Top 10 phishing simulation best practices
Phishing attacks are becoming increasingly sophisticated. According to BleepingComputer, just a few days ago, a threat actor attempted to sell over 1,800 web injects for stealing credentials and sensitive data from banking on Russian cybercrime forums. Don't wait until it's too late. Learn about the phishing simulation best practices and take a proactive approach to protect your business data.
1. Set clear goals and objectives
2. Collaborate with other departments
3. Educate employees about phishing attacks
7. Gain insights from training reports
8. Continuously update phishing simulations
9. Repeat simulation training regularly
10. Use the simulation results to determine security policies
1. Set clear goals and objectives
Setting goals and objectives is important because this provides direction. Goals and objectives help to focus efforts and resources on specific targets, ensuring that all activities are aligned towards a specific cybersecurity purpose. Determining what you want to achieve with the simulation is the key to success.
When setting goals, it is important to keep the simulated phishing attempts in line with legal and ethical guidelines. In addition, clearly communicating the goals of the simulation to all participants is essential. Clearly defined objectives and goals provide your employees with a sense of purpose and motivation.
VentureBeat has interviewed 31 CISOs from around the world to share their cybersecurity priority lists. Get some useful ideas from the leaders' suggestions and start planning your own goals for this year.
2. Collaborate with other departments
Work with other departments, such as IT and human resources, to ensure the simulation aligns with overall security and compliance goals. By working together, departments can share resources and knowledge, reduce duplication of effort and increase efficiency. Teaming up with other departments also enables the organisation to respond more quickly and effectively to prevent phishing attacks. This article published by SHRM, a popular HR management website, has explained how a cross-functional security team can tremendously help to prevent data breaches.
3. Educate employees about phishing attacks
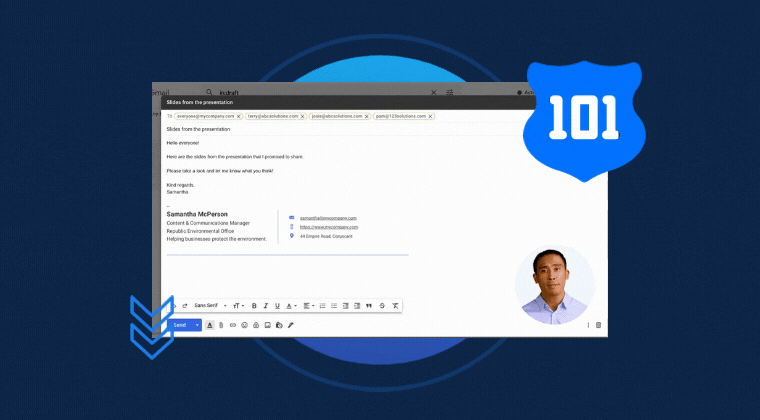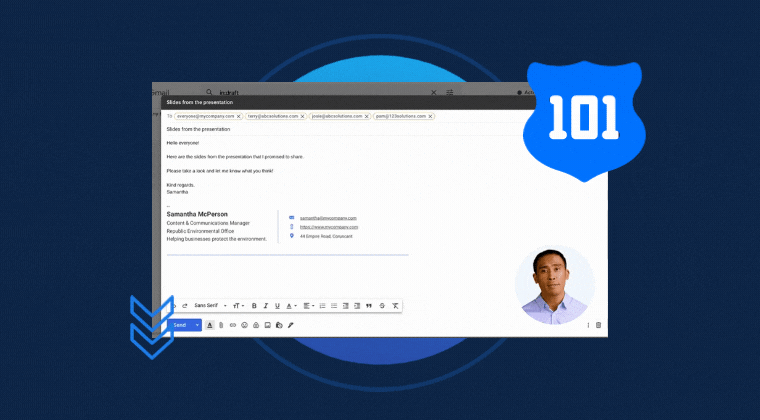
Before conducting the simulation, it is necessary to educate employees about what phishing attacks are, how they work, and how to identify and report them. Training and education on how to identify and respond to phishing attempts before the simulation takes place. 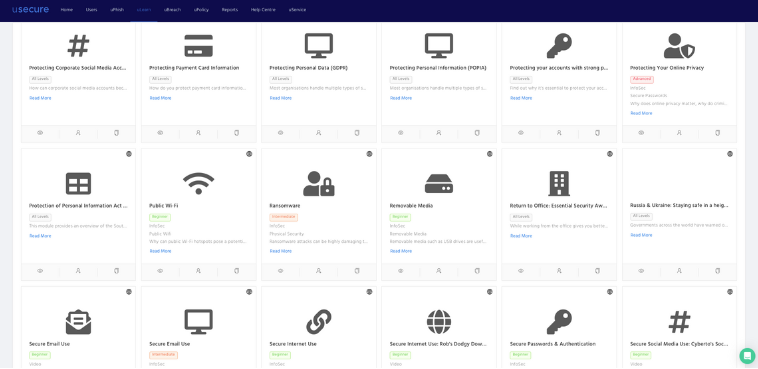
Some anti-phishing software vendors offer bite-sized training courses with interactive teaching materials. This kind of easily digestible training content can largely enhance learners' engagement.
Additionally, it is worth considering a variety of forms for delivering the phishing simulation, such as emails, text messages, and phone calls. Different file types, such as PDF, Word, Excel etc can also be used in the training to best mimic real phishing attacks.
4. Customise the simulations
Customise the simulations to your organisation's needs and make them as relevant as possible. Forbes, a famous content distribution platform for technology, has pointed out the importance of tailoring cybersecurity training for employees.
Use subject lines, sender names, brand colours, logos, domains, URLs, and corresponding email content that is relevant to your employees and can closely imitate real-world phishing attacks. It is recommended to use different levels of difficulty in the simulation to test employees of different skill levels or professional backgrounds. It is also suggested to customise the simulation to target specific departments or groups of employees who are more likely to be targeted by cyber criminals.
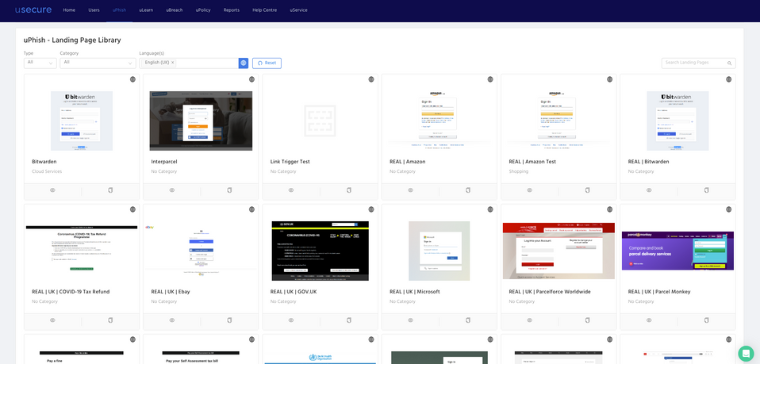 There is no one-size-fits-all solution for cybersecurity training. Therefore, some anti-phishing training tools allow you to create simulations that are specifically tailored to the targeted recipients. Make sure your simulator provides you with this flexibility.
There is no one-size-fits-all solution for cybersecurity training. Therefore, some anti-phishing training tools allow you to create simulations that are specifically tailored to the targeted recipients. Make sure your simulator provides you with this flexibility.
5. Monitor and track results
Utilise the tracking function of the simulator to monitor employee responses and analyse the results.
By monitoring phishing results, you can track the success rate of phishing attempts, which can indicate the level of phishing awareness among your employees. If you find that a high percentage of phishing emails are being opened and acted upon, it may be necessary to provide additional training or reminders to your employees on how to identify and avoid phishing attempts.
Furthermore, monitoring phishing results can help you evaluate the efficiency of your security systems and procedures. If you find that a large number of phishing emails are slipping through your filters, it may be necessary to adjust your email security settings or implement additional security measures.
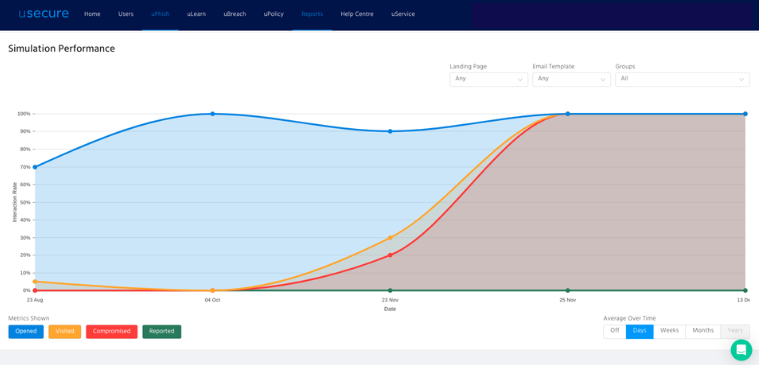
Almost all phishing simulation tools allow you to see your users' performance. You may want to make the most use of the function and identify the venerable users.
6. Follow up with employees
After the simulation, follow up with employees who fell for the attack and give them additional training and guidance. Providing feedback and coaching to employees is extremely crucial to help them learn from their mistakes and prevent them from falling for similar attacks in the future.
Incorporating a reward system is an effective way to encourage desired behaviour. For employees who successfully identify and report simulated phishing attempts, rewards or prizes can be awarded if the company's budget and resources allow it. Studies have shown that consistently recognising and rewarding employees for their contributions can help to build morale and motivation, which can lead to the overall success of phishing simulation training.
7. Gain insights from training reports
Regular reporting regarding simulation results and training progress allows you to see what is happening in the phishing simulation and understand how it is performing.
Some vendors provide in-depth reporting to help you understand your ongoing performance, including a summary of your organisation's overall risk; a breakdown of user management activities, as well as analytics for user training.
By receiving regular reports, you will be able to review the organisation's key areas for improvement. Check out our video to learn more.
8. Continuously update phishing simulations
Simulation content and forms should be kept up-to-date based on the current phishing trends, changes in the threat landscape, new technologies, and employee feedback.
It is important to regularly update phishing simulation training because phishing attacks are constantly evolving. It is essential to keep the training content relevant and ensure that employees are well-prepared to identify and respond to the latest phishing threats.
It is worth spending time updating your anti-phishing training from time to time in order to educate employees on the latest phishing techniques. Get more ideas for updating your simulated phishing attacks in this video.
9. Repeat simulation training regularly
Conducting phishing simulations at regular intervals is the key to assuring employee preparedness. The frequency at which you should repeat phishing simulations depends on several factors, including the size of your organisation, the risk profile, and the desired outcome of the simulation.
However, in order to keep your employees vigilant in this highly complex and ever-growing cyber threat landscape, it is generally believed that phishing simulation should be deployed every 2 to 4 weeks. Check out this video to know more about how often you should deploy phishing simulations.
It is important to note that the frequency of phishing simulations should be adjusted based on the results and effectiveness of each simulation. If a high number of employees fall for the simulation, it may be necessary to increase the frequency of simulations to provide more regular training and education.
10. Use the simulation results to develop security policies
Simulation results should be used to develop and refine security policies. Based on the results of a phishing simulation, organisations can assess the effectiveness of their technical controls, evaluate the behaviour and responses of employees, and detect vulnerabilities in their systems.
The results of phishing simulations can provide valuable information which is helpful for implementing additional measures to improve the organisation's overall security posture. By doing this, organisations can promote a culture of security that better protects them against real-world phishing threats.
Safeguard your business data
By following best practices for phishing simulations, organisations can ensure that their simulations are effective, efficient, and aligned with their overall security strategy.
Don't let cybercriminals compromise your organisation. As an experienced cybersecurity software vendor, we provide everything you need in your anti-phishing training. Stay ahead of the game with our cutting-edge cybersecurity software. Try our 14-day free phishing simulation now or click on our Employee Phishing 101 blog post to learn more about how to safeguard your valuable data.
-1.png?width=760&height=300&name=httpswww.usecure.ioenfree-employee-phishing-test%20(1)-1.png)