How to Reduce The Risk Of Human Error Cyber Attacks Remotely
As we move towards an era of an increasingly remote workforce, we need to ensure that users human error risk is reduced as much as possible. Cybercrime has increased since the pandemic, in part, it's suspected due to the remote workforce being a target due to their isolation from typical security defences. This blog discusses how to reduce the risk of human error with a remote workforce.
When thinking about the threats facing a remote workforce, many will think of the lack of IT infrastructure, use of own devices and other IT infrastructure issues that may occur. However, there is also a much larger risk of human error leading to an organisational threat such as malware or cybercrime.
When employee's are working remotely, they will be more easily targeted for phishing campaigns (due to lack of interaction/online interaction with colleagues). They will be more susceptible to social engineering attacks, or even simply physical risks such as leaving important documents in unsafe locations.
As many businesses have found, there are plenty of advantages that can come from remote working. However, managing this human error remotely can seem like an impossible task, however there are tools and tricks that can help you monitor and empower your workforce, to reduce the risk of human error to your business.
- A 64 percent increase in phishing and ransomware attempts
- Critical vulnerability patch time has increased by 40 days
- Unsecured Wi-Fi usage is up by over 240 percent
Email Vulnerabilities and Phishing Attacks
When working remotely, potentially the biggest threat to your workforce is through phishing attacks. At the time fo writing, in 2020 we have seen an increase in phishing attacks (SOURCE), perhaps in part due to remote working.
As employee's are isolated, and working on personal devices, hackers have assumed they are more susceptible to phishing attacks. This is perhaps true, as they may be swapping from personal and private accounts on devices, be communicating more through channels such as text and email, and therefore more likely to fall for a phishing attempt.
Increase in spear-phishing. Some have even reported up to a 30,000% increase in phishing attacks during the Covid-19 Pandemic.
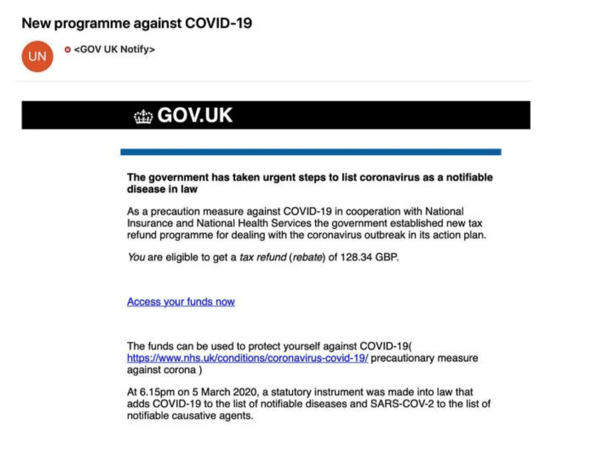
Always ensure end users are aware of the potential risks of clicking links on emails, even if they seem legitimate as the one above. There are a few recommended steps to take to be able to spot a phishing emails
- Look at the email address, often they will be dissimilar or a faked version of the real company's email
- Look for spelling errors, spelling errors are common in phishing emails. It's even been suggestions this is done intentionally, to weed out the more discerning users.
- Think if you've requested this information. If you haven't actively asked for a link, get in contact with the company to see if it is legitimate.
- Stop if the email has a sense of urgency, often phrases such as 'CLICK NOW' try and encourage an immediate response, suggestive of a phishing email.
Secure your home network
Secure Your Router's Password
Securing your home network is key to working safely when working remotely. The first piece of advice is to change your factory default settings on your home WiFi router - the name and password that come automatically with the router, it is much easier for hacker's to gain access to this. Make sure to change your password to something secure, the current recommendation is 3 random unconnected words.
Encrypt Your Home Router
Next you should take steps to encrypt your network, WPA- 2 is seen as the industry standard and should be seen as a minimum requirement for your home router. Other settings may easily be exploited by attackers, who would then be more easily able to access the files in your network.
Change Your Default IP Address
Changing your default IP address can be another way to ensure that your home network is secured. Your IP address is your unique identifier on the web, if hacker's are able to gain access to your IP, they can do a range of things; including duplicating your IP for illegal content, up to launching DDoS attacks with fake web traffic. By changing your IP it will make it more difficult for hackers to find.
Ensure Your Router Stays up-to-date
If your router does become compromised by hackers, it's likely that the provider will install a patch - a way to fix the problem the hackers are exploiting. Most routers do not provide the option to automatically update, so you will have to do this manually. This will prevent hackers from exploiting any previous vulnerabilities that have been fixed.
Risks of Bring Your Own Device (BYOD)
Using personal devices is becoming increasingly common in the workplace, as people gain access to much more integrated, internet-connected devices. This can include anything from smartphones, tablets, laptops and more. In a more flexible and remote working environment, BYOD policies will become increasingly common. Therefore, it's important to make sure that these devices have been properly secured.
Risks of using personal devices:
- Devices being lost or stolen. This can cause an issue because of the sensitive information that might be lost or leaked from these devices.
- Man-in-the-Middle Attacks. If BYOD policies are poorly managed, attackers may exploit them in order to intercept sensitive information. This could be done by eavesdropping at public Wi-Fi networks used by remote workers, or by attackers placing themselves within range of the company Wi-Fi network.
- Insider attacks. These could be either deliberate attempts to access data (sabotage), or accidental (negligent data-handling) incidents, such as employees printing off sensitive company information at home or accessing confidential data via an unsecured network.
- Shoulder surfing. Unauthorised users may also attempt to view sensitive company information shown on the screen of your personal devices.
- Malware infection. This could come about through employees opening malicious emails on BYOD devices, using these devices on unsecured public networks or by visiting bogus/harmful websites in their own time.
How to Protect against them:
- Patching and malware protection. These become the responsibility of the user, as the company does not manage the device.
- Avoid storing data on your personal devices. Try to avoid storing data on your personal devices when possible, even if you need to access it sometimes. This protects confidentiality if a device is lost, stolen or accessed by a cyber criminal. Instead, try accessing data from the cloud instead.
- Protecting all devices with strong passcodes or biometric data such as fingerprints. This includes using a different password for each device and account. You should also make sure your passwords are complex and known only to yourself!
- Enable multi-factor authentication. This includes a combination of something you know (eg. your password), you have (eg. a finger-print scan) and/or a security code/token. These additional layers make it more difficult for unauthorised users to access sensitive information. If one factor is overcome, attackers still have to bypass at least one more barrier to obtain anything valuable.
- Software to remotely erase your device if lost or stolen. If the worst case scenario were to happen and you lost your device, you should have already installed software that means you can remotely erase your data. This can be a last resort if you feel your device is now in unsafe hands.
Social Engineering
Employees are working different hours, which may choosing to work later, or outside the standard 9-5 operating hours. This puts them outside the help of the security team. It is also especially easy to launch a social engineering attack when employees are working remotely due to the different nature of communication, imitating and manipulation can be much easier online.
Hacker's may try to imitate:
- Your CEO or another member of management. The social engineer could send you an email or text message that claims to be from someone with authority, and ask you to hand over information or make a payment.
- A member of IT support staff. An attacker could call into your office and claim to be from your IT support team. They could then ask you for your passwords or for other confidential information.
- Any colleague. A classic social engineering tactic involves simply hanging out in communal areas and getting involved in confidential conversations or following staff members through locked doors into secure areas.
What To Do To Prevent A Social Engineering Attack
-
Whenever a new person from your clients' or partners' organisations contact you for the first time, always verify their identity first or check with someone who has worked with them before.
-
If a plumber, repairman, IT support team member or anyone else requests to be let inside the company's premises, always ask to see their ID first. If they are who they say they are, they will always be carrying ID on them.
-
Never share or give your passwords to anyone. A legitimate member of IT staff would never ask for your password.
-
Never plug in devices to your computer unless you are completely certain of their owner and their contents.
-
Contest people attempting to tailgate, or people walking in the premises without an ID.
-
If you're not certain of who you are speaking to over the phone or over email, call back the person or organisation who you believe you should be speaking to directly.