The 8 types of phishing attack that could target your business
Phishing makes up the majority of cyber attacks targeted against businesses. In order to save time, money and damage to brand reputation that could be caused by a cyber breach, it is essential that businesses understand the types of threats targeted against them - and how to counteract them.
In this article, we will look at the different types of phishing attacks that target companies around the world every day, and how you can help your business stay safe.
What are the different types of phishing attacks?
While new phishing scams are crafted by cyber criminals every day, most scams fall into one of the major common types of phishing. Below, you'll be able to read more about and see examples of each type of phishing attack.
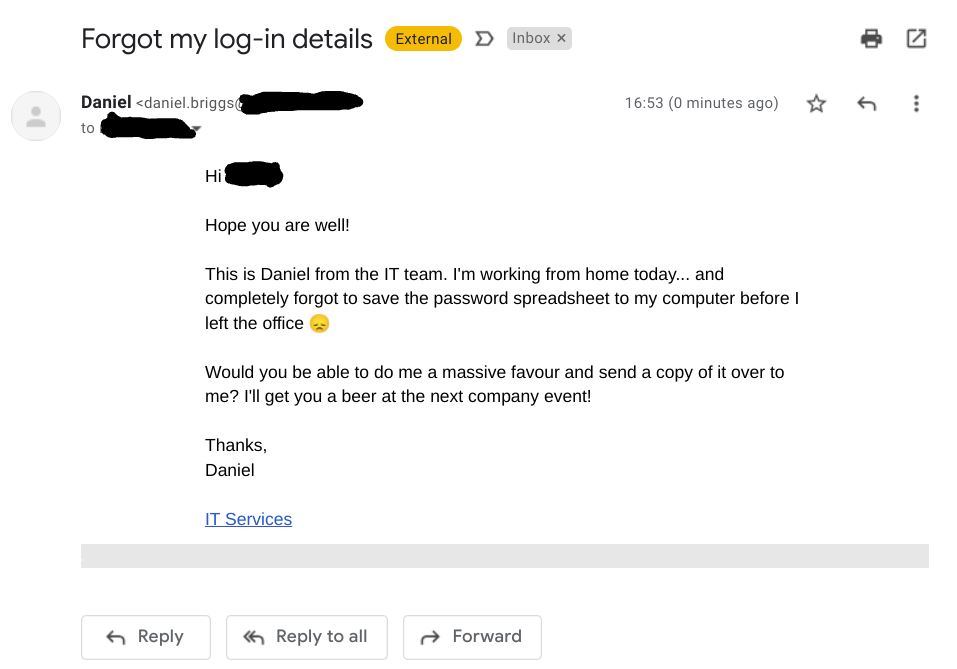
#1 - Spear phishing
Spear phishing emails are targeted at specific companies or groups of people. They are customised with the target audience in mind to be highly believable and likely to get the victims to click on the links provided in the email.
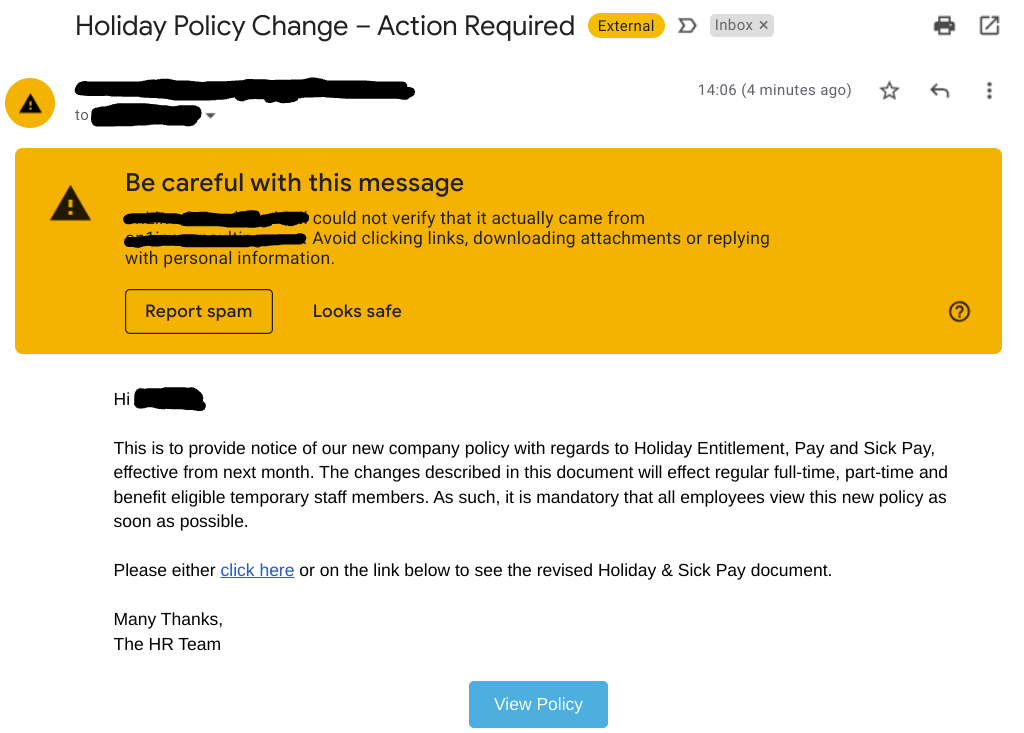
This example spear phishing email poses as a message from the company's HR department, and uses a custom domain name and a highly-engaging topic in an attempt to get its victims to overlook security and give up their details.
- Read more about why spear phishing is a threat to every business
#2 - Whaling
Whaling is a type of phishing attack aimed at high-value targets such as senior executives. These lucrative targets are called 'whales' due to their access to company funds and sensitive information.
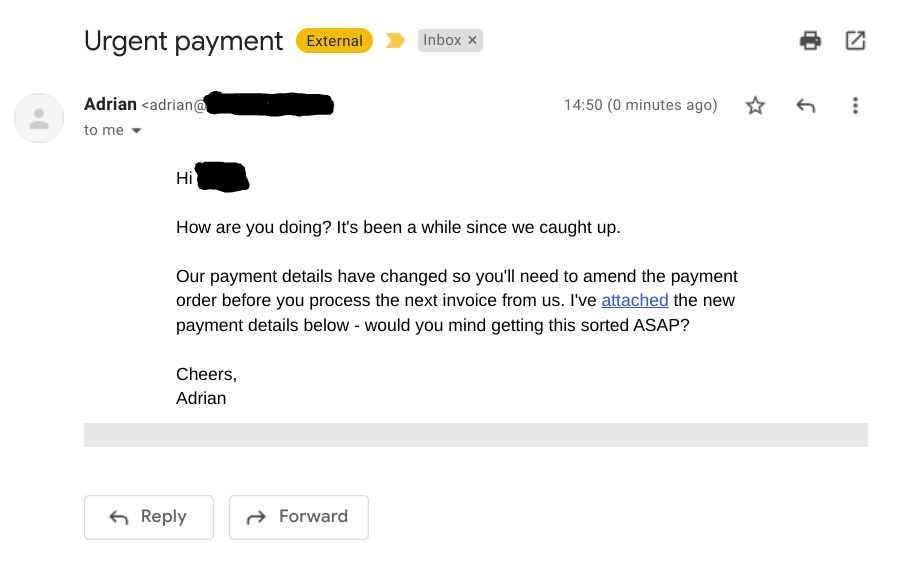
This example whaling email is aimed at a finance manager. It purportedly updates the target with payment details from a vendor - but actually contains payment details that would lead the payments directly to the cyber criminal's account.
- Read more about staying safe from whaling emails
#3 - Smishing
Smishing attacks take place over SMS text messages, though other types of chat- and message-based phishing attacks are also often included in the definition. Smishing attacks make use of the fact that text-based messages lack sender domains and branding that could otherwise be easy tells of a message's illegitimate origins.
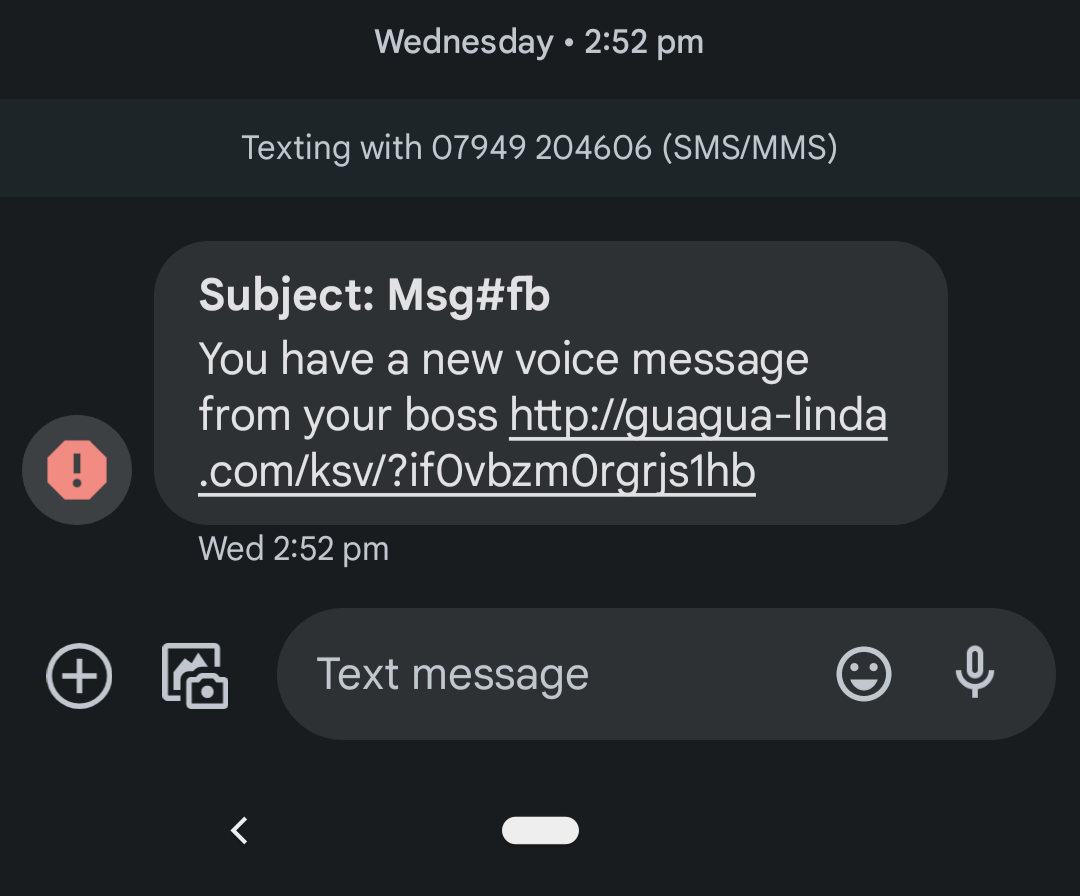
The below smishing message claims to be a message from the recipient's boss. While smishing messages often claim to be from banks or utility companies asking for a bill to be paid, this is an example of a business-related smishing message that is becoming more and more common.
- Read more about the rising threat of smishing attacks
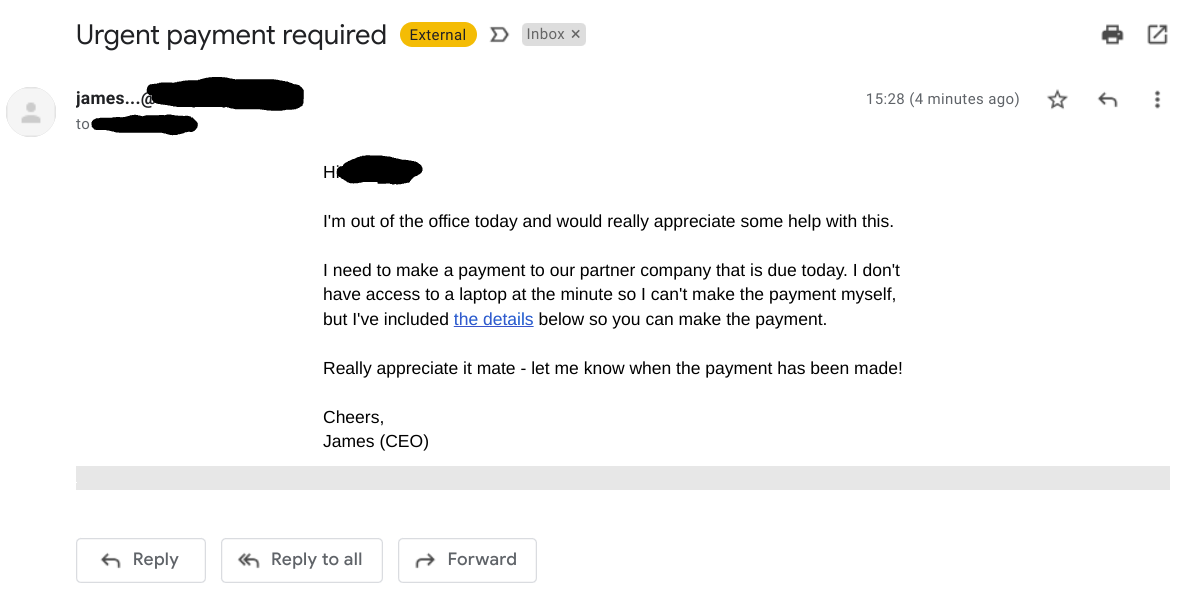
#4 - CEO Fraud
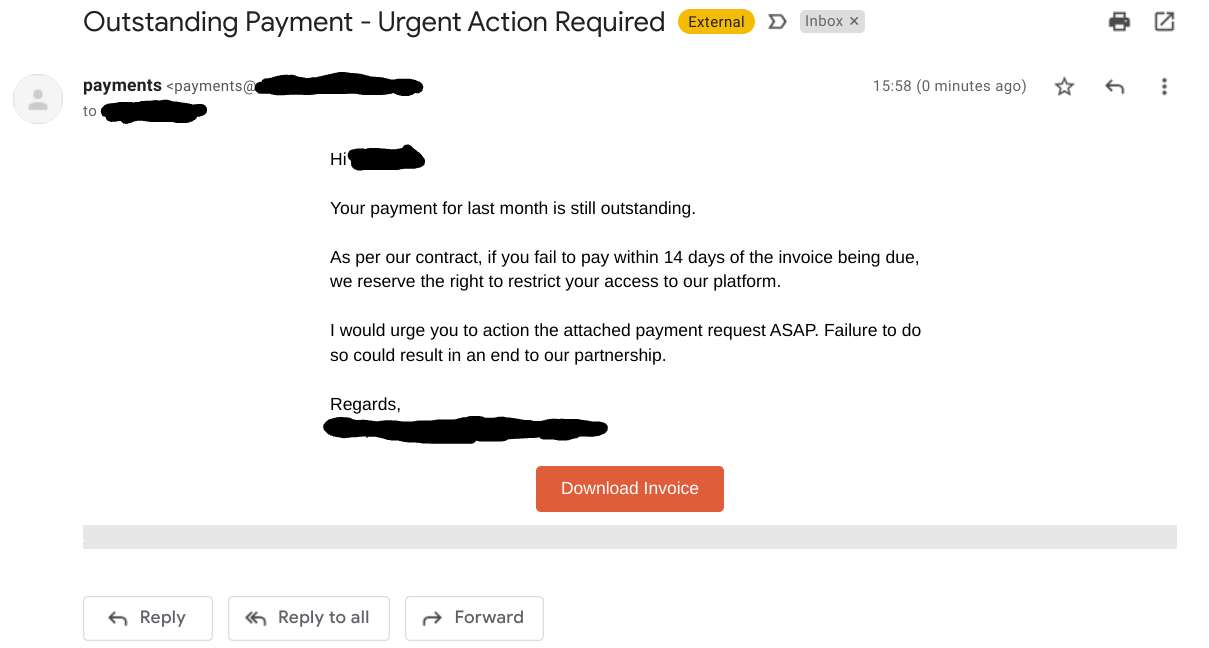
In a CEO Fraud scam, a cyber criminal sends an employee an email that claims to come from the company's Chief Executive Officer. Due to the authority held by the CEO, the employee is likely to urgently take any action set out in the email - such as carrying out a payment to a new bank account - as long as the attacker manages to dupe them with a similar looking domain and a realistic-sounding email.
#5 - Business Email Compromise (BEC)
A Business Email Compromise (BEC) is a scam where a criminal poses as a business partner, customer or vendor of the target recipient. These types of phishing attack make use of business terminology and often involve detailed research and long chains of messages to make the scam believable.
#6 - Vishing
Vishing scams take place over the phone or voice messages. In the most common form, the perpetrator poses as a partner firm, vendor or supplier of the target employee's company, and urges the victim to make a payment or to divulge sensitive information. Due to the perceived authority possessed by the caller, the victim is likely to overlook the fact that they can't be sure of the caller's identity, and perform the action requested by the criminal.
#7 - Pretexting
Pretexting - also called social engineered phishing - is the use of a 'pretext' or a story to dupe a victim into making a payment, giving up credentials or letting the attacker into a company system. This type of scam involves the attacker taking on a role that they play throughout the attack in order to make the scam more likely to succeed. As most people are naturally helpful and want to assist someone with a relatable story, it is easy to fall for these type of scams.
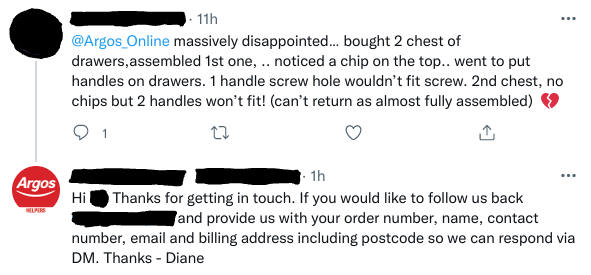
#8 - Angler phishing
Angler phishing attacks take place over social media. In this scam a criminal creates an account that looks similar to a known brand, and replies to the public messages of users complaining or otherwise talking about the brand on the social media site. Impersonating a customer service agent, they either send the user a link that leads to a malicious website, or continues the conversation with them in direct messages where they can harvest their personal details.
How to keep your business safe
The number of phishing threats targeting businesses increases year by year. Phishing is now the number one entry vector that cyber criminals use to intrude business networks, and it is essential that every organisation takes the appropriate measures to protect themselves, their devices and their data.
There are a number of technical measures that can seriously clamp down on the number of phishing emails that reach users' inboxes. However, spam filters and intelligent detection will never be able to stop every single scam from reaching users, and thus addressing the human factor is necessary to reduce the chances of a damaging breach affecting your business.
Addressing the human factor is compromised from three parts: education, testing and culture. First, users must be educated on the risks of phishing and how to detect suspicious emails. Secondly, users have to be tested - not only to gauge how well they have taken up their learning, but also because practical learning is one of the best ways to increase learning retention. And thirdly, your business needs to promote a security culture where users feel rewarded for putting security first and asking questions if they're ever unsure.
.png)
