How Human Risk Management Supports Compliance Across Global Standards
Security compliance requirements extend beyond technical safeguards – they require organizations to demonstrate that their workforce is prepared to prevent, detect, and respond to risks effectively. HRM becomes a pivotal strategy for meeting and sustaining compliance. This blog explores how HRM aligns with global compliance requirements to maximize control efforts and reduce organizational risk.
In this blog, we will cover:
- What is Human Risk Management (HRM)?
- 5 Key Components of a Successful HRM Program
- An Overview of Global Standards that Requires HRM
- HRM’s Role in Achieving Compliance
What is Human Risk Management (HRM)?
Human Risk Management (HRM) is a strategic approach to identifying, assessing, and mitigating risks posed by human behaviour within an organization. It represents a proactive approach to addressing human vulnerabilities within an organization’s security framework. By focusing on educating, equipping, and empowering employees, HRM minimizes human-related risks that could lead to compliance violations or security breaches.
5 Key Components of a Successful HRM Program
HRM encompasses a range of tools and solutions designed to minimize security vulnerabilities caused by human error, lack of awareness, or malicious actions. Key elements of HRM as defined by usecure include: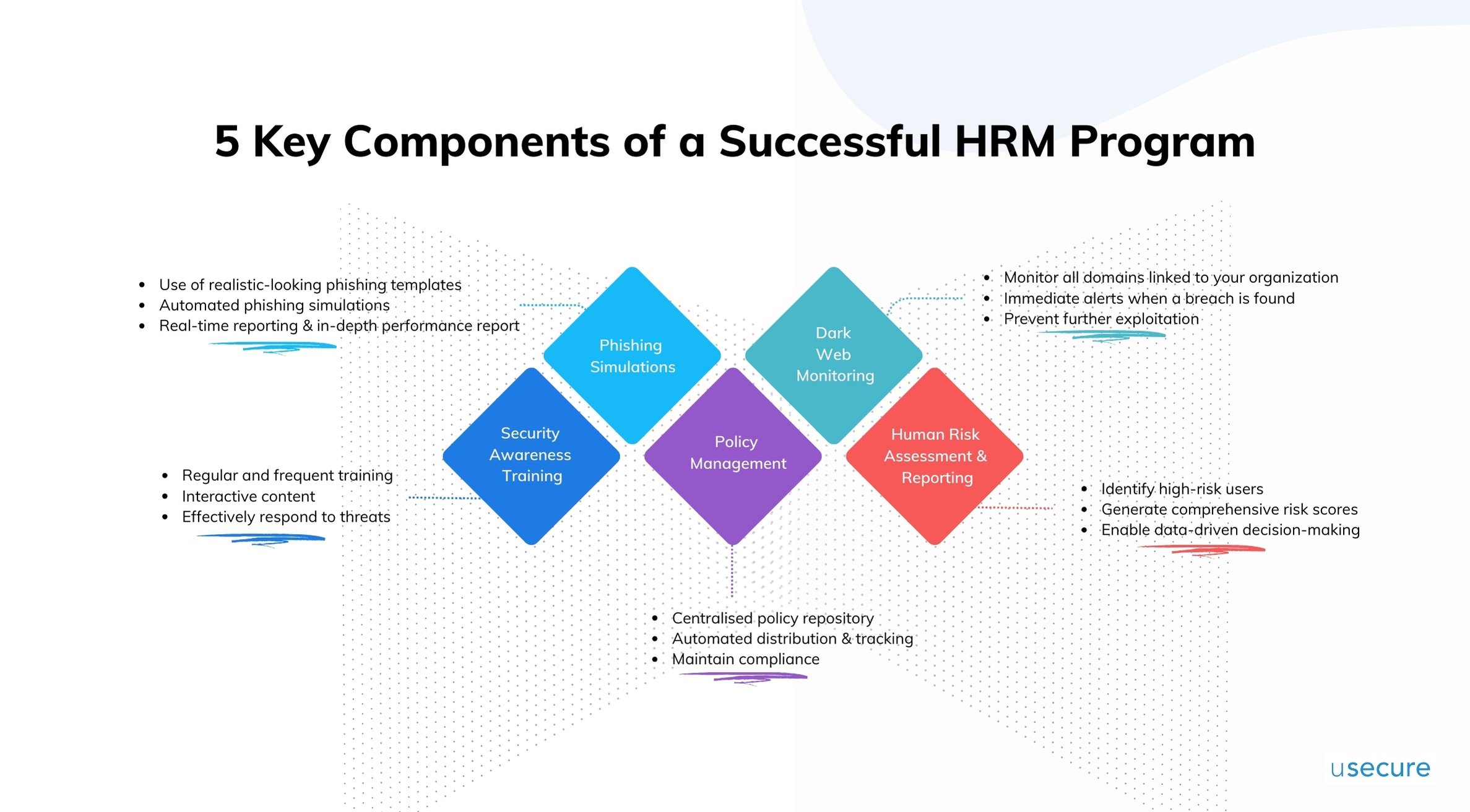
-
Security Awareness Training: HRM involves providing employees with regular and frequent training to educate them about potential cybersecurity threats, such as phishing, malware, and social engineering attacks. This training empowers staff to recognize and respond to threats effectively. Studies have shown interactive learning materials like animation and scenario-based training can enhance user engagement, making learning more effective and ensuring employees retain critical information.
-
Phishing Simulations: A proactive component of HRM is testing employees’ susceptibility to phishing attacks through automated phishing simulation. Ensure you have realistic phishing email templates that mimic actual threats, increasing the effectiveness of simulations. Real-time reporting and detailed insights are also important for you to monitor the simulation outcomes instantly.
-
Policy Management: HRM ensures that employees understand and comply with organizational security policies. With the help of a policy management tool, you can access and manage policies in a centralised repository, make automated distribution and track the progress. This makes it easier for businesses to maintain compliance and reduce risks associated with non-adherence.
-
Dark Web Monitoring: By identifying compromised credentials or sensitive information across all domains linked to your organization on the dark web, HRM allows you to act swiftly to protect accounts and prevent further breaches. When a breach is detected, affected employees are immediately alerted, enabling them to take quick action to secure their accounts and prevent further exploitation.
-
Human Risk Assessment and Reporting: HRM provides actionable insights by continuously assessing the risk levels of employees based on their behaviour, training completion, and phishing test results. This helps organizations focus resources on high-risk areas and demonstrate compliance with regulatory requirements.
In essence, HRM goes beyond traditional training by integrating proactive monitoring, targeted risk reduction, and measurable improvements in employee security behaviour. The ultimate goal of HRM is to reduce human vulnerabilities and strengthen an organization’s overall cybersecurity posture.
An Overview of Global Standards that Require HRM

Several global standards directly link compliance requirements to human-centric strategies. For example, the famous International Organization for Standardization (ISO) based in Geneva, underscores the importance of staff competence and awareness for effective risk mitigation. In the context of information security, ISO 27001 encourages human risk management by requiring organizations to ensure that employees are aware of their security responsibilities and adequately trained to handle threats.
Moreover, individual countries across the seven continents have developed their own frameworks and regulations that emphasize the critical role of human-centric approaches in cybersecurity compliance. The following is an overview of how HRM is addressed in global cybersecurity standards across the seven continents.
Africa
Despite the differences in infrastructure, resources, and policy development, African countries are gradually incorporating HRM requirements to improve their cyber security.
- The African Union Convention on Cyber Security and Personal Data Protection (Malabo Convention) promotes capacity building and awareness for securing their cyberspace. It encourages training programs to address the human aspect of cyber risks.
- South Africa’s Protection of Personal Information Act (POPIA) stresses organizational responsibility for data security, including employee training to prevent breaches.
- Nigeria's National Cybersecurity Policy and Strategy (NCPS)
underscores the importance of human capacity building, advocating for regular training and awareness programs to mitigate cyber threats. - Togo's Personal Data Protection Law (PDPL) requires organizations to set up a personal data protection authority, emphasizing the need for employee awareness and training in data protection principles.
- Botswana's Cybercrime and Computer-Related Crimes Act (CCRCA)
includes provisions for organizations to educate and train employees on cybersecurity measures to prevent cyber offences. - Kenya's Computer Misuse and Cybercrimes Act (CMCA) mandates organizations to implement cybersecurity measures, including employee training, to safeguard against computer misuse and cybercrimes.
Asia
As cyber threats grow more sophisticated, Asian countries are taking significant strides in fortifying their digital landscapes through comprehensive cybersecurity legislation. Central to these efforts is the emphasis on HRM.
- China’s Cybersecurity Law (CSL) mandates regular employee training, particularly for staff managing critical information infrastructure.
- India’s Digital Personal Data Protection Act (DPDP) encourages organizations to train employees on data privacy practices.
- Japan’s Act on Protection of Personal Information Act (APPI) similarly encourage organizations to train employees on data privacy and security practices.
- Singapore's Cybersecurity Act (CSA) requires owners of Critical Information Infrastructure (CII) to conduct regular cybersecurity training and awareness programs for their employees to maintain a robust security posture.
- Thailand's Cybersecurity Act (CA) obliges organizations to establish cybersecurity training programs and set minimum standards for cloud security, ensuring that personnel are well-prepared to address cyber threats.
- Vietnam's Law on Cybersecurity (LOCS)requires organizations to provide cybersecurity training to their employees, enhancing their ability to protect personal data and respond to cyber incidents.
- Indonesia's Personal Data Protection Law (PDP) mandates organizations to implement measures, including employee training, to protect personal data and ensure compliance with data protection standards.
- Malaysia's Personal Data Protection Act (PDPA) requires organizations to communicate their data protection policies to staff, ensuring employees are informed about their responsibilities in handling personal data.
Europe
In Europe, countries have started to focus on cybersecurity since the early 2000s. European Union has established overarching laws and directives which apply uniformly across all member states. Non-EU member states in Europe such as Norway and Switzerland develop their own cybersecurity laws that are influenced by EU regulations due to trade agreements and their participation in regional initiatives. All these laws emphasize the importance of addressing human vulnerabilities to ensure compliance and mitigate risks.
- EU's General Data Protection Regulation (GDPR), requires organizations to implement organizational measures such as employee training to reduce human errors.
- EU's NIS 2 Directive also explicitly mandates staff training for incident response and cybersecurity awareness.
- EU's Cybersecurity Act (CSA) strengthens the EU Agency for Cybersecurity (ENISA) and establishes an EU-wide cybersecurity certification framework, encouraging organizations to adopt certified products and services and to train employees accordingly.
- EU's Digital Operational Resilience Act (DORA) focuses on the financial sector, requiring firms to ensure operational resilience by implementing comprehensive risk management frameworks, which include regular employee training on cybersecurity threats and protocols.
- Norway's Digital Security Act (DSA) mandates that covered companies establish management systems for digital security, conduct risk assessments, and ensure incident management, emphasising the importance of HRM in maintaining digital security. National Cyber Security Strategy (NCSS-NO) also underscores the significance of human factors in cybersecurity.
- Switzerland's Federal Act on Data Protection (FADP) requires ensuring employees are trained and aware of data protection principles, aligning with HRM practices to prevent unauthorized data processing. National Cyber Security Strategy (NCSS-CH) also emphasizes the need for building competencies to address deficiencies in security management.
North America
The United States and Canada have incorporated HRM into industry-specific standards and regulations.
- In the U.S., HIPAA (Health Insurance Portability and Accountability Act) requires workforce training to secure protected health information (PHI).
- U.S. SOC 2 is a cybersecurity compliance framework that emphasises HRM under its Trust Services Criteria.
- U.S. federal-level law, Gramm-Leach-Bliley Act (GLBA), requires financial institutions to manage human risk through security awareness training and risk assessments.
- Another U.S. federal-level law, Sarbanes-Oxley Act (SOX), requires training employees on compliance and ethical practices to mitigate insider threats, fraud, and negligence.
- The U.S. Federal Information Security Management Act (FISMA) requires federal agencies to develop, document, and implement programs to secure information systems, including mandatory security awareness training for employees.
- In Canada, The Personal Information Protection and Electronic Documents Act (PIPEDA) promotes staff training as part of maintaining privacy and data security.
- U.S., Canada, and Mexico came together and established the Electric Reliability Corporation Critical Infrastructure Protection (NERC CIP). It mandates that entities in the energy sector establish, document, implement, and maintain a security awareness program for all personnel to safeguard critical infrastructure.
South America
- Argentina has made strides in cybersecurity, with the Personal Data Protection Act (PDPA) (Law No. 25,326) requiring organizations to protect sensitive data and emphasizing the importance of employee awareness in achieving compliance.
- Brazil’s LGPD (Lei Geral de Proteção de Dados) mandates privacy training for employees and emphasizes human-centric measures to protect personal data.
- Chile’s Data Protection Act also stresses the need for organizational measures like staff training.
- Colombia's Data Protection Law (Law 1581) requires organizations to adopt internal policies to train employees on their responsibilities regarding personal data handling.
- Peru's Personal Data Protection Law (Law 29733) mandates that organizations implement security measures, including training programs, to protect personal data and ensure compliance with the law.
Oceania
In Oceania, Human Risk Management (HRM) is a critical component of cybersecurity frameworks, with both Australia and New Zealand emphasizing employee training, awareness, and proactive measures to address human vulnerabilities.
- Australia’s Privacy Act 1988 and Cyber Security Strategy 2020 both emphasize employee training to ensure compliance with privacy principles and mitigate cyber threats.
- Australia's Essential Eight framework established by the Australian Signals Directorate further encourages regular user training as a foundational cybersecurity measure.
- New Zealand’s Privacy Act 2020 mandates organizations to take reasonable steps to protect personal information, including ensuring employees are trained in data protection principles.
- New Zealand’s Cyber Security Strategy 2019 prioritizes building a cyber-resilient society, encouraging security awareness programs and collaboration with businesses to address human vulnerabilities.
Antarctica
While Antarctica does not have a permanent population or standalone cybersecurity standards, research stations must comply with the cybersecurity laws of their countries.
- For example, the United States Antarctic Program (USAP) follows NIST cybersecurity standards and emphasizes awareness training for researchers and staff to ensure security in extreme and isolated environments.
HRM’s Role in Achieving Compliance
A well-executed Human Risk Management (HRM) strategy plays a critical role in helping organizations comply with cybersecurity standards and regulations. By addressing human vulnerabilities through risk assessment, structured training, policy management, and dark web monitoring, HRM helps organizations reduce the likelihood of non-compliance and strengthens their overall security posture. Let’s look at how HRM supports compliance in three main ways: 
1. Mitigate Human Error
Human error remains a leading cause of cybersecurity breaches. HRM mitigates this risk by fostering a culture of vigilance through regular training and assessments. Key measures include:
- Employee Training: Employees are taught to recognize threats like phishing, social engineering, and other scams, significantly reducing the risk of incidents caused by negligence or oversight.
- Behavioural Assessments: By identifying high-risk employees and targeting their specific vulnerabilities, organizations can implement tailored interventions to address gaps in awareness and behaviour.
2. Provide Documentation and Audit Readiness
Laws and standards like GDPR, HIPAA, SOC 2, and ISO 27001 often require organizations to demonstrate compliance efforts through detailed documentation and audit trails. HRM platforms simplify this process by:
- Generating Comprehensive Reports: HRM systems track employee training progress, policy acknowledgements, and risk assessment results, providing clear evidence of compliance efforts.
- Ensuring Up-to-Date Records: By maintaining up-to-date records, HRM tools streamline audits and inspections, reducing the administrative burden on compliance teams.
3. Enable Ongoing Training and Policy Management
Compliance is not a one-time activity but requires continuous effort. HRM systems help organizations stay aligned with evolving regulations by:
- Automating Training Reminders: Regularly scheduled, role-specific training ensures employees remain up-to-date on the latest security practices and regulatory requirements.
- Streamlining Policy Updates: HRM platforms allow organizations to distribute updated policies, track employee acknowledgements, and measure compliance in real time.
Empower Your Workforce with HRM for Compliance and Security
Implementing, managing, and tracking a Human Risk Management solution can feel overwhelming—but it doesn’t have to be. We believe a user-friendly HRM platform should be designed with simplicity at its core, making deployment and administration effortless.
If you’re looking to simplify and enhance your HRM strategy, we provide a comprehensive platform designed to help you reduce human risk and meet compliance requirements effortlessly. Get your 14-day free trial or access a library of on-demand demos to experience the modern way to implement your HRM program.