Top 10 cybersecurity threats in 2024
This blog will delve into the top ten cybersecurity threats in 2024, offer insights and recommend mitigation strategies to help you safeguard your organisation's security.
In this blog, we’ll cover:
- Human risks
- Phishing
- Ransomware
- AI-powered threats
- The dark web
- Business Email Compromise (BEC)
- Remote work
- Supply chain vulnerabilities
- Cloud Security
- Quantum computing
1. Human risks
The weakest link in cybersecurity is often not the technology but the people who use it. Human risk is considered a top cybersecurity threat because of the central role humans play in the operational and security processes of organisations.
The most common human risks involve careless behaviours at the workplace, such as using weak or reused passwords, failing to secure physical devices, mishandling sensitive information or downloading malicious software by mistake. Poor security hygiene and insider credential theft can also leave organisations vulnerable to exploits and attacks.
The recent trend of human risk
The 2023 Cost of Insider Risk Global Report by Ponemon Institute outlines employee or contractor negligence, malicious intent and insider credential theft as the three main reasons for insider threat incidents.
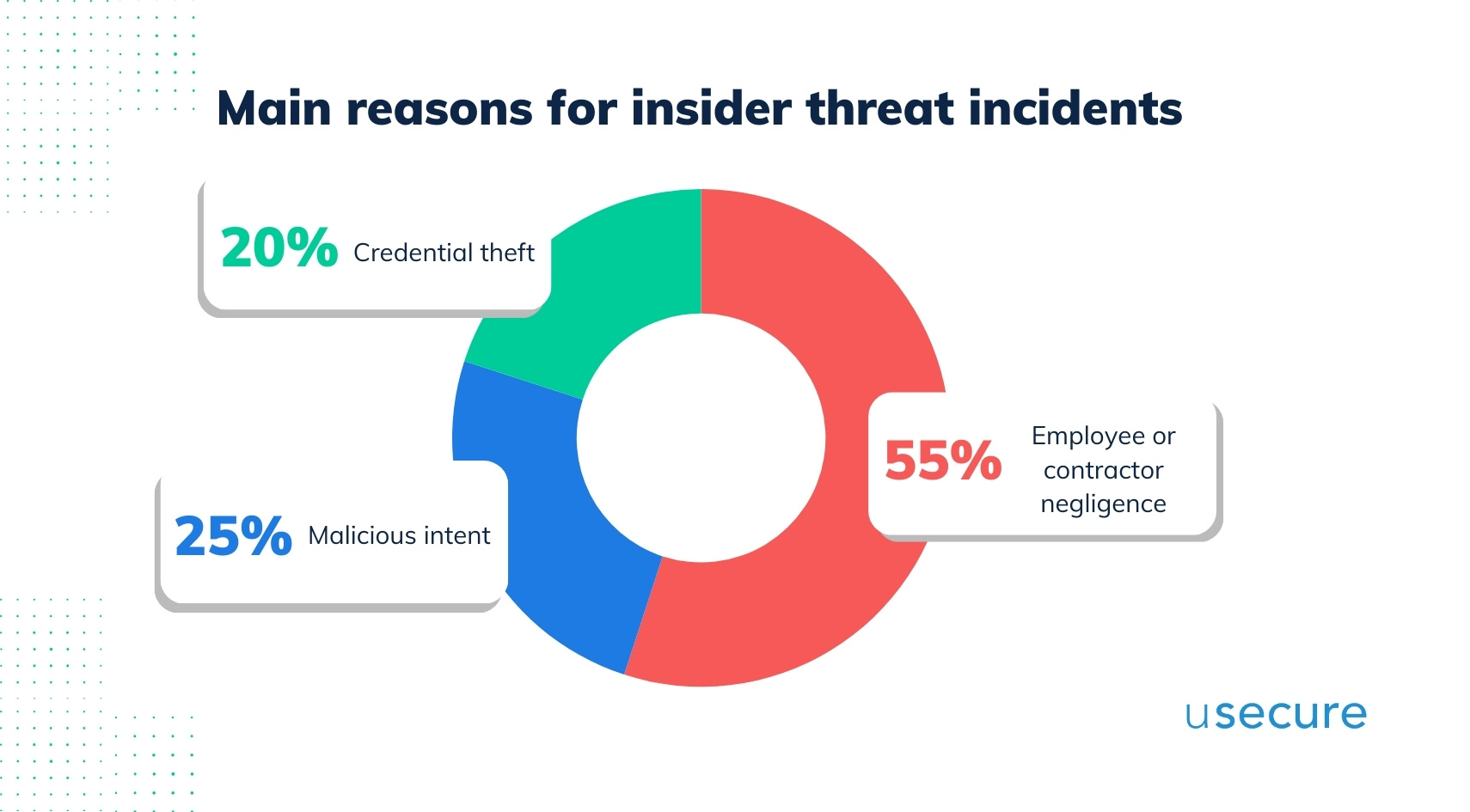
According to a recent study by the security firm Mimecast, human error remains the primary cybersecurity risk for businesses. The report highlights that in 2023, more than 70% of cyber breaches were attributable to human errors, including incidents where credentials were stolen, identities were compromised, social engineering tactics were employed, and access privileges were misused.
Mitigation strategies
- Work with a cybersecurity vendor:
Cybersecurity vendors can provide tailored training programmes that raise awareness among your employees regarding different types of cyber threats they might face. These programmes are often more sophisticated and up-to-date compared to in-house training, as vendors specialise in the field and keep abreast of the latest tactics used by cybercriminals.
- Human Risk Management (HRM):
HRM is extremely useful for preventing human risks. HRM assesses which roles in the organisation are most at risk of being targeted attackers. It can also tailor cybersecurity training and protocols to these roles. For example, finance department employees would require in-depth training on the verification processes for payment changes and requests.
2. Phishing
Phishing remains one of the most common attack vectors. Phishing attacks continue to be effective because they are good at exploiting human psychology rather than technological vulnerabilities.
Attackers craft emails or messages that mimic legitimate sources, such as reputable companies or known contacts. The goal is to trick the recipient into revealing sensitive personal or financial information or downloading malware onto their device.
The recent trend of phishing
Recent trends in phishing attacks have shown a significant increase in both frequency and sophistication, highlighting the evolving challenge these threats pose. According to the ThreatLabz Report, in 2022, there was a 47.2% increase in phishing incidents compared to the previous year thanks to the growing sophistication of phishing techniques, which now often include the use of phishing kits and AI tools. According to the report, Education was the most targeted industry in 2022, with attacks increasing by 576%.
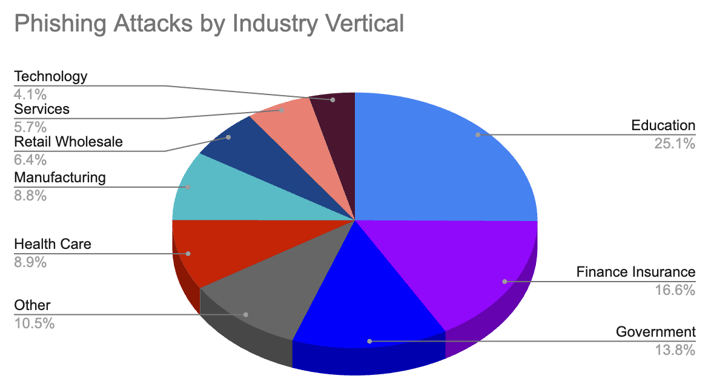
Source of image: ThreatLabz Report
Mitigation strategies
- Deploy phishing simulations:
Phishing simulation is a proactive and educational tool. Simulated phishing aims to train employees to recognise and report phishing attempts. Phishing simulation is a proven and widely adopted method to strengthen employee's ability to fight against phishing attacks.
- Use multi-factor authentication (MFA):
Enforcing MFA where possible to add a layer of security. Even if credentials are compromised via a phishing attack, MFA can prevent unauthorised access. This extra security step requires users to verify their identity using two or more validation methods, effectively blocking intruders who might have stolen a password.
3. Ransomware
Ransomware attacks involve malicious software that encrypts the victim’s data, making it inaccessible until a ransom is paid. These attacks typically start with phishing emails or exploiting network vulnerabilities. Once the ransomware is installed, it locks all accessible data, and the attackers demand payment for the decryption key.
The recent trend of ransomware
Recent findings about ransomware by Corvus reveal alarming statistics that highlight the concerning situation. From August 2022 to May 2023, the number of ransomware incidents has soared by a staggering 101.84%. The increase became particularly notable in late 2022, peaking with a growth of 36% in the first quarter of 2023, which also marked a 65% rise compared to the same period in 2021. This trend shows no indications of diminishing.
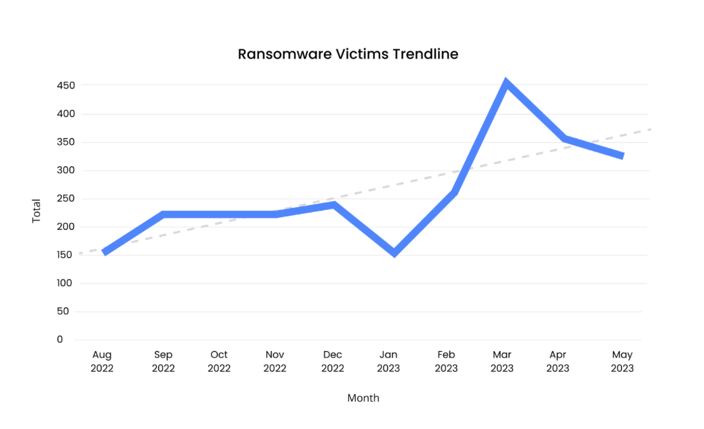
Source of image: Corvus
This trend is expected to escalate, with predictions suggesting that ransomware attacks will occur every 2 seconds by 2031.
Mitigation strategies
- Take advantage of security awareness training:
Provide employees with security awareness training programmes to educate them on how to recognise and avoid potential ransomware threats, such as malicious links or attachments in emails. Regular training and phishing simulations can significantly reduce the likelihood of an employee inadvertently triggering a ransomware attack.
- Use advanced email filtering tools:
Implementing sophisticated email filtering solutions can be useful for detecting ransomware attempts. These filtering tools analyse the authenticity of the sender, scan email content for malicious links, and identify suspicious attachments.
4. AI-powered threats
Artificial intelligence (AI) enhances offensive capabilities in cybersecurity. AI can be used by attackers to automate tasks that were previously time-consuming for humans, such as identifying system vulnerabilities, crafting phishing emails, or even hacking into systems.
Deepfake-powered attacks have also become a sinister threat. The attacks refer to the use of artificial intelligence (AI) and machine learning techniques to create highly realistic but false audio, video, or image content. Here is an example of the most eerily deepfake video on the internet.
The dynamic nature of AI-driven threats means that they can evolve in response to changes in cybersecurity measures, continuously finding new vulnerabilities to exploit. This allows cybercriminals to launch large-scale attacks with higher efficiency.
The recent trend of AI-powered threats
AI technologies evolve at a rapid pace, enabling new forms of cyber attacks that can quickly outpace traditional security defences. According to the Canadian Cyber Threat Intelligence Annual Report, PwC highlights the radical shifts in the cyber threat landscape over the past year, exacerbated by new technologies. They point out the evolving nature of cyber threats as AI technologies become more integrated into attack vectors.
Mitigation strategies
- Provide AI Security Training to employees:
Educate employees about the specific challenges posed by AI-driven threats. Training should include scenarios involving AI tactics, teaching employees how to recognise and respond to AI-powered threats effectively.
- Open Source Intelligence (OSINT):
OSINT can be highly useful in combating AI-driven threats. OSINT involves collecting and analysing information from publicly available sources to support intelligence efforts. OSINT is a valuable and cost-effective component that should appear in the organisation's cybersecurity strategy.
5. The Dark Web
The dark web's role in accelerating cybercriminal activities makes it a significant threat to global cybersecurity. The dark web hosts numerous marketplaces that sell hacking tools, malware, ransomware kits, and services such as DDoS attacks, data breaches, and other cybercriminal activities.
The dark web also provides a high level of anonymity which is facilitated by the use of encryption technologies and specialised browsers. This anonymity makes it challenging for law enforcement and security agencies to track and prosecute perpetrators of cybercrime.
The recent trend of the dark web
The recent trend in dark web threats shows a notable increase in data theft and leaks. These leaked data would almost always end up being on the dark web. IBM’s X-Force Report revealed that Data Theft and Leak were the top impact to organisations, making up 32% of cybersecurity incidents in 2022.
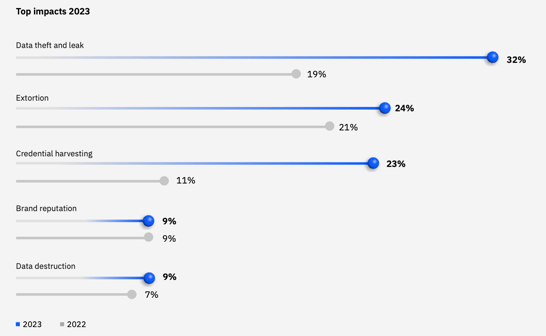
Top impacts X-Force observed in incident response engagements in 2023
Source of image: IBM’s X-Force Report
The report also observed that attackers were increasingly investing in measures to obtain user identities – with a 266% increase in infostealing malware designed to steal personal information such as emails, social media and messaging app credentials, banking details, crypto wallet data and more.
Mitigation Strategies
- Use a Dark Web Monitoring (DWM) tool:
A DWM tool can assist you in continuously scanning the dark web, including forums and marketplaces known for illicit activities, to detect if sensitive corporate data or personal information has been exposed. This includes leaked credentials, confidential documents and financial information. If the monitoring tool finds any data related to the client on the dark web, it immediately alerts them. Real-time alerts allow organisations to act swiftly to mitigate the risk, such as changing passwords or securing breached accounts before the information can be exploited.
- Incident Response Planning:
Having a well-defined incident response plan enables organisations to react quickly to a security breach. This should include procedures for containing the breach, eradicating the threat, recovering data, and communicating with stakeholders.
6. Business Email Compromise (BEC)
BEC is considered a top cybersecurity threat due to its significant impact. BEC is a sophisticated scam targeting companies with international suppliers or businesses that regularly perform wire transfer payments. Successful BEC can lead to significant financial losses including stolen funds, disrupted operations, and a negative impact on the organisation’s image.
In BEC attacks, scammers pretend to be a trusted figure such as a senior executive or a partner company aiming to gain access to or impersonate corporate email accounts to deceive the company’s employees, customers, or partners into transferring sensitive information or funds to fraudulent accounts.
The recent trend of BEC
BEC attacks are becoming more and more financially damaging. The FBI, in their 2023 IC3 Report, highlighted that BEC remains a significant threat to modern enterprises, with reported losses nearing $3 billion in 2023. This marks a 7% increase over the previous year's total of $2.7 billion, summing up to a total of $14.3 billion in losses since BEC was included in the FBI's reports in 2015.
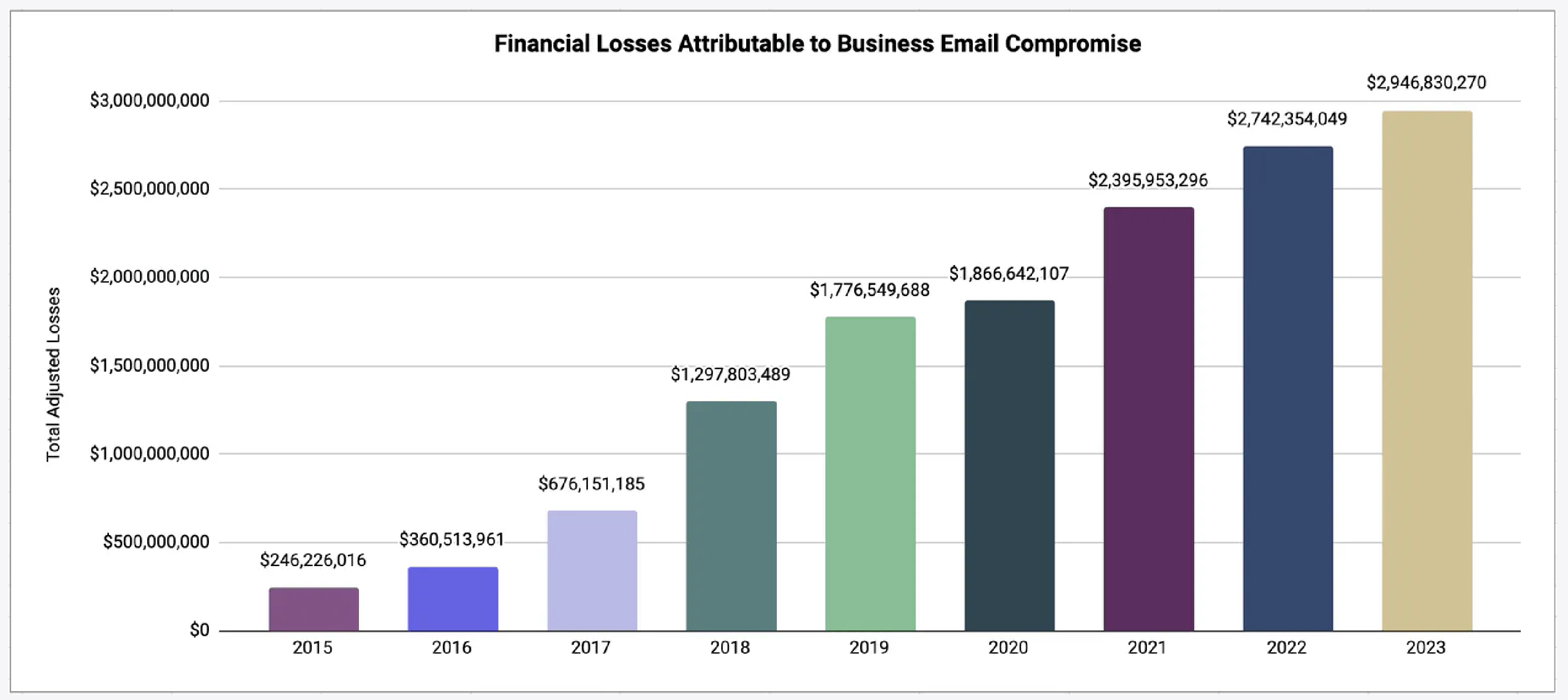
Source of image: The FBI 2023 IC3 Report
Mitigation strategies
- Develop secure email practices:
Encourage secure email practices, such as avoiding the sharing of sensitive data, especially financial information over email. Deploy secure file transfers instead of email attachments when possible.
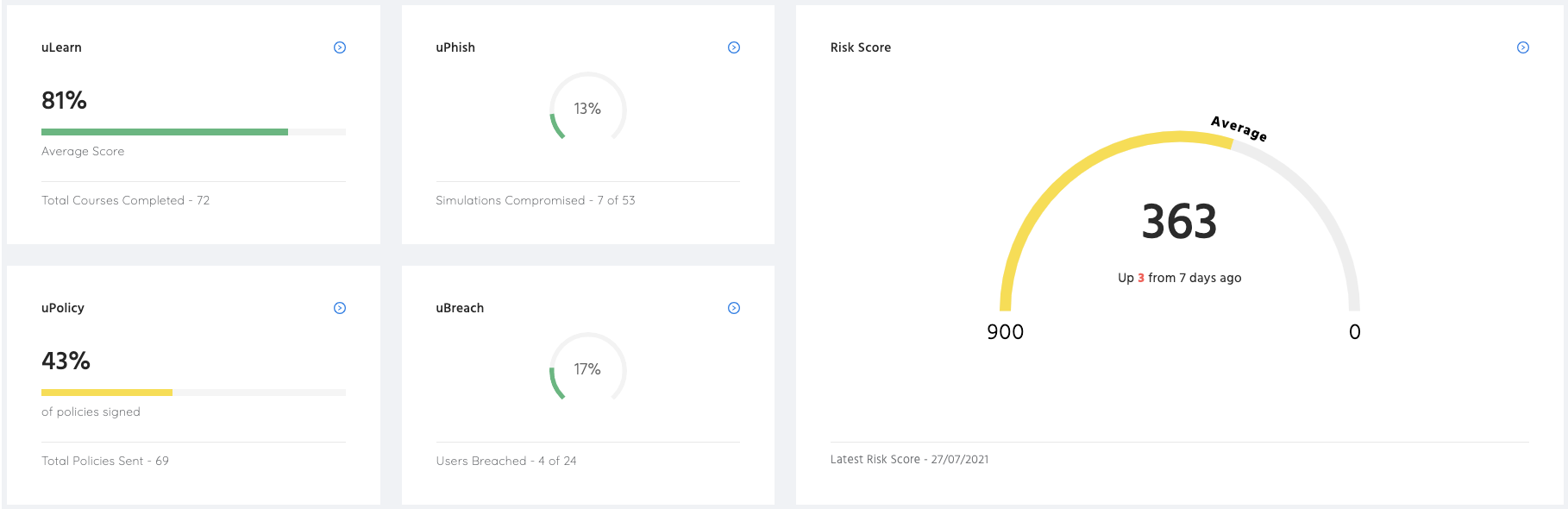
- Use an assessment tool with a risk-scoring function:
Some sophisticated cybersecurity vendors would provide a risk-scoring tool for you to visualise the human threat within your organisation.
A risk score allows you to assess the level of security performance of your employees, especially those involved in financial transaction tasks. The scoring tool could also provide you with a breakdown by group or department.
7. Remote work
The shift to remote work has expanded the attack surface in many organisations. Remote systems often lack the same level of security as in-office networks, making them prime targets for cyberattacks.
With remote work, employees access corporate networks from different locations and often through personal or less secure devices. This can lead to increased risks of unauthorised access. Attackers can exploit weak home Wi-Fi security, use malware-infected personal devices as a gateway, or intercept unencrypted communications across less protected networks.
The recent trend of remote work
The World Economic Forum in its 2023 Global Cybersecurity Outlook, has emphasised that the trend of remote work has intensified the challenge of maintaining cybersecurity in many organisations.
They note that as businesses adapt to a more dispersed workforce, the traditional perimeter-based security models are becoming less effective. They also highlight that securing a remote workforce is necessary for developing better resilience.
Mitigation strategies
- Consider services provided by MSPs:
Small businesses or those lacking in-house expertise may benefit from working with managed services providers (MSPs). MSPs could offer tailored and a variety of security solutions to protect your business from remote work-related threats.
- Deploy endpoint security solutions:
Equip all endpoints with robust antivirus and anti-malware solutions, along with firewalls, to detect and mitigate threats before they can cause harm.
8. Supply chain vulnerabilities
A single vulnerability in the supply chain can compromise all connected entities.
Supply chain attacks occur when a hacker infiltrates your system through an outside partner or provider with access to your systems and data. This could include software providers, hardware manufacturers, or service providers.
Supply chain attacks can be particularly dangerous because they exploit trusted relationships and are often difficult to detect. As businesses increasingly rely on third-party services and software, the potential for a breach through a supplier grows.
The recent trend of supply chain vulnerabilities
Organisations are recommended to pay due diligence to downloading software onto their IT estates. A significant piece of statistics shared by Sonatype, a software supply chain management platform, indicated that there has been a rapid increase in supply chain attacks over the last three years. The report showed researchers had uncovered 88,000 malicious open-source packages in 2022 and this equated to a staggering 742% increase over the number recorded for 2019.
Mitigation strategies
- Use third-party audits:
Regularly audit third-party vendors for compliance with security standards and policies. Require vendors to adhere to specific cybersecurity practices and standards, such as ISO/IEC 27001 or NIST frameworks. Implementing contractual agreements that enforce these security measures is also crucial.
- Use a policy management tool:
A policy management tool can help organisations develop, manage, and enforce security policies that govern their interactions with suppliers.
Sophisticated policy management tools include a variety of features that automate the process. This helps organisations to continuously monitor the compliance status of suppliers and take timely action if discrepancies are found.
9. Cloud Security
As more companies migrate to the cloud, the potential for data breaches, insecure interfaces, and hijacking of accounts increases. Cloud threats can involve data breaches, misconfigured cloud storage, insecure APIs, and account hijacking. Attackers may even exploit weak authentication processes to gain access to cloud-based applications and data. Once inside, they can steal data, plant malware, or use your cloud services to launch further attacks.
The recent trend of cloud security
The growing adoption of cloud computing has brought forth a lot of security concerns for IT professionals. According to websitepulse.com, 91% of organisations said that they were concerned about cloud security and 90% of organisations said at least half of their data on the cloud was sensitive. 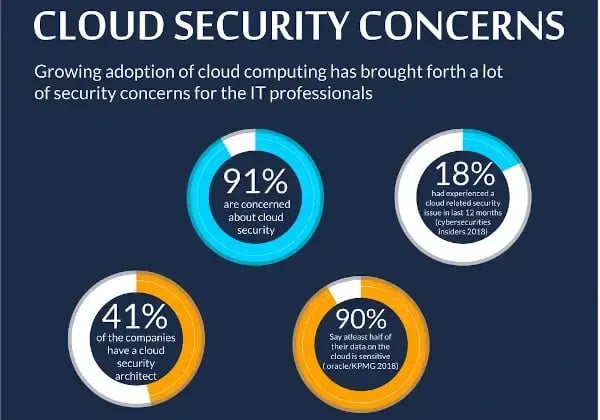
Source of image: websitepulse.com
Attackers are constantly searching to exploit hybrid cloud weaknesses to target sensitive data stored in previously unreachable destinations. As Google predicts in its new Cybersecurity Forecast 2024 Report, attackers would target misconfigurations and weak identity protection in cloud infrastructure and applications to cross boundaries between public and hybrid cloud environments.
Mitigation strategies
- Choose a vendor who complies with GDPR and ISO 27001:
Choosing a cloud-service vendor that complies with GDPR and ISO 27001 can provide you with enhanced data security.
-
- GDPR: Compliance with GDPR ensures the vendor handles data with the highest regard for privacy and security, adhering to stringent European Union regulations on data protection.
- ISO 27001: Compliance with ISO 27001 means that the vendor has a comprehensive information security management system (ISMS) in place, which is systematically examined.
- Choose a vendor with security certifications:
Choosing a vendor with Cyber Essentials/Cyber Essentials Plus certificates is beneficial for your organisation. These certifications are government-backed, industry-supported schemes to ensure the vendors protect themselves against common online threats.
-
- Cyber Essentials: Cyber Essentials covers essential precautions related to securing Internet connections, devices, and services.
- Cyber Essentials Plus: Cyber Essentials Plus provides further assurance that the company not only has good security practices on paper but also that these measures have been effectively implemented. This certification involves rigorous testing of an organisation’s cybersecurity measures, including a technical audit of systems in scope.
10. Quantum computing
The rise of quantum computing poses a significant future threat to current encryption methodologies.
Current cryptographic systems rely on complex mathematical problems that classical computers take too long to solve. Quantum computing could solve these problems much more quickly and automatically.
Quantum computing could potentially break many of the cryptographic protocols that currently secure our data. Preparing for this future involves investing in quantum-resistant cryptography and staying abreast of advancements in quantum technology.
The recent trend of quantum computing
According to netmeister.org, the latest accomplishments are the IBM Condor (1,121 qubits) and the Atom Computing atomic array (1,180 qubits), both towards the end of 2023, showing an increasing acceleration in the number of qubits.
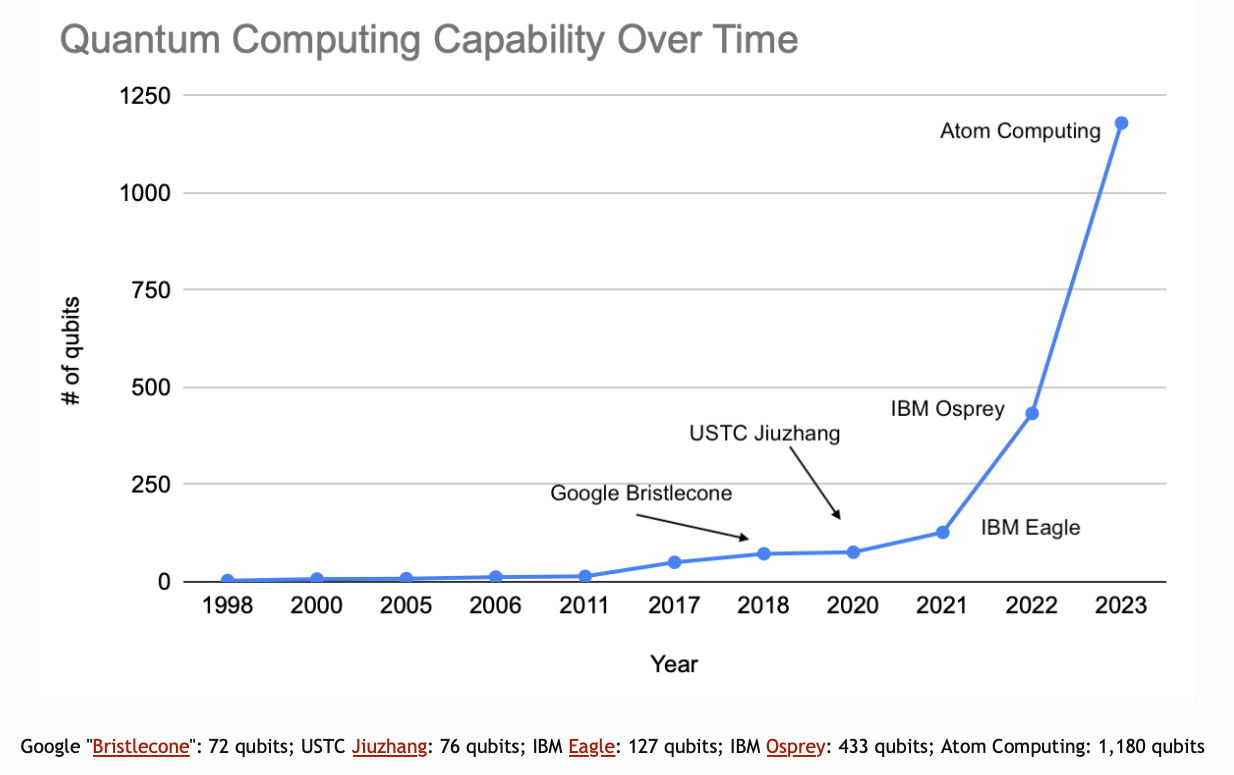
Source of image: netmeister.org
Such powerful systems can potentially decrypt current public key infrastructures (PKIs) that secure digital communications, leading to cryptopocalypse -- the point at which quantum computing becomes powerful enough to break any type of cryptography.
Mitigation strategies
- Keep an eye on new technology advancements:
Working with a cybersecurity vendor is the best way to keep an eye on the new technology advancements. Vendors could provide information on cybersecurity hot talks and give you regular updates. This is advantageous for your organisation because it could broaden your horizons and provide useful intelligence for you to build your organisation's security defences.
- Continue training your employees:
Implement a regular and continuous security training programme that goes beyond annual training sessions. Repetition is key to memory retention. Regularly distributed new short courses, quizzes, security alerts, notes or posters to cement important security practices in employees' long-term memory.
Stay informed and vigilant in the digital age!
Understanding these ten evolving threats is just the first step in defending against them. Navigating the complex web of cybersecurity is crucial for any organisation aiming to protect its business in the digital age. Watch a short demo to see how we can help you enhance your security posture. Or get in touch with us to unlock the 14-day free trial to experience our renowned security awareness training programme.



.png)