What is The Australian Cyber Security Centre's (ACSC) Essential Eight?
What is the Essential Eight?
The Australian Cyber Security Centre’s (ACSC) Essential Eight is a risk management framework that prioritises eight mitigation strategies - taken from the recommended Strategies to Mitigate Cyber Security Incidents for organisations - to help businesses improve their cyber security posture.
Published in February 2017 by the ACSC, in conjunction with the Australian Signals Directorate (ASD), the Essential Eight is considered to be the most effective ‘baseline’ for keeping today’s organisations cyber resilient.
Before 2017, the top four of these mitigation strategies were already mandated for federal government departments by the Australian Federal Government, with the other four strategies mandated by the Attorney-General’s Department’s PSPF (Protective Security Policy Framework).
Why should your business implement these security controls?
These recommended strategies help protect your organisation’s information security system against a range of known cyber threats and keep your customer’s sensitive data secure. Implementing the Essential Eight can also save your business the time, money and effort often needed to respond to a serious cyber security incident.
In addition to keeping your organisation safe, the current NSW Government Cyber Security Policy became effective in February 2019. The policy (section 1.5) requires, by 31 August each year, that each department submits a report detailing a maturity assessment against the ACSC Essential Eight.
What are the Essential Eight security controls?
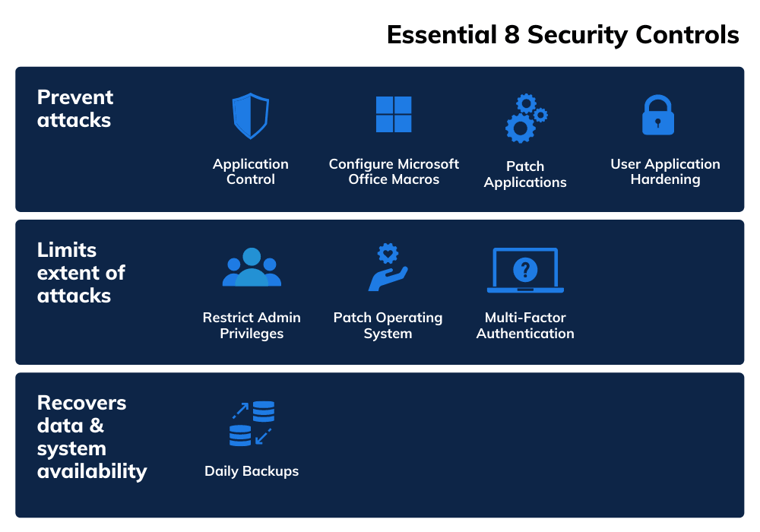
- Application Control/Whitelisting — to control the execution of unauthorised software
- Configure Macros — to block untrusted macros
- Patch Application — to remediate known security vulnerabilities
- Application Hardening — to protect against vulnerable functionality
- Restrict Admin Permissions — to limit powerful access to systems
- Patch Operating Systems — to remediate known security vulnerabilities
- Multi-Factor Authentication — to protect against risk activities
- Daily Backups — to maintain the availability of critical data
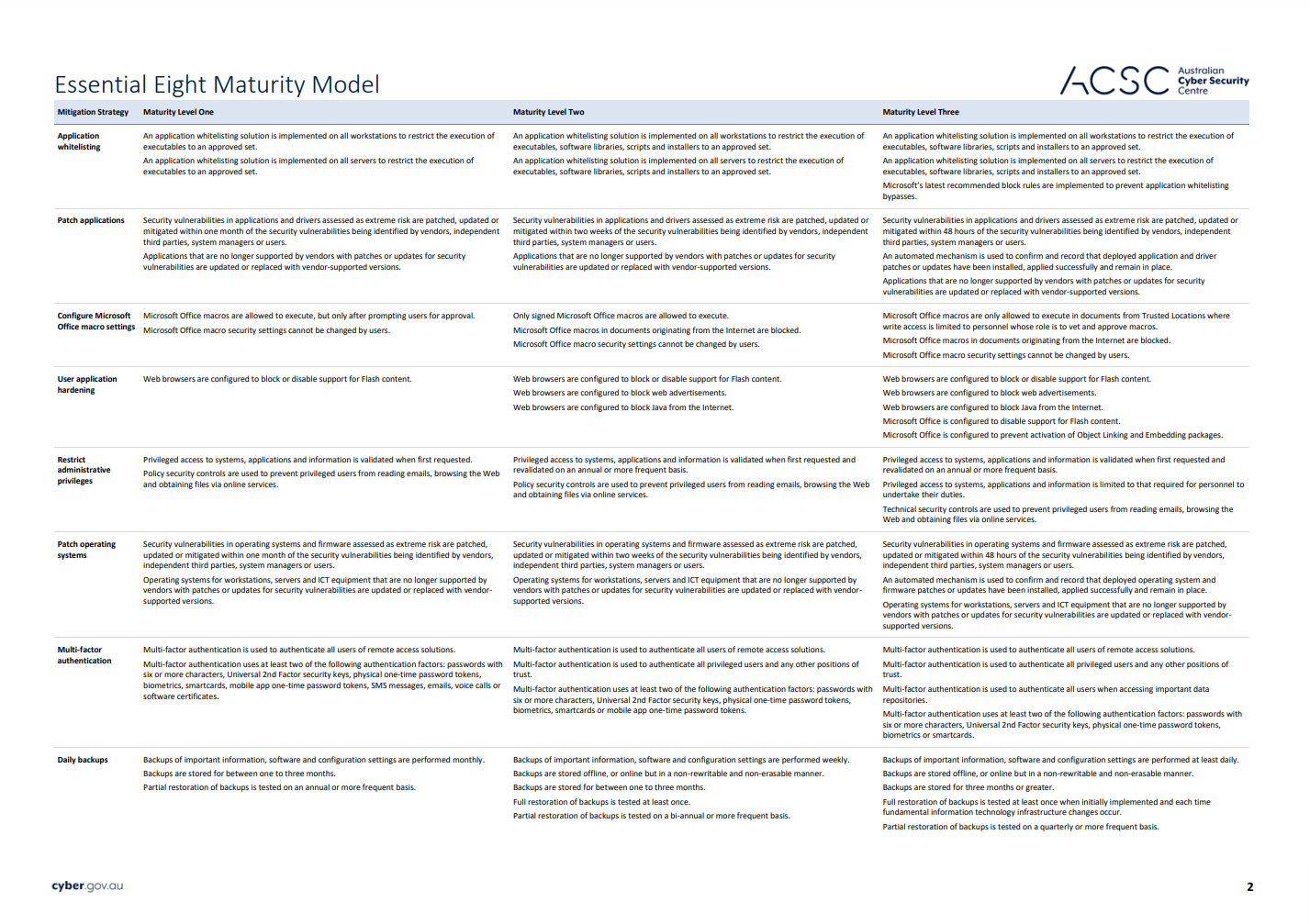
What is the Essential Eight Maturity Model?
The Essential Eight Maturity Model provides advice on how organisations can implement the Essential Eight security controls in a graduated approach.
To assist organisations in determining the maturity of their implementation of the Essential Eight, three maturity levels have been defined for each mitigation strategy. The maturity levels are defined as:
- Maturity Level One — Partly aligned with the intent of the mitigation strategy.
- Maturity Level Two — Mostly aligned with the intent of the mitigation strategy.
- Maturity Level Three — Fully aligned with the intent of the mitigation strategy.
Which maturity level should your organisation aim for?
The ACSC states that, as a baseline, organisations should aim to reach Maturity Level Three for each mitigation strategy. However, some organisations can operate in a higher risk environment where their business is constantly targeted by highly skilled attackers.
Take a look at the Essential Eight Maturity Model in detail using the ACSC's official guide (click to open in a new window):
Is implementing the Essential Eight enough to secure my business?
Whilst implementing the Essential Eight security controls is a great way of keeping your business cyber fit, they don't offer guaranteed protection against all cyber threats and shouldn't be the only protection your business has.
Other security measures, like effective policy processes and ongoing human risk management, are essential layers of protection that any modern business needs to deliver adequate cyber security.
Getting started
Learn more about the Essential Eight's security controls, maturity model and implementation via the Australian Government's website.
About usecure
usecure is the Human Risk Management (HRM) solution that empowers businesses to reduce user-related security incidents, build a cyber-resilient workforce and achieve compliance standards through automated user training programs.
Trusted by leading IT pros and managed service providers (MSPs), usecure analyses, reduces and monitors human cyber risk through risk-driven security awareness training programs, simulated phishing campaigns, simplified policy management and continuous dark web breach monitoring - all from one platform.