Why Social Engineering Isn't Just a Headache for Big Tech Firms
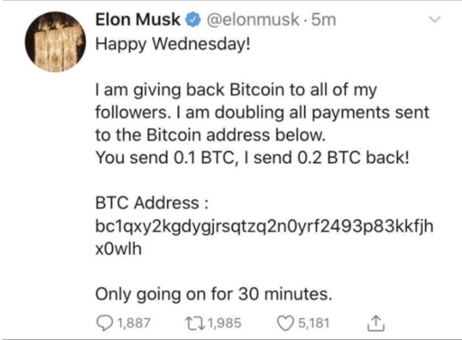
On Wednesday 15th July, a number of high profile Twitter accounts, including Elon Musk, Barack Obama, Kanye West, Joe Biden and Bill Gates were hacked.
The aim of the attack was simple, a bitcoin scam we've seen numerous times "Send bitcoin to our account and we'll double your money!".
However, the implications of this attack are very different. They point to vulnerabilities of impersonation, deception and scams on one of the most widely used, politically influential platforms on the planet.
How Did The Hack Happen And What Type Of Attack Was It?
It seems as though targeting such high-profile political and industry leaders is a brazen display of the weaknesses in Twitter's cyber-security defences.
For the moment, the details of the attack remain speculation. However, many are suggesting the attacker has used high-level employee privileges to gain access to these accounts. The New York Times has claimed, via a twitter spokesperson, this was a co-ordinated social engineering attack.
Twitter seemed unable to stop the attack, with repeated messages posted from the same accounts when removed.
The result has been the disabling of all verified accounts on Twitter from posting, a 3% drop in share price (which has since rebounded at time of publication), and a loss of trust in the platform.
Twitter's History of Large Scale Data Breaches
Less than a month ago, Twitter was apologising for a breach to the businesses who use their advertising platform, where personal data such as email addresses and phone numbers were accessed.
This social engineering scam isn't particularly new, with fake accounts of notable figures such as Elon Musk, using similar usernames to pose as the real account. However, this differed from the imitator approach, by using the real accounts, which is an unprecedented move by these scammers.
The high-profile nature of the users who have been targeted in the most recent attack, and the implications of a breach spreading disinformation from a Presidential candidate, highlights the dangers of online impersonation.
Trust in the Twitter platform and its overall reputation will no doubt be diminished, especially as these high profile attacks continue to happen repeatedly.
It seems from the initial reports as though this was from a high-level employee account. Having an employee with these types of privileges leaves a distinct vulnerability for hackers to exploit.
But how does the hacker gain access to this high-level account?
Social Engineering: What is it and why is it such an issue?
"We detected what we believe to be a coordinated social engineering attack by people who successfully targeted some of our employees with access to internal systems and tools."
— Twitter Support (@TwitterSupport) July 16, 2020
This accentuates the vulnerabilities that all major social media platforms have (Facebook, Twitter, Snapchat) have all been the victims of data breaches in the past.
Most often due to the weakness of what we call the 'Human Firewall'. Whilst they may have complicated cyber security for malware, employee's remain a weakness that hackers can exploit.
This is how it is believed the hackers got access to the entire back end platform of Twitter.
Often this is through phishing attacks, simple emails trying to recover information from employee's. Social Engineering relies on the basic tactics of trust, manipulation and deception.
However, the increasingly sophisticated digital criminal has an arsenal of different tactics used in social engineering attacks such as: baiting, phishing, whaling and more. Most of these scams fall under the same theme:the pretence of being a legitimate person or resource.
Common Types of Social Engineering Attack to Look out For:
- Baiting
- Quid Pro Quo
- Phishing
- Spear-phishing
- Whaling
- Voicemail phishing and SMS phishing
- Watering hole
- Pretexting
- Requesting a Password Change
- Fake IT Support
- Fake LinkedIn Profiles
- Name-Drop
- Insider threat
More detailed information can be found in our earlier blog on Social Engineering.
Social Engineering Can Affect Any Business
Twitter has suffered public humiliation, however, for most businesses that are internally breached, this should be considered getting off lightly.
"All tech companies face the issue of malicious insiders."- Vice
Whilst Twitter and Facebook make the headlines, and in this case, international news, over these forms of hacks, it does not mean they are more vulnerable than smaller organisations. In fact, whilst the above quote from Vice is true, it should go further to say 'All companies.' not just limited to tech.
Most companies use some kind of digitisation, whether it be for payroll, communications, accountancy or any number of things. That leaves them all vulnerable to a social engineering attack.
In fact, SMB's are the most highly targeted by social engineering attacks."43 percent of UK SMBs have suffered phishing attacks involving attempts to impersonate staff in the last year."
Whilst Twitter faces public backlash, they may consider themselves lucky compared with the typical SMB, A report by VIPRE found that "66% of SMBs would close their doors if hit by a data breach".
In this sense, the damage to SMB's is much more serious than it would be for a company like Twitter, which can weather the storm time and time again.
How can businesses combat social engineering?
It's important to regularly assess your companies vulnerabilities to a social engineering attack, such as a phishing attack. As this Twitter saga has proven, it takes one errant employee to lead to an embarrassing data breach.
There are a few basic things every company should have their employee's do:
Regular Cyber-Security Training:
The most simple and most effective way to combat the threat of social engineering in your business is employee awareness. If employees are trained and aware of the types of social engineering scams discussed above, they are far less susceptible to falling for them.
Cyber-security awareness training for your team will dramatically reduce your company's susceptibility to Social Engineering. By promoting a culture of awareness and training, your risk of manipulation and the consequences are dramatically reduced.
Practice good password hygiene:
Regularly changing passwords, and avoiding using simple passwords is one of the most simple ways of preventing this form of attack. Always use a new password for a different account, worryingly 65 percent of people use the same password for all their accounts. This means if one is breached, all accounts can be compromised. You can check if your password for an account may have been already leaked using our tool: uBreach.
Conduct simulated phishing attacks to assess your risk:
To assess whether your user's would be vulnerable to a similar attack, conducting a simulated phishing attack of your own can make you aware of the risk to your business, and help highlight the issue to employee's.
This will keep security top of mind when using email, and make employee's aware of practising safe email habits, e.g. not opening unsolicited emails, attachments that seem suspicious or answering unrequested emails for personal information.
usecure offers intelligently-automated security awareness training, simulated phishing and policy management to help you build a comprehensive strategy to mitigate social engineering in your business.