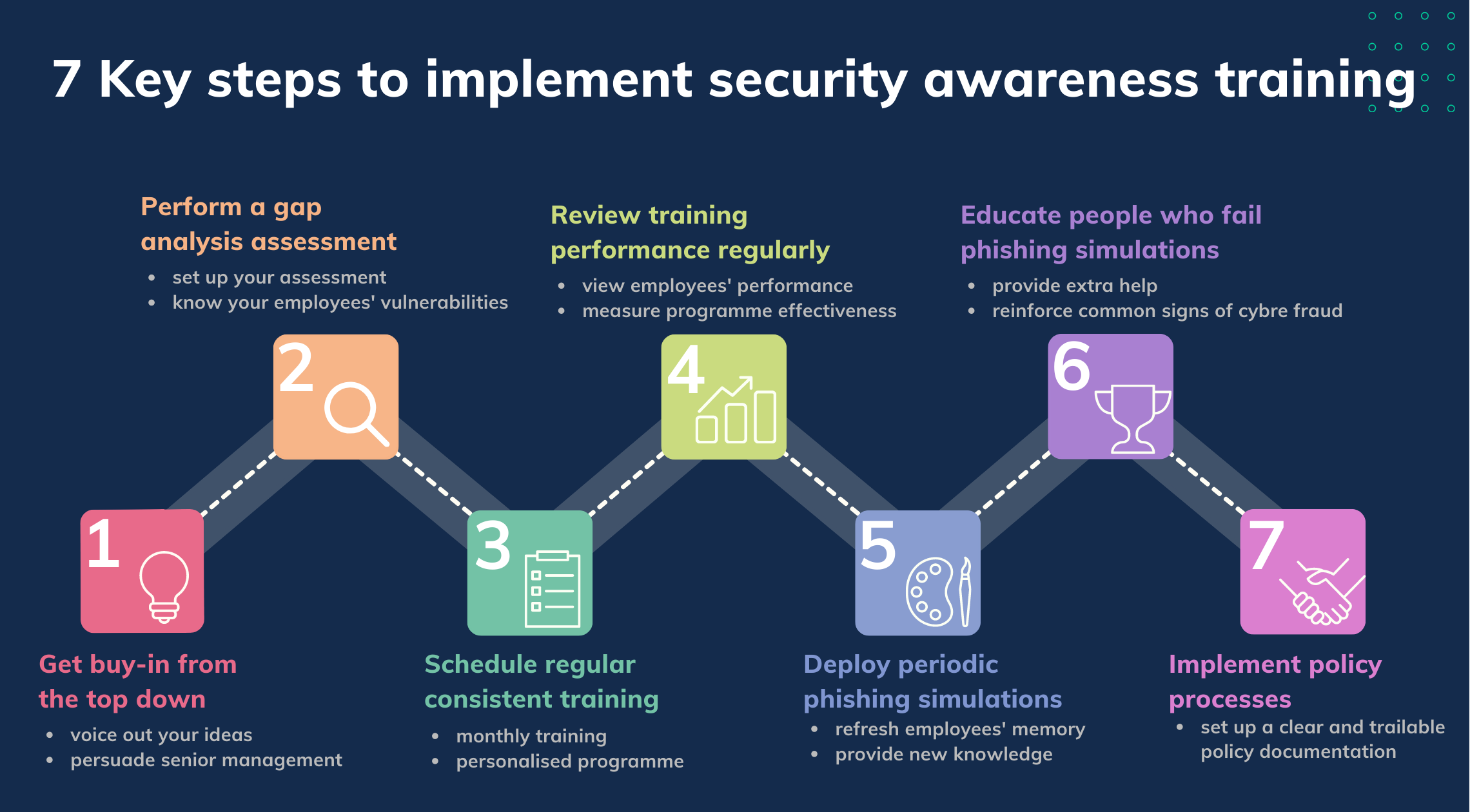
7 Key steps to implement security awareness training
Table of content
Introduction to the 7 key steps
- Step 1: Get buy-in from the top down
- Step 2: Perform a gap analysis assessment
- Step 3: Schedule regular, consistent training
- Step 4: Review training performance regularly
- Step 5: Deploy periodic phishing simulations
- Step 6: Educate people who fail phishing simulations
- Step 7: Implement policy processes
Words of wisdom from the CEO of IBM
Introduction to the 7 key steps
Security awareness training is important to bringing attention to cyber crimes. It is becoming a popular strategy used by IT professionals to guard their organisations against security breaches caused by human errors. However, building a training programme requires a lot of work. Very often than not, threats are pressing but training plans are still pending because of technical difficulties. We understand the pain so we are going to give you solutions and break down the complicated process into 7 key steps. Follow us to establish a customised training programme now with minimal resources.
Step 1: Get buy-in from the top down
Find the right time to voice out your ideas and concerns about your company’s network security to your senior management. Explain why security awareness training is essential in today’s world and its benefits. Tailor the pitch and sharpen your message by blending in the organisational goals or values. Once the company leaders see how your initiative fits into the big picture, they’ll be more willing to devote resources to it. Take reference from our article, and learn how to persuade the senior management in order to get a budget.
Getting support with a top-down approach can help you quickly acquire needed material and resources. It will also empower you to get authority and credibility to increase the likelihood for employees to adopt the training.
Step 2: Perform a gap analysis assessment
It's critical to perform a gap analysis to assess potential human risk and security awareness vulnerabilities in your organisation. Set up your assessment as below:
-
Identify the area to be analysed
For example, you may want to figure out why your employees kept falling for phishing emails.
-
Establish the ideal future state
For example, if no staff fell for phishing emails, how much would you be able to save every year? -
Analyse the current state
For example, what causes contribute to the problem? Are the workers well-trained enough? -
Compare the current state with the ideal state
For example, how many employees had fallen victim to cyber fraud when you expected no one to do so? -
Create a plan to bridge the gap
For example, determine the most effective and efficient way to fix things. There are many well-designed training programmes available to choose from. You just need to pay a reasonable fee and programmes will do all the work to train your employees to be your strongest cyber crime fighters.
By doing a gap assessment, you will get an in-depth understanding of which employees are at the top priority for training and which improvement areas should be taken into account. You'll be able to identify the current state and devise a plan of action to achieve the desired future state.
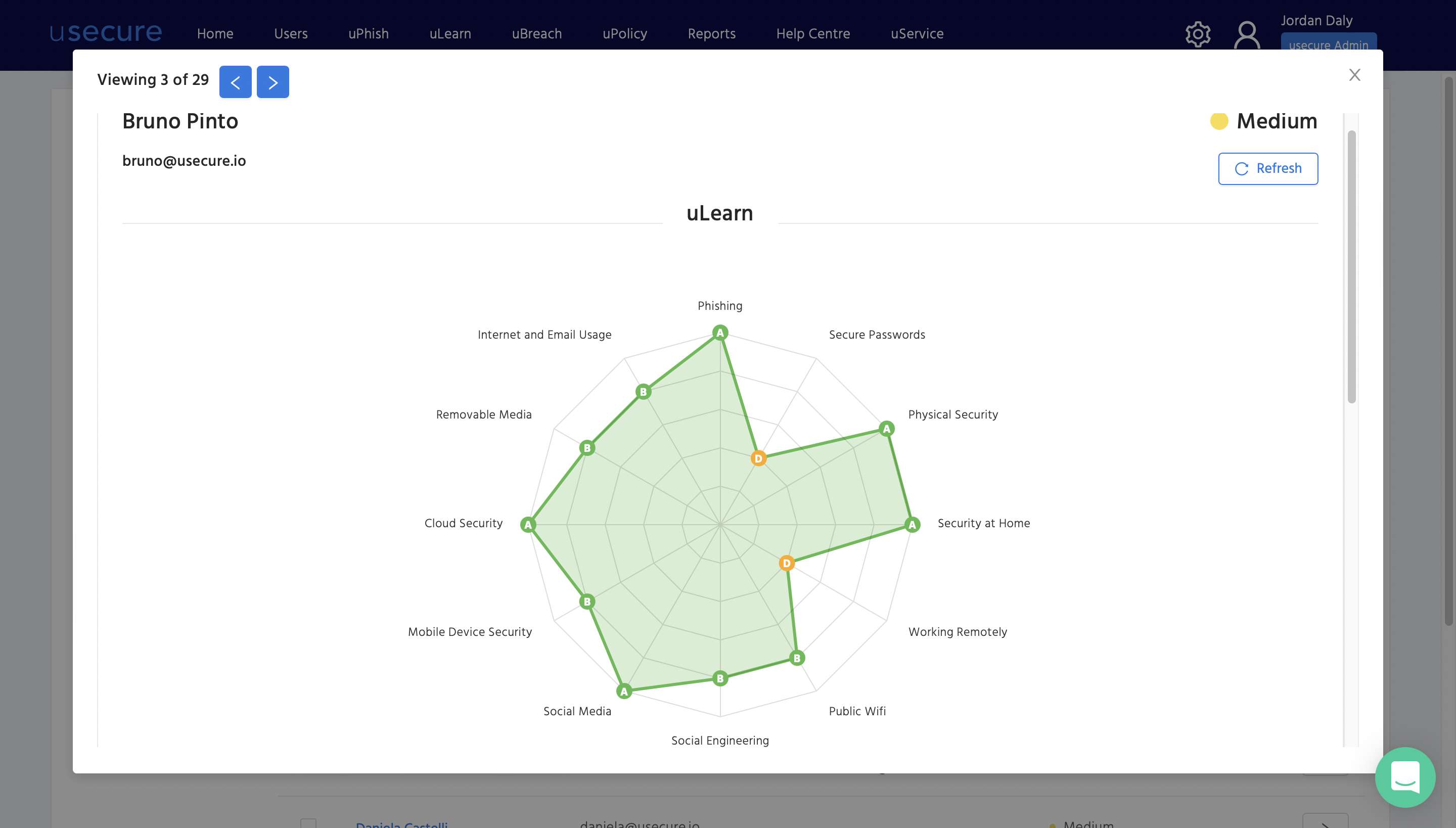
Below is an example of how you can conduct a quick gap analysis assessment using usecure. Once your people have been enrolled, usecure sends out a short, 10-minute questionnaire which highlights each individual's security knowledge gaps in core areas of information security.
Step 3: Schedule regular, consistent training
How often should employees receive training? More and more businesses are finding that monthly security awareness training is the most effective approach for educating all staff on new threats whilst maximising their knowledge retention. We’ve put together third-party research and findings in another blog post for your review, to let you know more about the ideal frequency.
Pro-tip for you:
There are hundreds of choices on the market for security awareness training software, but to pick the most suitable one, look for those that allow you to choose and set personalised training, rather than a ‘one-size-fits-all’ programme.
Step 4: Review training performance regularly
Regardless of what type or frequency of training you are providing to your employees, it is important to regularly review their performance. It assists you to understand exactly where they stand and what they should do to improve. You can further cultivate them with real-time coaching and help them overcome obstacles.
Most security awareness training programmes on the market carry a set of criteria to help managers define every employee’s learning effectiveness. Some even provide short tests or assessments to evaluate employee performance and determine where they should go next. These are important functions you may like to consider.
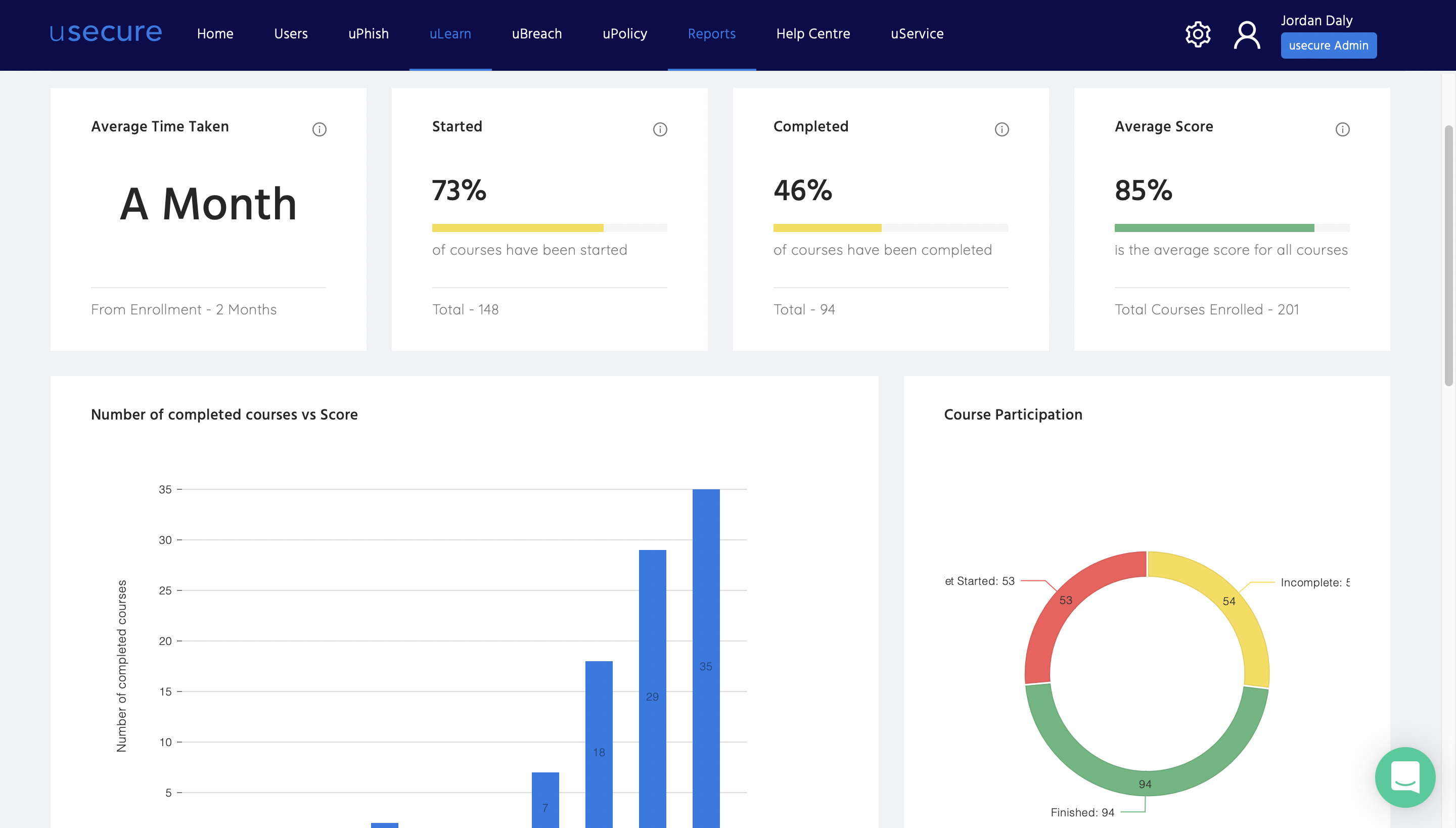
With usecure, you get access to key metrics and insights that help you measure the impact that the training is having, including ongoing adoption rates, performance grades and changes over time.
Step 5: Deploy periodic phishing simulations
Every skill requires regular practice, otherwise, mastery over it is lost. This is especially true in today's ever-changing cybercrime landscape, one-off employee training is not enough and periodic phishing simulations should be deployed regularly. They serve as refresher courses which not only help your employees sharpen the skills they have already learnt but also enable your organisation to measure the improvement your employees made along the training journey.
Step 6: Educate people who fail phishing simulations
Indeed, training is increasingly important and many leading companies are adapting to the trend and requiring phishing training for employees. However, many of these companies received no guidance on what to do with their employees who fail the training.
Employees failing phishing tests is a warning sign for companies, those who face repeated failures should be dealt with even more carefully. IT managers can educate an employee to be more vigilant to suspicious emails. Implementing remedial measures, such as reinforcing the common signs of phishing emails, is an effective method to ensure that such employees do not fall prey to real phishing attacks.
Pro-tip for you:
To ensure employees properly digest the information provided by the training, you should look for bite-size designed programmes that reassert a few core messages at a time to help employees consume quickly.
Step 7: Implement policy processes
Last but not least, implementing a clear and trailable policy documentation is the key to a better security foundation. IT Managers often need to send out different types of documentation to employees, to make sure they understand the policies and agree to follow them. Some security awareness training programmes offer a wide range of readily-made policy templates, such as email policy, password policy or encryption policy, etc. These templates can save IT Managers a great amount of time and effort. Also, they can usually be edited to better fit particular organisational needs.
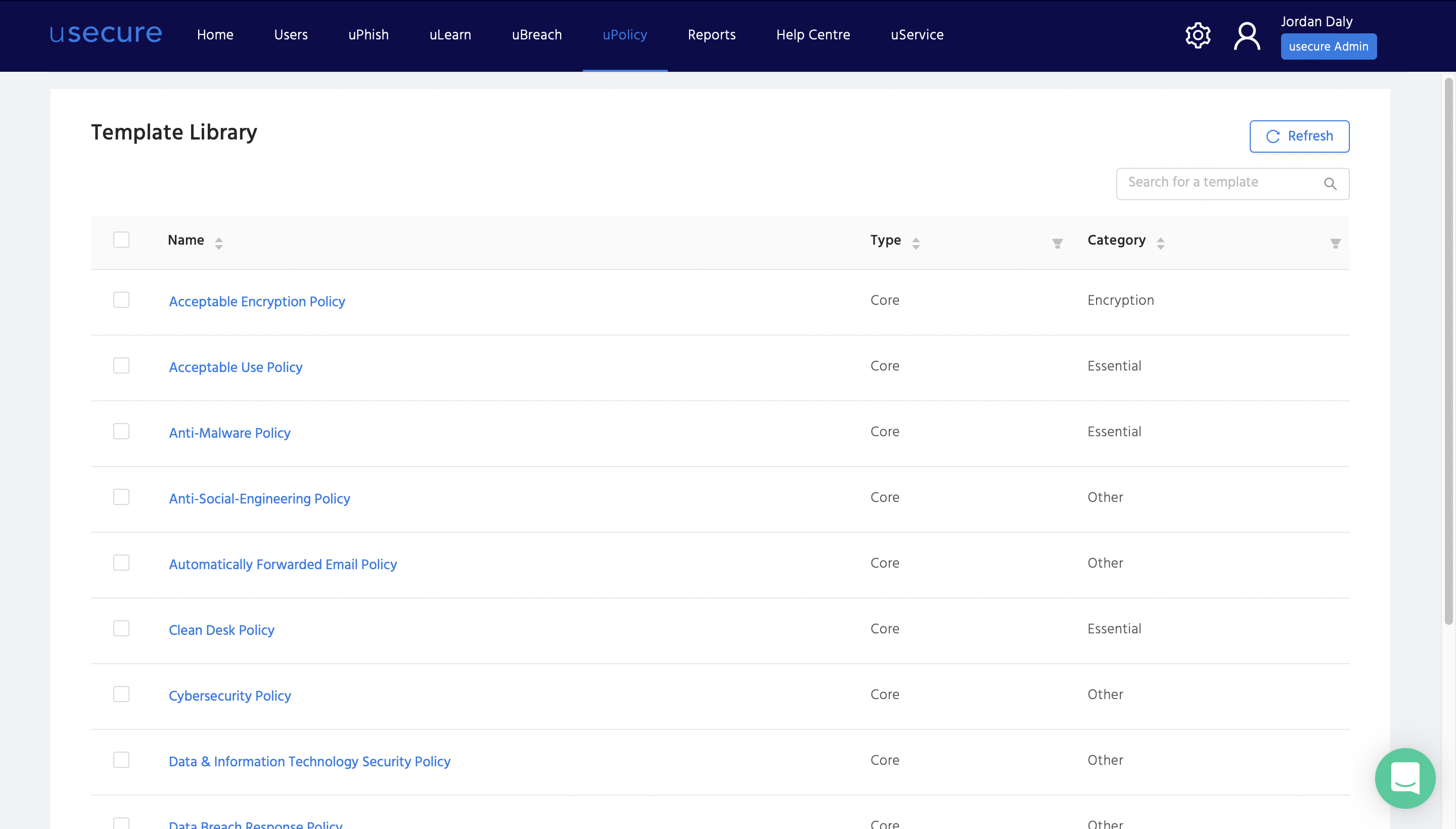
Software with a tracking function can provide IT Managers with a clear overview of employees' progress in responding to policies. So that managers know whether the policies have been viewed and signed. Some advanced training programmes even allow IT Manages to set automatic rules and send policies to specific employees at a specific time, to make sure no targeted employee is being left behind.
“Cybercrime is the greatest threat to every company in the world.” — Ginni Rometty
These words of wisdom are from the former Chairman, President and CEO of IBM. The threat is real and we need better defences. Security awareness training is what you need to empower your workforce and secure your business. Follow this 7-step roadmap, and start looking for a training programme that would suit your organisational needs.
usecure Demo Hub
Want to launch ongoing security awareness training that is engaging, non-disruptive and easy to manage? Watch a quick on-demand demo to learn how usecure creates user-tailored security awareness training programmes in a flash, automates ongoing enrolment, and tracks the impact of the training through meaningful metrics.
.jpg?width=760&name=SAT%20Blog%20CTA%20Images%20(1).jpg)
.png)
.png)