How stolen employee credentials on the dark web can harm your business
In today's interconnected world, businesses rely more on digital technology to manage their operations and reach customers.
However, with the rise of the dark web, cybercriminals have gained access to a vast underground marketplace where they can sell stolen credentials to the highest bidder. In fact, according to a recent study, there are over 15 billion stolen credentials circulating on the dark web, posing a serious risk to businesses of all sizes.
In this blog post, we'll explore why compromised credentials on the dark web are such a significant threat to your business and what steps you can take to protect yourself against this growing threat.
In this article, we'll cover:
-
What is the value of compromised credentials on the dark web?
-
Recent high-profile breaches caused by compromised credentials
-
Are there any prevention or mitigation strategies we can take?
What are "compromised credentials"?
Compromised credentials refer to login credentials, such as usernames and passwords, that have been stolen or obtained by an unauthorised person or entity. When an attacker gains access to an individual's login credentials, they can use them to impersonate that person and access sensitive information or systems that they would not otherwise have access to.
It is important to take steps to protect and monitor login credentials because they are a significant security risk for individuals and organisations. Leaked credentials could lead to data breaches and various cyber attacks, including phishing attacks, malware infections, credential stuffing attacks, or brute force attacks.
What is the value of compromised credentials on the dark web?
-
Access to sensitive information
Compromised credentials can provide access to sensitive information, such as personal information, financial data, and confidential business information. This information can be used for identity theft, financial fraud, or corporate espionage. -
Access to systems and networks
With compromised credentials, attackers would be able to gain access to systems and networks. This access can be used to steal data, install malware, or carry out other malicious activities. -
Facilitate further attacks
Compromised credentials can be used to facilitate further attacks, such as phishing attacks, credential stuffing attacks, or brute force attacks. Attackers can use compromised credentials to gain access to other systems or networks that may have more valuable information or weaker security measures. -
Higher value on the dark web
Compromised credentials are highly valued on the dark web because they provide a relatively easy and low-risk way for attackers to get access to sensitive information and systems. This makes them a sought-after commodity, with prices varying depending on the type of credentials and the level of access provided. -
Long-term value
Unlike other types of stolen data, compromised credentials can have long-term value. For example, an individual may use the same password across multiple accounts, meaning that an attacker with access to one set of compromised credentials can potentially access multiple accounts.
Popular types of attacks enabled by compromised credentials
-
Phishing attacks
These attacks involve tricking an employee into giving away their login credentials through a fake login page or email. Once an attacker has these credentials, they can access sensitive company information.
-
Credential stuffing attacks
Cybercriminals can use automated tools to rapidly input stolen usernames and passwords into login pages of targeted websites and applications, in the hopes of gaining access to user accounts. The success of these attacks largely depends on the number of users who reuse the same login credentials across multiple accounts. -
Social engineering attacks
This is a type of attack that involves manipulating an employee into giving away their login credentials through psychological manipulation. This can include impersonating someone in authority, creating a sense of urgency, or using other tactics to gain the employee's trust. -
Brute-force attacks
These attacks involve using software to repeatedly guess an employee's login credentials until the correct combination is found. This can be successful if the employee's password is weak or easily guessable. -
Insider attacks
Insider attacks are usually caused by an employee who intentionally or unintentionally shares their login credentials with someone who shouldn't have access to them. This can be especially dangerous if the employee has access to sensitive information or systems. -
Remote access attacks
If an employee's login credentials are compromised, an attacker can use them to remotely access company systems and data. This can be especially dangerous if the employee has access to critical systems or infrastructure.
Recent high-profile breaches caused by compromised credentials
In recent years, there have been several high-profile data breaches caused by compromised credentials. Let's dive into some of the most notable high-profile breaches caused by compromised credentials and the lessons that can be learned from them.
-
Capcom's data breach (November 2020)
The Japanese video game company, Capcom suffered from a data breach in November 2020. The company disclosed that over 350,000 customer and employee records had been leaked in a data breach. Hackers had gained access to the company's network through an old VPN device that was not updated with the latest security patches.
The note below was found on the encrypted systems. The game maker said it was a message from the threat actors. The note did not mention any price; it just instructed the company to contact the attacker to engage in negotiations.
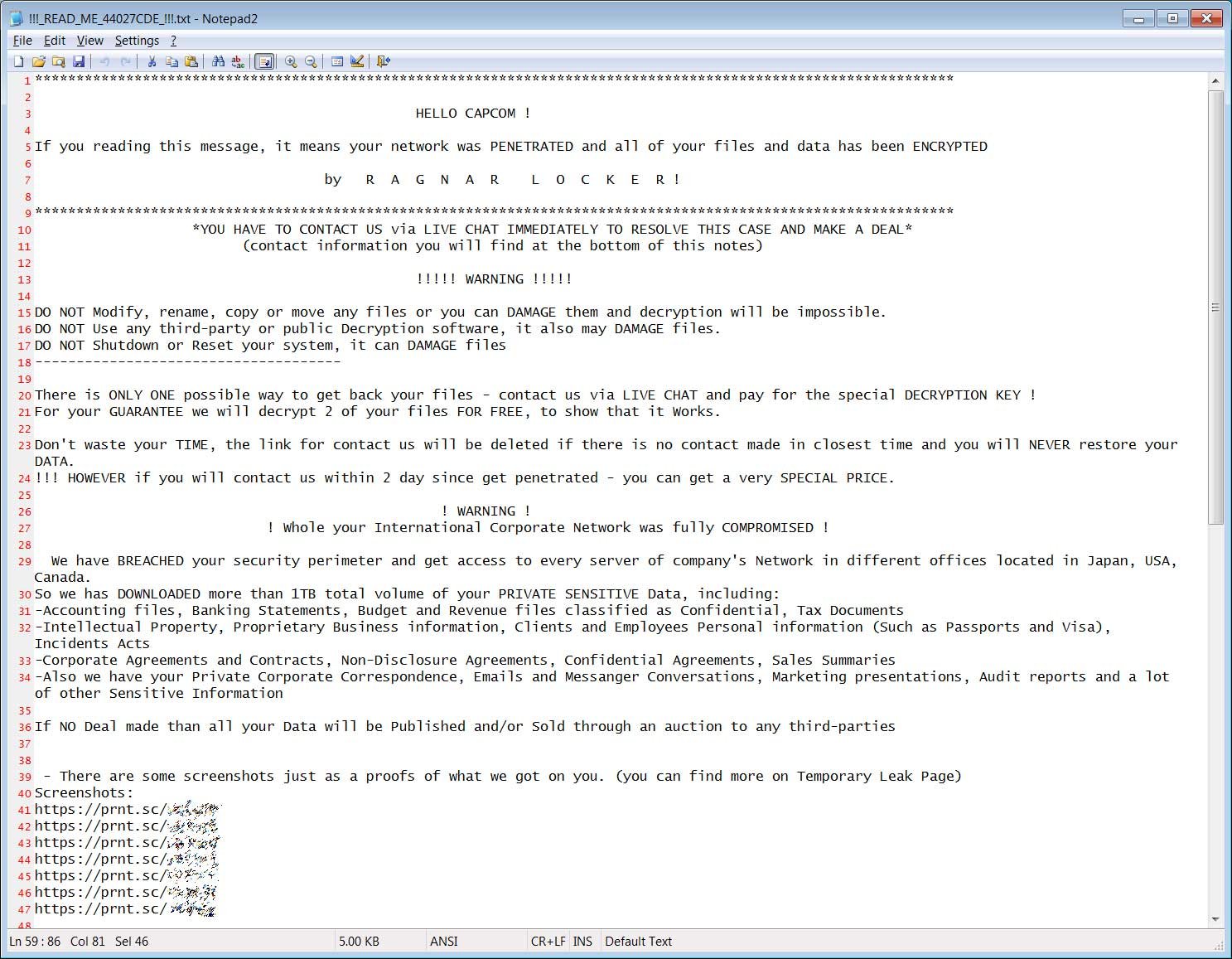 (Source: bleepingcomputer.com)
(Source: bleepingcomputer.com)
-
Colonial Pipeline suffered from business interruption (May 2021)
The inability to access key systems or the disruption of communication channels can result in a loss of income and revenue. A recent example of this is the ransomware attack suffered by Colonial Pipeline in May 2021.
In this attack, hackers gained access to Colonial Pipeline's network through a compromised password which was still active. The hackers were then able to deploy ransomware that encrypted critical data and disrupted the company's ability to operate.
(Source: abcnews)
As a result of the attack, Colonial Pipeline was forced to shut down its pipeline operations, which transport fuel across the eastern United States. This caused fuel shortages, price spikes, and panic buying in some areas, leading to significant business interruption and economic impact.
-
Whatsapp account takeover (March 2023)
Action Fraud, the UK’s national reporting centre for cybercrime and fraud, are warning people to remain vigilant after they received more than 60 reports relating to a scam that steals access to a WhatsApp user’s account.
According to the authority, the criminal would pose as a friend or someone who’s a member of a WhatsApp group that the victim is in. Then, they would send seemingly normal messages to try and start a conversation.
While doing so, the victim would receive a text message from WhatsApp with a six-digit code. The scammer would then claim that the code was sent to the victim's number by accident and ask for it to be sent to them. The scammer could then log in and sign the victim out.

(Source: Action Fraud)
What business risks are posed by compromised credentials?
-
Financial loss
Cybercriminals can use stolen employee credentials to carry out fraudulent activities, such as making unauthorised purchases or transferring funds from company accounts. This can result in significant financial losses for your business. -
Damage to reputation
A data breach or financial loss due to stolen employee credentials can harm your company's reputation, leading to a loss of customer trust and business opportunities. -
Legal and regulatory penalties
A data breach resulting from stolen employee credentials can lead to violations of industry regulations, such as HIPAA or GDPR. -
Loss of customer trust
Customers may lose trust in an organisation that has experienced a data breach. They may feel that their personal information has been mishandled or that the organisation did not take adequate steps to protect their data.
Are there any prevention or mitigation strategies we can take?
Protecting business data is crucial to ensure that sensitive information remains confidential and doesn't fall into the wrong hands. Here are some steps you can take to protect your business data:
-
Identify your sensitive data: The first step is to identify the types of data that are most important to your business. This might include financial records, customer data, or trade secrets.
-
Implement access controls: Use access controls to limit who can access sensitive data and define access levels based on job roles or responsibilities. For example, only employees in the finance department may need access to financial data.
-
Monitor data access: Regularly monitor who is accessing your sensitive data and when they are accessing it. This can help you detect any suspicious access and take action to prevent data breaches.
-
Keep software up-to-date: Keep your software and operating systems up-to-date with the latest security patches and updates to ensure that any vulnerabilities are addressed.
-
Implement data backup procedures: Regularly back up your sensitive data to a secure off-site location to prevent loss due to data breaches.
- Use dark web monitoring service: Dark web monitoring can help detect potential data breaches early on, alert you when sensitive information appears on the dark web, and continuously scan the dark web for any mention of your business's information to help you stay ahead of emerging threats.
Protect your business data today!
As the world becomes increasingly digital and interconnected, it is essential to remain vigilant and proactive in safeguarding your business from the dangers of the dark web. Remember, the best defence is always prevention.
If you're interested in trying out dark web monitoring software for your business, we invite you to join our 14-day free trial. With our powerful dark web monitoring tool -- uBreach Pro, you can monitor your business's sensitive data and receive real-time alerts if any information is found on the dark web. This will allow you to take immediate action to protect your business.
Sign up today and experience the peace of mind that comes with knowing your business's data is secure.

.png)
.png)