sector-specific mandates like HIPAA and PCI DSS v4.0, compliance requirements are expanding rapidly.
Most Common Cyber Regulatory Requirements Globally
Many of the cybersecurity laws, frameworks and standards now include people-focused requirements designed to reduce human risk and demonstrate proactive security management. Below are some of the most common regulatory expectations MSPs and their clients must meet:
-
- Security Awareness Training
Most regulations mandate that organisations provide regular, role-based security awareness training for all employees. This ensures users understand common threats like phishing, ransomware, and data mishandling.Strongly required by NIS 2 (Article 20(1)), GDPR (Article 39(1)(b)), HIPAA (§164.308(a)(5)), PCI DSS v4.0 (Requirement 12.6), ISO 27001 (Annex A 6.3), DORA (Article 5 Section 2(g), Cyber Essentials (Requirement 4) and NIST CSF 2.0 (Identify).
- Security Awareness Training
-
-
Phishing Preparedness and Simulation
Strongly required by NIS 2 (Article 21 (2)(g)), PCI DSS v4.0 (Requirement 5.4), ISO 27001 (Annex A 6.3), Cyber Essentials (Requirement 5), NIST CSF 2.0 (Detect). Many laws and frameworks emphasise the need to simulate cyber attacks to evaluate and improve user readiness — especially against phishing, one of the most common attack vectors.
-
-
-
Policy Management and User Acknowledgement
Strongly required by GDPR (Article 33), HIPAA (45 CFR §§ 164.400-414), CIRCIA (Cyber Incident Reporting Requirements), ISO 27001 (Annex A 6.8) and NIST CSF 2.0 (Protect). Organisations are expected to have clear policies (e.g. Acceptable Use, Data Handling, Remote Work) and ensure users read and acknowledge them. Lack of policy awareness is a compliance red flag.
- Breach Detection and Credential Monitoring
Cybersecurity laws increasingly demand that organisations detect and respond to breaches swiftly. Monitoring for exposed credentials is a proactive way to reduce the risk of unauthorised access and demonstrate incident readinessStrongly required by GDPR (Article 33), HIPAA (45 CFR §§ 164.400-414), CIRCIA (Cyber Incident Reporting Requirements), ISO 27001 (Annex A 6.8) and NIST CSF 2.0 (Protect).
-
Key Security Solutions MSPs Should Look For

MSPs, increasingly seen as extensions of their clients’ security and compliance operations, must stay on top of legal requirements and deliver compliance-ready, people-focused solutions that align with these tightening standards.
-
- Role-specific, engaging training modules that overcome the forgetting curve, featuring automated delivery, completion tracking, and exportable reports to support audit requirements.
- Automated phishing simulations with real-time monitoring of click-through and reporting rates to measure and improve user resilience over time.
- Automated policy distribution coupled with acknowledgement tracking, ensuring audit-ready records of user acceptance and up-to-date policy management.
- Regular scans for compromised user credentials associated with client domains, providing timely alerts that enable MSPs to take swift action and prevent account takeovers.
The toughening cyber rules create both a challenge and a growth opportunity. MSPs who embed compliance into their services will stand out as strategic partners in this high-stakes environment.
Trend 3: Clients Are Demanding Proof of Credibility from Cybersecurity Vendors
Nowadays, clients are no longer content with verbal assurances or glossy product sheets — they want proof. They want concrete proof that the solutions in place are secure, compliant, and of a high standard.
According to a recent CyberSmart survey of 900 MSP leaders, 77% of MSPs said that they're experiencing increased scrutiny of their own businesses’ security capabilities — meaning that MSPs need to choose their cybersecurity partners carefully.
For MSPs, it’s not enough to say your stack is secure; you must demonstrate that you’ve made deliberate, vetted choices about the vendors you use.
Three Essential Criteria for Vetting Cybersecurity Vendors

To meet your clients’ expectations and regulatory obligations, here’s how you can confidently select solution vendors that meet today’s security and reliability standards:
1. Prioritise Vendors with Recognised Cybersecurity Certifications
When clients demand assurance, third-party validation speaks volumes. Choose vendors who hold credible certifications such as Cyber Essentials, Cyber Essentials Plus, ISO 27001, SMB1001, etc. These certifications demonstrate a proactive and audited commitment to information security, helping you align with cybersecurity laws globally. Partnering with certified vendors gives your clients confidence in your security posture — and helps protect your own business too.
2. Vet Vendors for Long-Term Viability and Financial Stability
Too many cybersecurity solutions burn bright and fade fast. To ensure your investment pays off, choose vendors who are financially secure and actively growing. Look for partners with a solid financial footing and a clear trajectory for growth. Indicators such as recent funding rounds, consistent revenue growth, and strategic expansions are strong signs of long-term viability.
3. Look for a Consistent Track Record of Product Development
Cyber threats evolve and so should your vendors. Select partners who consistently enhance their platform with meaningful upgrades, new features, bug fixes or UI tweaks. Proactive development shows a vendor’s commitment in continuous improvement. It’s about building a platform that grows with your business and adapts to your clients’ evolving security needs.
From Passive Provider to Proactive Partner
With the second half of 2025 already underway, one thing is clear: the cybersecurity threats and expectations are advancing quickly. MSPs can no longer afford to be reactive in their approach to risk mitigation. The good news? These challenges also present massive opportunities. MSPs who embrace their role as proactive partners — offering human-centric solutions, compliance-aligned services, and evidence-backed credibility — will set themselves apart in a crowded market.
The market has spoken, and the MSPs who listen will thrive. Get in touch with us today to enjoy a 14-day free trial of our products or access a library of on-demand demos to experience the modern way to reduce human cyber risk, meet evolving compliance standards, and prove your value as a proactive security partner.


