The ultimate guide to dark web monitoring 2024
Dark web monitoring is a critical component of any holistic cybersecurity strategy, but with the constantly evolving nature of the dark web, it can be difficult to know where to begin.
In this year's ultimate guide to dark web monitoring, we'll provide a comprehensive overview of the dark web, the monitoring techniques, and actionable steps you can take to safeguard your digital assets.
Whether you're a small business owner or a cybersecurity professional, this guide will equip you with the knowledge you need to stay ahead of the threats posed by the dark web.
In this blog, we'll cover:
- What is dark web monitoring?
- Is dark web monitoring worth it?
- What are “compromised credentials”?
- Types of compromised credentials found through dark web monitoring
- What are the benefits of using a dark web monitoring service?
- What are the consequences of ignoring dark web monitoring?
- How do dark web monitoring tools work?
- What makes the best dark web monitoring tool?
- How to choose the best dark web monitoring vendor?
- 5 steps to implement dark web monitoring
- Get the right tool to protect your business data
What is dark web monitoring?
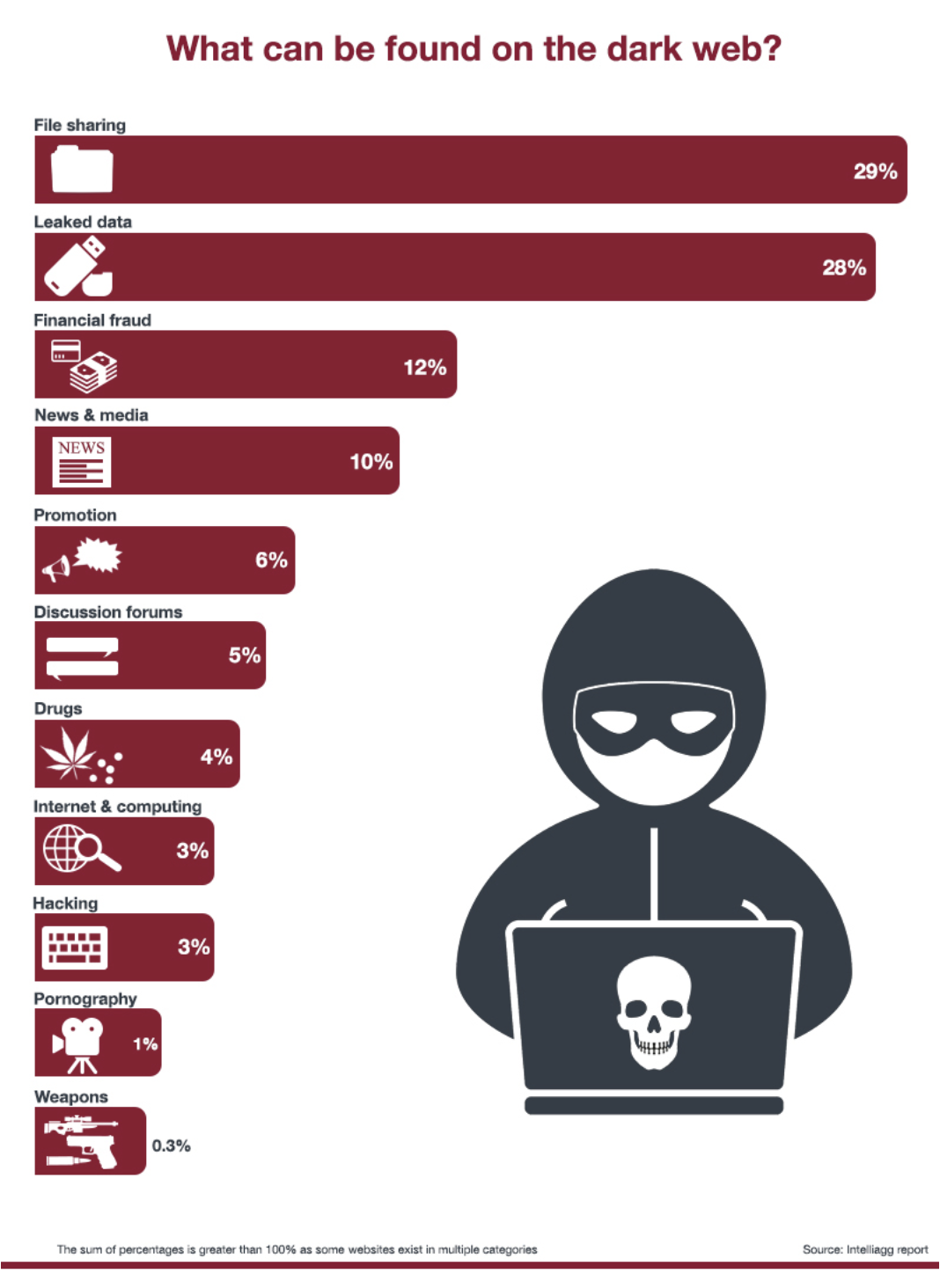
The dark web is a haven for criminals who seek to exploit vulnerabilities and steal sensitive information from unsuspecting victims. According to Intelliagg report, These are the most common types of criminal activities found on the dark web.
Dark web monitoring refers to the process of monitoring the dark web, which is a part of the internet that is not accessible through traditional search engines or web browsers.
Dark web monitoring involves using specialised browsers with specific configurations to search for and analyse data on the dark web. This can include monitoring for particular keywords or phrases related to a company or individual, such as login credentials, financial information, or personal data. The goal of dark web monitoring is to identify potential threats and vulnerabilities before they can be exploited by cybercriminals.
The use of dark web monitoring has been increasingly on the rise in recent years due to the growing risks posed by the dark web. Therefore, it is anticipated that a larger number of companies will incorporate dark web monitoring as an integral part of their overall security strategy to safeguard against potential threats.
Is dark web monitoring worth it?
The cost of a dark web monitoring service varies depending on the provider you choose and the level of service you require. However, the cost of a data breach can be significant - the average cost of a security incident is $3.86 million, according to a 2020 study by the IBM Security Team.
Check Point Research (CPR) has reported an increase in discussions on dark web forums concerning the unauthorised sharing or sale of compromised premium accounts for ChatGPT over the past month. These are what they found regarding the situation:
- Leak and free publication of credentials to ChatGPT accounts
- Trade of premium ChatGPT accounts that were stolen
- Bruteforcing and Checkers tools for ChatGPT – tools that allow cybercriminals to hack into ChatGPT accounts by running huge lists of email addresses and passwords, trying to guess the right combination to access existing accounts.
- ChatGPT Accounts as a Service – dedicated service that offers opening ChatGPT premium accounts, most likely using stolen payment cards.
When you thought your company's data was safe and sound, the ChatGPT data leak came along to shatter that illusion. It's a stark reminder that the most unexpected data breaches can and do happen. Just consider the potential cost of a data breach, investing in a dark web monitoring service is a mere pittance by comparison.
What are "compromised credentials"?
A compromised credential refers to login credentials, such as usernames and passwords, that have been stolen or obtained by an unauthorised person or entity.
When an attacker gains access to an individual's login credentials, they can use them to impersonate that person and access sensitive information or systems. Learn more about the risks of compromised credentials in this blog.
It is important to take steps to protect and monitor login credentials because they are a significant security risk for organisations. Leaked credentials can lead to data breaches and various cyber attacks, including phishing attacks, malware infections, credential stuffing attacks, or brute force attacks.
Types of credentials found through dark web monitoring tools
Dark web monitoring can uncover various types of employee credentials, including:
-
Usernames and passwords
Cybercriminals frequently steal login credentials and sell them on the dark web. These credentials can give them access to the business's network and sensitive data. -
Personally identifiable information (PII)
PII such as names, addresses, and Social Security numbers can be used to steal identities or commit other forms of fraud. -
Email addresses
Business email addresses can be used for phishing attacks or spamming. -
Financial information
Credit card numbers, bank account information, and other financial information can be used for fraudulent purchases or identity theft. -
Security question answers
Cybercriminals can use security question answers to reset passwords and gain access to employee accounts. -
Healthcare information
Medical records, insurance details, and other health-related information can be used for identity theft or fraudulent medical claims. -
Subscription service credentials
Logins for streaming services, social media accounts, and other subscription-based platforms can be stolen. -
Access badges
Information or copies of digital badges that grant access to a company's network if compromised.
What are the benefits of using a dark web monitoring service?
Dark web monitoring services offer several benefits that are essential for any business looking to protect its data. Here are some of the key benefits you can get from the service.
-
Proactive threat intelligence
Dark web monitoring services offer proactive threat intelligence, which can help you stay ahead of emerging threats and protect your sensitive data. -
Early detection of data breaches
Dark web monitoring services can detect data breaches before they become major security incidents, giving you the opportunity to take action before the breach becomes widespread. -
Protect your reputation
By monitoring the dark web, you can identify potential threats and take steps to mitigate them before they become public. This can help protect your company's reputation and maintain customer trust. -
Compliance
Dark web monitoring services can help you stay compliant with regulations that require companies to protect sensitive information, avoiding potential fines or legal actions. -
Competitive advantage
By monitoring the dark web, you can stay ahead of your competitorsabout emerging threats. It can help to develop a competitive advantage for your company.
What are the consequences of ignoring dark web monitoring?
Failing to monitor exposed credentials on the dark web can lead to a number of headaches for businesses, including:
-
Data breaches
When cybercriminals gain access to a company's network using compromised credentials, they can steal sensitive information, such as customer data, financial records, and intellectual property.
-
Financial fraud
Cybercriminals can use compromised credentials to conduct financial fraud, such as making unauthorised transactions or accessing company bank accounts.
-
Ransomware attacks
Ransomware is a type of malware that encrypts a company's data and demands payment to release it. Cybercriminals can use compromised credentials to gain access to a company's network and deploy ransomware, causing significant disruption and financial losses.
-
Reputational damage
A data breach or other cyber attack can damage a company's reputation, leading to lost business, legal action, and long-term damage to the brand's image.
-
Compliance violations
Many industries are subject to data protection regulations, such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA). Compromised credentials can lead to violations of these regulations, resulting in significant fines and legal actions.
This is why it's important for businesses to monitor the dark web for exposed employee credentials. By doing so, companies can proactively identify and respond to potential cyber threats before they cause harm.
How do dark web monitoring tools work?
Dark web monitoring tools work by continuously scanning the dark web for any data that may be relevant to a business. This includes data such as employee credentials, credit card numbers, and other sensitive information that may be stolen and sold on the dark web.
Once the tool identifies any data related to the business, it performs a series of checks to determine if the data is legitimate and if it poses a risk to the business. If the data is verified as legitimate, the tool will generate an alert, notifying the business of the compromised data.
The following is a typical process that dark web monitoring tools usually go through:
-
Scan the dark web
The first step in dark web monitoring is scanning the dark web to identify any stolen or compromised data related to the business. This is typically done using specialised software that can search through the dark web's hidden websites, forums, and marketplaces.
-
Identify compromised data
Once the dark web is scanned, the software identifies any stolen or compromised data related to the business. This can include login credentials, personal information, financial information, and other sensitive data.
-
Alert the business
Once compromised data is identified, the software alerts the business of the potential threat. This allows the business to take immediate action to secure any affected accounts, reset passwords, and investigate any potential breaches.
-
Breach report
Dark web monitoring software provides businesses with detailed reports on any compromised data found on the dark web. These reports can help businesses identify vulnerabilities in their security systems and take proactive measures to strengthen their defences.
-
Ongoing monitoring
Dark web monitoring is an ongoing process that involves continuously monitoring the dark web for new threats. This helps businesses stay ahead of cybercriminals and avoid potential data breaches.
What makes the best dark web monitoring tool?
Choosing the right dark web monitoring tool can be challenging. The criteria for organisations to choose a suitable dark web monitoring service will vary depending on the specific business needs. However, here are the main factors to consider when you're searching for a suitable tool for your business.
-
Holistic coverage
It's important for a dark web monitoring service to provide comprehensive coverage of the dark web, including both public and private marketplaces, forums, and other online sources. This will ensure that all potential threats and vulnerabilities are identified and monitored, giving businesses a complete picture of their security posture. -
Real-time alerts
A good dark web monitoring service should provide real-time alerts when potential threats are detected. These alerts should be customisable to the organisation's specific needs. It will be handy for users if the alerts can be delivered via multiple channels, such as email, SMS, or mobile app notifications. -
Customisable dashboards and reports
A dark web monitoring tool should provide customisable dashboards and reports that allow users to view their dark web monitoring data in a way that is relevant to their needs. This can include metrics such as the number of potential threats detected, the types of data compromised, and the geographic locations of threat actors. -
Actionable intelligence
A commendable dark web monitoring service should provide actionable intelligence that businesses can use to proactively mitigate threats and vulnerabilities. This can include recommendations for strengthening security measures, such as changing passwords or implementing multi-factor authentication, or alerts for suspicious activity that may require further investigation. -
Integration with existing security infrastructure
An easy-to-use dark web monitoring service should be able to integrate seamlessly with your business's existing security infrastructure, including security information and event management (SIEM) systems, endpoint detection and response (EDR) tools, and threat intelligence platforms. This will allow businesses to leverage their existing investments in security technology and streamline their security operations. -
Strong data privacy and security
The best dark web monitoring service should have strong data privacy and security measures in place, to protect the sensitive information that is being monitored. This can include encryption of data at rest and in transit, multi-factor authentication for access to the service, and regular security audits and vulnerability testing.
How to choose the best dark web monitoring vendor?
Choosing the right dark web monitoring vendor to provide the service is critical. Here are some factors to consider when evaluating potential vendors:
-
Reputation and experience
Look for a vendor with a proven track record and extensive experience in the dark web monitoring space. Consider reading reviews from other users, and ask for references from the vendor to ensure that they have a good reputation. -
Data privacy and security
Choose a vendor that has a strong commitment to data privacy and security. Ask about their data handling and storage practices, and ensure that they comply with relevant regulations. -
Customisation and flexibility
Look for a vendor that can offer customised solutions to meet the specific needs of your clients. Ensure that their services are flexible and can be easily integrated into your existing cybersecurity management. -
Pricing and support
Evaluate the vendor's pricing structure and ensure that it aligns with your cybersecurity budget. Consider the level of support that they offer, such as training and technical support.
5 steps to implement dark web monitoring
Once you've chosen a dark web monitoring service provider to work with, here are some steps you can take to start monitoring the dark web and protect your business data:
-
Define your scope
Identify which data you want to monitor, such as your company name, domain, or sensitive information. This will help you set up the right alerts and filters. -
Set up alerts
Configure alerts for your chosen keywords and data types. Set up real-time alerts via email or text message, so you can take action quickly if a threat is detected. -
Review reports
Regularly review reports generated by your monitoring tool. This will help you stay informed about emerging threats and identify potential threats. -
Take action
If a threat is detected, take action immediately. This may involve contacting law enforcement, taking steps to protect your data, or communicating with your customers and stakeholders. -
Continuously monitor
Cyber threats are constantly evolving, so it's important to continuously monitor the dark web for new threats and vulnerabilities. Regularly review your monitoring tool and adjust your alerts and filters as needed.
Get the right tool now to protect your business data
The dark web remains a murky and dangerous place where criminal activity thrives. As technology continues to evolve, so do the methods and techniques used by cybercriminals to exploit the anonymity of the dark web.
However, by understanding the dark web's inner workings, employing a variety of monitoring techniques, and staying up-to-date on emerging trends and threats, you can safeguard your assets.
Are you concerned about the safety of your organisation's information online? Our dark web monitoring tool, uBreach Pro offers a powerful and easy-to-use platform for scanning the dark web and protecting your digital assets. Take advantage of the 14-day free trial and ensure the safety of your business data today!

.png)