39% of Employees Gave Away Their Passwords In This Phishing Simulation
It’s half past four on a Thursday afternoon. You’re getting through your last tasks of the day, when you receive a new email. It has an alluring title:
"Holiday Policy Change - Action Required"
Would you click it?
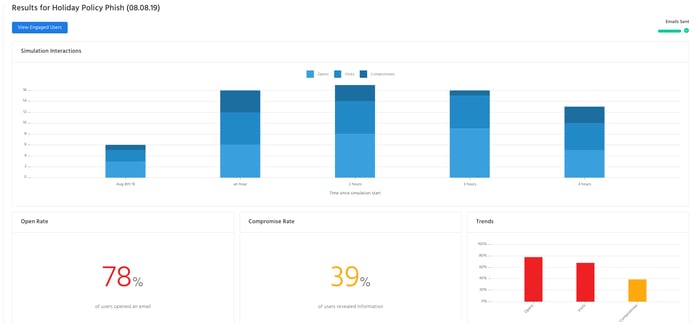
When an email with this title was sent out to the employees of one of our clients, 78% of them opened it. The email, however, was a phishing scam: By the end of the day, 39% of the recipients had been duped into giving up their email passwords.
Luckily for our client, the email was only a simulation.
Here's the story of the holiday phish.
In this article, we'll go through...
- What is phishing?
- What is simulated phishing and how does it help?
- How do real-world cyber criminals create phishing emails?
- What was in the holiday policy email?
- How were employees duped into giving up their passwords?
- What happened afterwards?
- The full simulation results
- How did our client benefit from this?
- How can you protect your own organisation?
What even is phishing?
Phishing is the sending of fake emails to dupe victims.
Phishing has grown to become one of the main cyber threats that both businesses and individuals face. It involves sending out a deceptive message to dupe the targets into performing a specific action. This could be providing sensitive information, making a bank transfer, or following a link to a page where their credentials will be harvested. Phishing emails can also contain malware in an attachment disguised as a legitimate document, or link to a page containing viruses. This is why phishing plays a role in the majority of cyber attacks.
To learn more about phishing, visit our complete guide to phishing scams.
What is simulated phishing - and how does it help?
Phishing simulations are used to raise staff awareness about phishing.
Simulated phishing means sending out 'fake' phishing emails. These are often modelled after real-world phishing emails and use similar techniques to catch the target's attention, but are intended to educate the target on the risks of phishing rather than to trick them into giving up their details.
While training end-users on the risks of phishing and the common telling signs of phishing emails is essential, simulated phishing allows employees to put what they've learned into a real-world test. This helps raise awareness about phishing - employees that do fall for simulated phishing are sure to remember how easy it is to fall for a phishing scam - and the results are recorded for you to see how your employees fare in the simulation. This data can then be used to provide additional training and guidance to employees most at risk, helping you secure your organisation.
Learn how you can use uPhish to raise phishing awareness and test the phishing response of your own workforce.
How do cyber criminals create phishing emails?
Real-world phishing emails offer something worth clicking - or create a sense of urgency. The most dangerous do both.
Real-world phishing emails generally fall into two categories: template-based and spear phishing. Template-based attacks are the 'standard' phishing attack: they use a generic template that can work no matter who the email is sent to, making them ideal for spamming vast numbers of phishing emails. Most people using email these days are savvy enough to filter out these attacks - if they aren't caught by the anti-spam functions of email clients beforehand. This is why just about every cyber criminal who knows what they're doing has moved on to spear phishing.
Spear phishing gets its name from the fact that it is a targeted attack, unlike the template-based attacks that cast a wide net. Cyber criminals seek out information about their targets first, before utilising this information to make their phishing bait appear genuine and believable. This information can be as simple as finding out and using the target's name, or can involve tedious study of social media profiles to impersonate persons and infiltrate networks before striking at the most opportune moment.
What was in the holiday policy email?
The email posed as a message from HR that was too lucrative to miss.
The tricky thing with simulated phishing is creating an attack that's believable enough to appeal to all employees, yet broad enough to cover the whole organisation. In this case, the only 'targeted' information we used was the name of the organisation, which we placed in the text of the email.
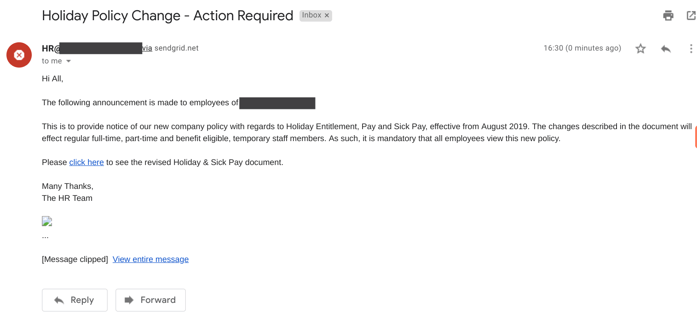
This is the email that 78% of employees opened.
In order for a phishing email to be effective, the cyber criminal must get the victim to perform an action - and there's no better way to do that than by creating a sense of urgency. In this case, not only was the 'Action Required' in the title was sure to catch employees attentions', but the email also promised something in return: knowledge about the new holiday policy. After all, who wouldn't be tempted to spend some of their Thursday afternoon thinking about their next holiday?
Within a couple of hours of sending out the simulation, 68% of recipients had not only opened the email but followed the link within.
How were employees duped into giving up their passwords?
Most employees sign into apps like 0365 every day - causing them to enter their credentials almost automatically when presented with what looks like a log-in screen.
The employees that followed the link were presented with an Office 365 log-in screen - ostensibly required to verify their identities before allowing them access to the Holiday & Sick Pay policy. The landing page itself is an almost exact replication of a real Office 365 log-in screen - a reasonably easy feat for a cyber criminal to accomplish as it only requires copying the HTML and CSS code from the real log-in page.
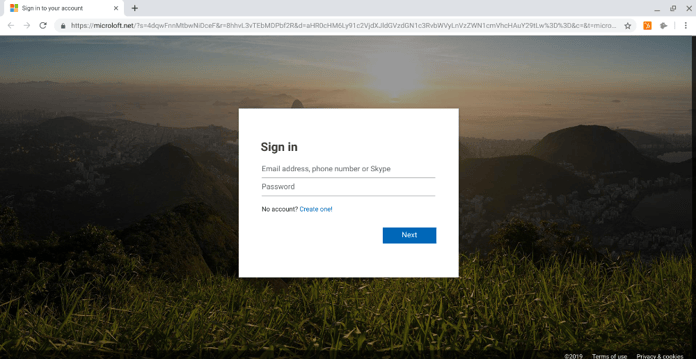
The 68% of employees who followed the link the email saw this landing page. 58% of them entered their email address and password.
While the page itself would not give a user any clues about the real owner of the form, the domain name tells a different tale. When entering your credentials online, it's important to always check the domain name of the site. This is because while making your page imitate another page is quite trivial, faking the domain name is a lot harder.
In this case, the domain reads microloft.com - not microsoft.com, which is the domain where a real Office 365 log-in page would be located. At a quick glance, the domains do look very similar - but this is not much of a consolation when a cyber criminal has already ran away with your passwords.
What happened afterwards?
The members of staff who clicked the link found out they had been duped.
Instead of finding the juicy details of a new holiday policy, the employees that entered their credentials on the landing page were greeted with a message asking them to contact their IT team. Their passwords were not sent forward to us or anyone else, or recorded in any manner. Had this been a real phishing attack, however, all passwords that had been entered here would now be in the hands of a cyber criminal - with potentially disastrous results.
When a cyber criminal gains a user's email password, a whole world of opportunity opens up for them. Any sensitive or confidential data contained in the user's emails and attachments are now available for the cyber criminal. Since most users use their work email as the back-up or authentication for services like Google Drive, Slack, Hubspot, Trello, Office 365 etc., the attacker would also gain access to these accounts and all data within. A patient attacker, however, would not use this data or make themselves known, but rather stay quiet, monitor email activity to learn more about the business, and wait for the most opportune moment to strike when they can extract the most value out of the business.
If an attacker gained access to not just one email, but the emails of 39% of the company's employees, you can only imagine the type of havoc they could cause.
The full simulation results
The majority of staff opened the email and followed the link - and 39% ended up giving away their passwords.
This phishing simulation had a high 'success' rate - but it's not too dissimilar from the numbers we see from other organisations without existing security awareness training in place.
Here are the full results:
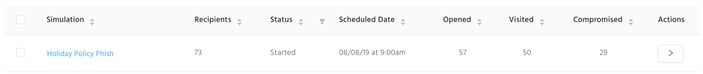
| Received | Opened | Visited | Compromised |
| 73 | 57 | 50 | 29 |
| 100% | 78% | 68% | 39% |
And here's an explanation of what the different categories mean:
Received: How many employees were sent - and successfully received - the email.
Opened: How many employees opened the email by clicking or tapping on it.
Visited: How many employees followed the link in the email.
Compromised: How many employees gave away their log-in details on the phishing page.
How did our client benefit from this?
The good news, as far as our client is concerned, is that they have now fully identified the human threat facing their organisation. Their employees are now all enrolled onto security awareness courses encompassing not only email and phishing awareness but also topics including safe use of removable devices and the risks of data interception on public Wi-Fi networks.
This simulation allowed our client to:
- Discover the company's risk level and vulnerability to human error
- Raise awareness about security in a memorable manner among all staff
- Identify employees in need of extra training which was automatically provided to them through usecure's automated training
In a couple of months, our client may choose to send out another simulated phishing campaign to see how their employees fare after some training - or they may wish to turn on our auto-phish feature, which constantly selects random employees to test with a templated attack from our library.
What can you do to protect your own organisation?
Regular training and testing is key to protecting your business from phishing scams.
With Accenture recently estimating the total global cost of cyber crime over the next five years to be $5.2 trillion, your business simply can't afford to leave itself unprotected. Security awareness training addresses cyber breaches at the very core - the natural tendency of untrained users to make mistakes. Simulated phishing works best when used to complement training, as it gives users an opportunity to put what they've learned into practice, as well as letting you assess how effective training has been at improving outcomes.
No technical solution is capable of stopping your employees from making errors, but with the right tools you can turn your end-users from your weakest link into your first line of defence.
If you'd like to learn more about our security awareness training and simulated phishing solution, follow the link below.
Learn how security awareness training and simulated phishing can safeguard your organisation against the most damaging cyber threats.

.png)