How to monitor the dark web for compromised employee credentials
In today's world, employee credential theft is a growing concern for organisations globally. Cybercriminals are targeting sensitive data for malicious purposes on the dark web.
In recent years, there has been a 429% increase in the number of corporate login details with plaintext passwords exposed on the dark web. This highlights the urgent need for businesses to take proactive steps to mitigate the risks associated with compromised employee credentials.
In this blog, we'll explore effective strategies and tools to help companies locate stolen employee credentials on the dark web and prevent these credentials from falling into the wrong hands.
In this article, we'll cover:
- What is dark web monitoring?
- Why should you monitor the dark web for compromised credentials?
- How do dark web monitoring tools work?
- The types of credentials often found through dark web monitoring
- Choosing the right vendor for dark web monitoring
- Get started with a free dark web scan
What is dark web monitoring?
Dark web monitoring is the process of monitoring the dark web -- a part of the internet that is not indexed by search engines. Dark web monitoring is crucial to ensure an organisation's data remains secure because stolen or compromised data could pose a serious threat to the businesses.
“People don’t seem to realise just how often their credentials end up in criminal hands or how stolen passwords can be used to access other accounts they think are safe.”
Chip Witt, Vice president of product management from SpyCloud
Why should you monitor the dark web for compromised employee credentials?
One of the most significant threats to companies is the exposure of employee credentials on the dark web. Employee credentials refer to login information such as usernames, passwords, and other sensitive information that employees use to access company systems and applications.
The dark web is a haven for cybercriminals who trade stolen personal and corporate information.
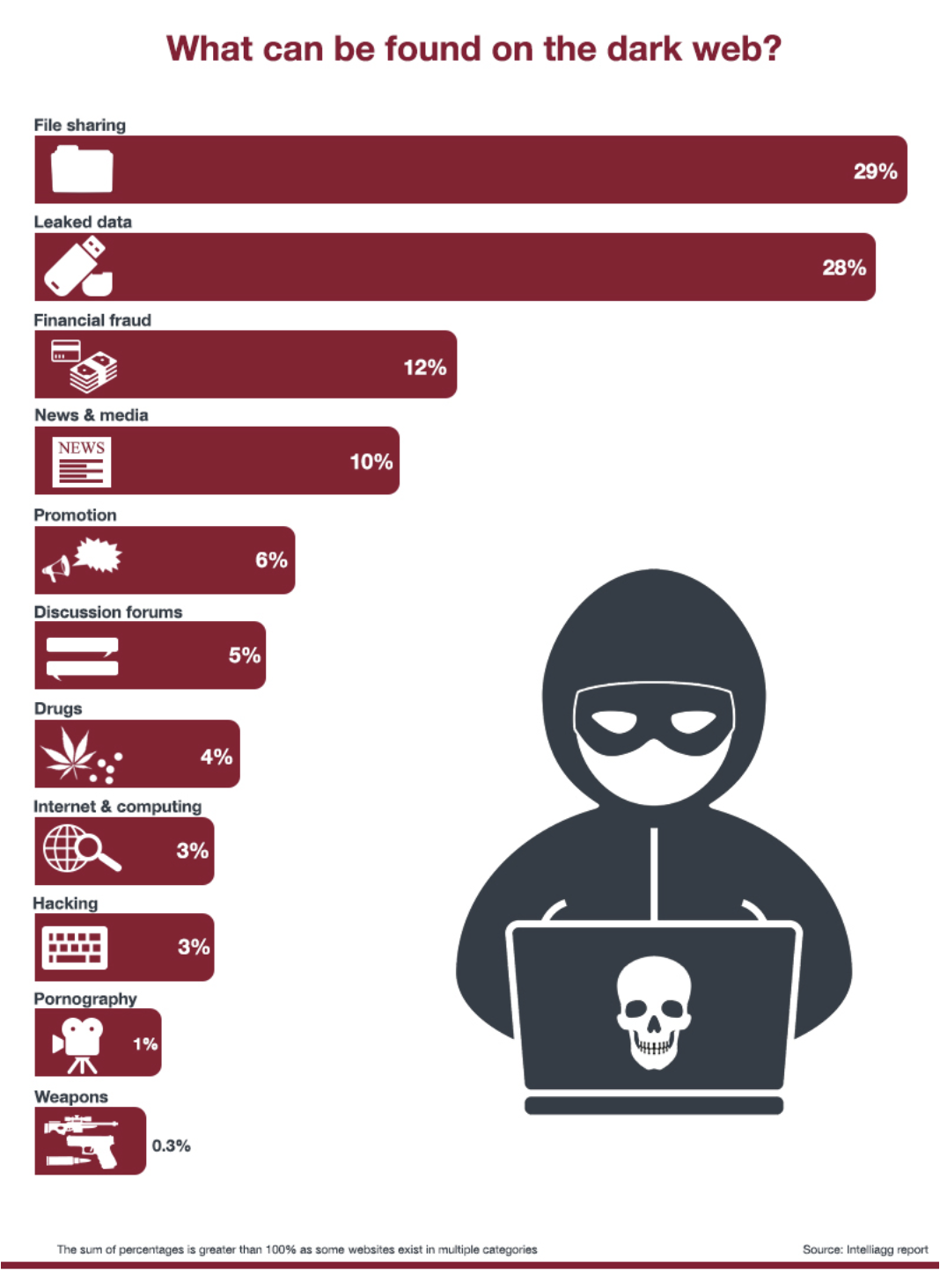
Failing to mitigate the threat of exposed credentials on the dark web can lead to a number of headaches for businesses, including:
-
Data breaches: When cybercriminals gain access to a company's network using compromised credentials, they can steal sensitive information, such as customer data, financial records, and intellectual property. This can result in significant financial losses and damage to the company's reputation.
-
Financial fraud: Cybercriminals can use compromised credentials to conduct financial fraud, such as making unauthorised transactions or accessing company bank accounts.
-
Ransomware attacks: Ransomware is a type of malware that encrypts a company's data and demands payment to release it. Cybercriminals can use compromised credentials to gain access to a company's network and deploy ransomware, causing significant disruption and financial losses.
-
Reputational damage: A data breach or other cyber attack can damage a company's reputation, leading to lost business, legal action, and long-term damage to the brand's image.
-
Compliance violations: Many industries are subject to data protection regulations, such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA). Compromised credentials can lead to violations of these regulations, resulting in significant fines and legal action.
It's important for businesses to monitor the dark web for exposed employee credentials. By doing so, companies can proactively identify and respond to potential cyber threats before they cause harm.
How do dark web monitoring tools work?
Dark web monitoring tools work by continuously scanning the dark web for any data that may be relevant to an organisation. This includes data such as employee credentials, credit card numbers, and other sensitive information that may be stolen and sold on the dark web. We'll go into more detail later in this blog.
Once the tool identifies any data related to the business, it performs a series of checks to determine if the data is legitimate and if it poses a risk to the business. If the data is verified as legitimate, the tool will generate an alert, notifying the business of the compromised data.
Here is what dark web monitoring does for businesses:
-
Scan the dark web: The first step in dark web monitoring is scanning the dark web to identify any stolen or compromised data related to the business. This is typically done by using specialised software that can search through the dark web's hidden websites, forums, and marketplaces.
-
Identify compromised data: Once the dark web is scanned, the software identifies any stolen or compromised data related to the business. This can include login credentials, personal information, financial information, and other sensitive data.
-
Alert the business: Once compromised data is identified, the software alerts the business of the potential threat. This allows the business to take immediate action to secure any affected accounts, reset passwords, and investigate any potential breaches.
-
Breach report: Dark web monitoring software provides businesses with detailed reports on any compromised data found on the dark web. These reports can help businesses identify vulnerabilities in their security systems and take proactive measures to strengthen their defences.
-
Ongoing monitoring: Dark web monitoring can continuously monitor the dark web for new threats. This helps businesses stay ahead of cybercriminals and avoid potential data breaches.
Types of credentials often found through dark web monitoring tools
Dark web monitoring can uncover various types of employee credentials, including:
-
Usernames and passwords: Cybercriminals frequently steal login credentials and sell them on the dark web. These credentials can give them access to the business's network and sensitive data.
-
Personally identifiable information (PII): PII such as names, addresses, and Social Security numbers can be used to steal identities or commit other forms of fraud.
-
Email addresses: Business email addresses can be used for phishing attacks or spamming.
-
Financial information: Credit card numbers, bank account information, and other financial information can be used for fraudulent purchases or identity theft.
-
Security question answers: Cybercriminals can use security question answers to reset passwords and gain access to employee accounts.
-
Healthcare information: Medical records, insurance details, and other health-related information can be used for identity theft or fraudulent medical claims.
- Subscription service credentials: Logins for streaming services, social media accounts, and other subscription-based platforms can be stolen.
- Access badges: Information or copies of digital badges that grant access to a company's network if compromised.
Choosing the right vendor for dark web monitoring services
When employee credentials are leaked, your business and reputation could be at risk. Therefore, knowing how to find stolen employee credentials on the dark web and take proactive steps to protect your data is essential.
However, not all dark web monitoring services are created equal; choosing a reputable provider that has a track record of success is crucial.
Some security software vendors offer dark web monitoring services as a part of a larger cybersecurity strategy that includes employee training, simulated phishing and policy management. These services can provide more comprehensive protection for businesses.
Get started with a free dark web scan
Cyber threats are becoming more sophisticated every day. Don't wait until too late! Learn more about how to implement dark web monitoring in this blog or sign up for a 14-free trial of our dark web monitoring tool, uBreach.
uBreach Pro will scan the dark web for any compromised employee credentials related to your business, providing you with real-time alerts and detailed reporting. By using our tool, you can stay ahead of cybercriminals and protect your data and employees from potential cyber threats.

.png)
.png)