The complete guide to security awareness training [+ free eBook]
The Covid-19 pandemic has posed many security challenges. Businesses around the world have adjusted to working from home and social distancing, while also dealing with new threats posed by cyber criminals exploiting fear and curiosity.
Even as companies have dealt with these challenges, traditional cyber threats have been as prevalent as ever, making for an increasingly challenging threat landscape.Mitigation of human error must be key to business cyber security in 2022 and, in this guide, we’ll look at the best ways to go about it.
Here's what you'll learn:
How human-targeted attacks
are set to evolve in 2022
Phishing & malware
Among the major cyber threats, malware remains a significant danger. The 2017 WannaCry outbreak that cost businesses worldwide up to $4 billion is still in recent memory, and other new strains of malware are discovered on a daily basis. Phishing has also seen a resurgence in the last few years, with many new scams being invented to take advantage of unsuspecting companies, from larger enterprises to small businesses. Just one variation, the CEO Fraud email scam, cost UK businesses alone £14.8m in 2018.
Working from home
Staff working from home are outside the direct oversight of IT support teams, and often struggle to deal with cyber threats and appropriately protect company information. Failing to update software and operating systems, sending data over insecure networks, and increasing reliance on email and online messaging has made employees far more susceptible to threats ranging from malware to phishing.
Human error
While technical solutions like spam filters and mobile device management systems are important for protecting end users, with the number of threats and the multitude of systems and communications through which staff perform work, the one unifying risk factor that has to be addressed to fundamentally improve security is the role of human error.
Why human error remains the
#1 security threat to your business
Almost all successful cyber breaches share one variable in common: human error. Human error can manifest in a multitude of ways: from failing to install software security updates in time to having weak passwords and giving up sensitive information to phishing emails.
How human error leads to data breaches
Even as modern anti-malware and threat detection software have grown more sophisticated, cyber criminals know that the effectiveness of technical security measures only go as far as they are properly utilised by humans. If a cyber criminal manages to guess the password to an online company portal, or uses social engineering to get an employee to make a payment to a bank account controlled by the cyber criminal, there is nothing that technical solutions can do to stop that intrusion.
In 2014, IBM conducted a study into the cyber breaches that occurred among thousands of their customers in over 130 countries. This study was the most wide-reaching look into the causes of cyber breaches that had been performed at that point, but its results have since been corroborated by similar studies.
Human error was a major contributing cause in 95% of all breaches.
IBM Cyber Security Intelligence Index Report
One of the key findings of the IBM study was that human error was a major contributing cause in 95% of all breaches. In other words, had human error not been a factor, the chances are that 19 out of 20 breaches analysed in the study would not have happened at all.
Since human error plays such a vast role in cyber breaches, addressing it is key to reducing the chances of your business being successfully targeted. It also allows you to protect your business from a far wider range of threats than any single technical solution could - and can potentially empower your workforce to actively look out for and report new threats they may encounter. Mitigation of human error must be key to business cyber security in 2022 - and in the next section, we’ll look at the best ways to go about it.
When does human error take place?
Two factors have to be present in order for human error to manifest:
- Opportunity
- Decision
Opportunity means that there is a situation where a human is allowed to make a mistake: for example, letting end users handle software updates rather than forcing security updates through with patch management. Decision is the action of the individual: in this case, the lack of action in installing security updates when they are available.
Reducing opportunity & improving decisions
A comprehensive mitigation effort includes both reducing the opportunity for error as well as improving the decisions made on the part of the end users. Taking action in both areas is essential to ensure that human error is thoroughly addressed and that compliance is achieved through core security standards, such as ISO 27001 and PCI DSS.
In the case of patching, for example, a technical measure such as introducing patch management may reduce the opportunity for human error to a minimum in most cases - but it is still essential to account for situations where the technical solutions have a temporary lapse, or if a new situation such as a BYOD policy where users are allowed to use their own devices without patch management is introduced.
In other cases, such as with phishing emails, technical measures such as spam filters and breach detection software have a very limited effect in reducing the opportunity for error when faced with a targeted attack. In those cases, the only effective way to mitigate human error is by teaching end users how to make better judgments.
How can you reduce human error?
In order for end users to make the right judgement in a security situation, four different factors have to be present.
4 pillars for reducing human error: |
|
The first of these is quite straightforward: the user has to recognise that they are in a situation where security is potentially at stake. Without recognising the situation as such, the user may not even realise that they are making a decision at all through their inaction.
#2. Empowerment
Secondly, the user has to know what the correct course of action is. This doesn’t necessarily require the user to completely understand the threat, but often is as simple as reporting the situation to a person in the IT or security department who can look into it.
#3. Education
Thirdly, the user must know why security matters, so they understand the importance of not ignoring security procedures and are aware of the potential implications of a breach. While these three factors are all essential for improving security outcomes, it is at this crucial point that businesses often falter. In order for better decisions to be made in real-world situations, the fourth factor must also come into play: pain avoidance.
#4. Eliminating pain avoidance
Issues such as weak password security and failure to patch software persist in organisations across the world, despite many computer users understanding why these issues are critical to security. The reason that action is not taken despite knowledge is due to what we refer to as pain avoidance. Having a unique and strong password requires more time to create, and more effort to remember, than a short, weak, or reused password.
Despite a user knowing better, this ‘pain’ caused by creating a strong password is often strong enough to make the user go against their best judgement. This is compounded by the fact that, despite many users taking the correct action under optimal circumstances, busy and urgent work situations as well as stress can make security measures feel even more ‘painful’ to users.
Driving cultural change
It is this last factor that can only be resolved through cultural change. End users have to feel that the pain caused by following security best practices is less than the satisfaction gained by not doing so.
Technical measures such as password managers are essential in this, as they make acting in a secure manner far easier: if employees don’t have to create or remember their own passwords, they have no reason not to use secure ones. Simultaneously, the threshold for performing the correct action must be lowered through cultural change. This means putting security at the forefront of decision making, and ensuring that users never feel they are ‘wasting time’ by taking appropriate security precautions.
Security should be discussed among employees, and questions and points that end users bring up about security issues in their own roles should be paid attention to and rewarded. This helps users feel like security isn’t just an afterthought, but something that is always worth spending the time on.
Effective security awareness training addresses not one, but all four of these factors.
Effective security awareness training addresses not one, but all four of these factors. This means identifying situations where data or systems could be compromised, understanding best practices, knowing what the potential consequences of breaches are, and finally helping to push through a cultural change to create an environment where security considerations are always taken into decision making.
Keeping staff security-savvy
when working from home
The global response to the Covid-19 pandemic has caused many changes in workplaces. The change that has had the most significant impact on security has been the transformation of many businesses to having most or all of their staff switch to working from home within a short period of time, which has led to many end users being at higher risk of succumbing to online threats.
The security risks of working from home
Employees that weren’t used to working from home before the pandemic quickly discovered some of the issues that it would cause: having to look after children and pets, dealing with poor internet connectivity, and putting up with all the other disturbances that can happen at home. In the midst of all these new changes to the working environment, security too often fell to the bottom of users’ priority lists.
End users that work from home are out of the oversight of the IT support department, and may struggle with simple tech-related issues. In addition, essential security tasks like updating software and operating systems, updating router firmware and securing the network, were suddenly placed into the hands of end users. It’s no wonder that cyber criminals haven’t wasted a second in exploiting the circumstances of the pandemic to come up with new forms of scams and cyber crime.
How to address security when
end-users are at home
The IT support team can’t be at every end users’ home, which is why it is essential to ensure that, in addition to having the right equipment, end users are aware of their individual responsibilities in keeping up security. End users need to know that they are responsible for ensuring that they only access company information and networks on devices and networks that are up-to-date and secure.
Security awareness training is key to ensuring that end users know how to keep up security. It’s best to break up training into small, digestible components, as this ensures that users aren’t overwhelmed.
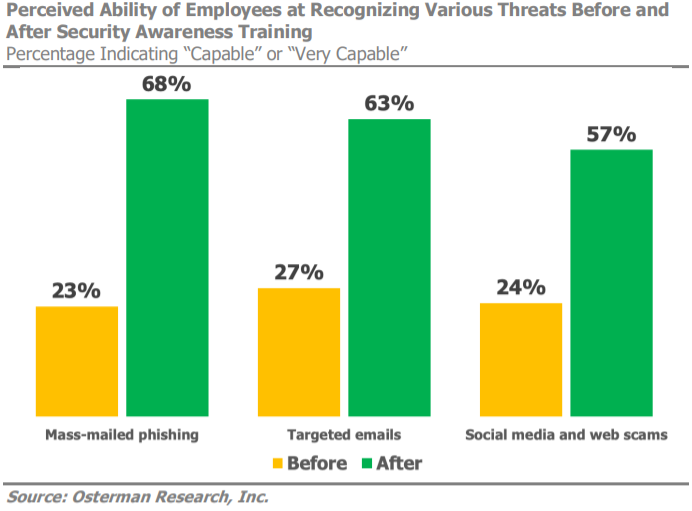
Training should also take place regularly - once a month, at the minimum - to ensure that key learning is retained and that users won’t forget about security as soon as the next work project comes along that shakes up the list of priorities. Lastly, it is important to test end users. As the report shows below, many businesses are opting to train staff on a monthly basis to keep information fresh in the mind.
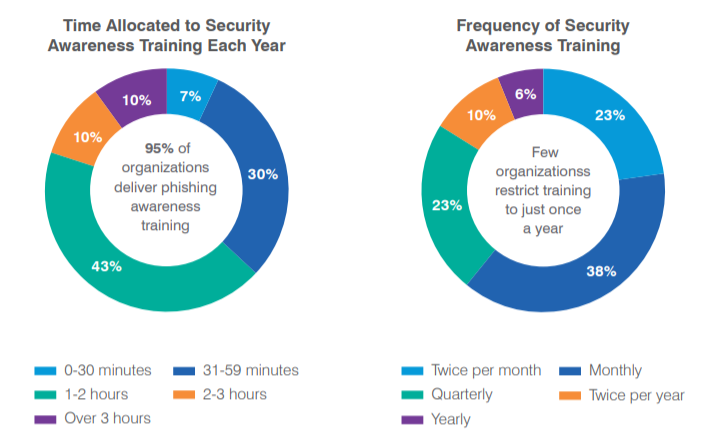
It should be made clear that this isn’t for judging or penalising users who struggle with their training, but rather to identify key security gaps across the workforce, and address these before they can be exploited by cyber criminals.
What's the best format for
security awareness training?
There are many different types of security awareness training that can be deployed in different ways. TThe way in which training is performed, structured and presented will have a major effect on its effectiveness in genuinely improving security outcomes in your organisation. In this section, we’ll take a look at what exactly is the best way to perform security awareness training for your end users.
Old-school VS modern training
Security awareness training used to mean making end users sit through an annual session consisting of hours of lectures and slideshows. The idea was that users would remember something of what they saw and heard - and in the worst-case scenario at least the box for ‘educating users’ could be ticked. How did it far in actually improving security outcomes though? It didn’t work, and everyone hated it.
There are a number of reasons why this type of annual lecture-based training isn’t effective. The first of these is that in an annual training session, there will simply be too much information at once for any employee to digest and remember. Even if users are given learning material to take with them or are sent occasional reminders, chances are that most of the material in the training session will go in through one ear and out the other - forgotten in mere moments.
Lectures and slideshows are simply not engaging formats for end users to learn.
Lectures and slideshows are simply not engaging formats for end users to learn from. They fail to raise the interest of employees in the same way that video and interactive content do, and too often are filled with unnecessary information that isn’t relevant to every end user. Slides filled to the brim with small text are sure to make any employee fall asleep halfway through the session.
The final, major reason why traditional training isn’t effective is that it doesn’t make use of learning through repetition. If there is a year between learning sessions, users simply won’t remember what they’ve learned - and awareness of security issues, in general, will plummet in the days and weeks after training. Security can’t be a one-time thing, but must be year round in order to be effective.
Security awareness training has increasingly shifted to online software-as-a-service solutions. Cloud-based training offers some immediate benefits over traditional methods but isn’t necessarily the ultimate answer to security awareness unless it delivers in certain areas that are essential for genuinely improving security outcomes.
How to make training truly effective?
Having a truly effective security awareness training program is possible, even on a tight training budget - but there are some important criteria you need to follow to genuinely engage your users.
7 steps to successful security awareness training: |
|
Breaking down material
There is a limited amount of information that a person can absorb at a time. This is especially true when it deals with topics that most employees won’t have much previous knowledge on. In order for the amount of learning material to not overwhelm end users, it has to be appropriately broken down into segments, each with their own clear, simple message that’s presented to users in an easily-digestible fashion.
Running regular training
Another benefit of breaking down learning material is that it allows learning to easily be made continuous, rather than a one-time thing. Breaking down learning into parts allows these sections to be sent out regularly throughout the year, helping keep security awareness consistently on the minds of end users. As repetition is key to learning, this is crucial for ensuring that users actually remember what they’ve been taught.
Ensuring your material is relevant
Ensuring that learning content is relevant to end users is essential for making sure they stay engaged. When an end user is presented with information that they feel is not relevant to them, they will quickly start losing interest and paying less attention. Learning material needs to not only avoid jargon and technical terms, but be made with real-life situations in mind that the average end user would actually encounter in their day-to-day working life. For example, most employees don’t need to know the specifics of regulations or malware attacks, but simply how to conduct themselves in a manner that reduces those risks - and how to appropriately report risks that they may encounter.
Offering practical advice
It’s all good and well teaching employees about the risks out there and how they can be countered - but what’s essential is that employees walk away from training with actual steps in mind that they can put to use right away in their daily work activities. Giving employees the chance to put their training to test right away also helps build memory - and can be achieved using methods such as phishing simulations and phishing awareness training.
Using video & interactive content
Not all content is the same. Text-based content becomes tiresome to users quickly, and should only be used when complemented by visual, more engaging content. Videos are great for keeping users entertained - as long as they are high-quality and enjoyable to watch. Humour can be used to great effect to make security awareness videos more appealing to end users. Interactive content is also great for engaging users. Many people learn by doing - answering questions or otherwise taking part in their learning - and interactive content can also give users a sense of achievement for getting through a course.
Testing your users' progress
It’s essential that after training sessions users are tested on what they’ve learned. This helps you know that users have learned key points and are walking away having learned something - but also helps the learning process of users as they recollect the information they have just learned from their own memory.
Creating a security culture
The most essential part of a security awareness training programme’s effectiveness, however, has as much to do with factors outside the training as the training itself. In order for training to be effective, it has to be a part of a security culture where security is always given the consideration it needs, and users are actively encouraged to bring up concerns and ask questions. A good security awareness programme contributes to this by presenting security as something that is continuous and active, rather than one-time and passive - but it is essential that the organisation supports this effort outside training as well.
How to embed security into
everyday staff culture
Security awareness training will not be effective in improving security outcomes if it is not accompanied by cultural change. Comprehensive training will teach end users how to recognise situations where security is at risk and how to deal with them appropriately - but this knowledge is not going to be put into practice unless the user feels that security is valued in their culture.
Security awareness training will not be effective if it is not accompanied by cultural change.
With the growing number of threats present, as well as the increasing complexity of business services and access to data and systems from mobile devices, it is impossible to know where the next threat or accidental leak to your business might appear. This is why security shouldn’t be about ensuring that your end users choose strong passwords or follow other specific steps - but rather about empowering them to be active guardians of your business, its systems, devices and data.
Don't think of cyber security as an IT problem
Culture is all about values. In order for employees to care about security, it needs to be highlighted as a value throughout the company. This means ensuring that security isn’t seen as the responsibility of the IT or infosec team - but as a responsibility shared by all employees.
Embed security into your company values
Cultural change and the company’s values have to come from the top. Senior management has an important role to play in emphasising the role of security in the business - but it is essential that they grow, rather than dictate, the new culture. This means encouraging employees to take an active role by asking them to bring up concerns relating to their own roles, and prompting them to ask questions and become engaged with security issues.
This way, users feel like they are involved in the security process, and start actively thinking about the security considerations in their own roles. A manager or someone in IT may not be completely familiar with all the processes of an employee’s workflow - which is why it’s essential that users themselves understand that they need to take steps to ensure the security of data and systems.
Get senior management onboard
The senior management also has a role in establishing priorities for the business. Anyone that works for an airline will tell you that safety is always, without any exception, the top priority. Everything else comes second. While in most other businesses security isn’t a life-or-death issue, it’s important to remember just how damaging any breach can be to a business.
If customers no longer feel like they can trust an organisation with their personal information or their business, it could be the end of the company. It should be made clear to all employees that security always comes first - and that it’s always better to ask and make sure than to be sorry afterwards.
Implement least privilege
For a secure business environment, an ingrained principle of least privilege will go a long way toward protecting business assets, data and systems. While the principle of least privilege is often seen as a technical measure - limiting each user to only the privileges that they require for their specific duties - it should also be embedded directly into corporate culture. This means encouraging users to actively report when they have access to more data or systems than they need - helping to limit possibilities of breaches.
Implement soft reminders of best practice
In terms of physical measures, items like posters can be helpful in building a security culture, and also contain helpful reminders on topics such as password strength. It’s important to remember though that just sticking a poster on a wall won’t achieve anything by itself, but they should be used as starters for discussion, or serve in complement to training material that users are already engaged with.
Make sure to reward employees
Finally, it’s important to make sure that employees feel their contributions to security are valued. When employees ask questions, they should always be given time and consideration, and it should be made sure that they completely understand the answer and why it matters to security. When users bring up security concerns, they should always be rewarded for paying attention and working to help keep the business secure.
The essential security awareness
training topics for 2022
It’s not only the format of the security awareness program that matters, but also what you include in the training. Training should exhaust all core topics, without being overwhelming to users. While each organisation and each job role will have different requirements, there are some essential areas that are worth ensuring every single end user is aware of - even just briefly.
usecure's top picks: |
|
Start driving employee
security awareness today
We believe that your end users aren’t your weakest link - but your first line of defence.
usecure offers bite-size security awareness training that is designed to keep your users engaged. Entertaining videos and interactive content ensure that end users are always looking forward to their next training module - while the intelligent automation at the heart of the usecure platform keeps admin time to a minimum.

.png)