Mastering CIS Control 14 -- Security Awareness and Skills Training
In this blog, we’ll delve into the details of CIS Control 14 and its Safeguards. We'll provide you with best practices for CIS suggested implementations, hoping to help you build an effective security awareness program in your organization.
In this blog, we’ll cover:
- Why is CIS Control 14 important?
- What are the Control 14 Safeguards and how to implement them?
- CIS Safeguard 14.1 – Establish and Maintain a Security Awareness Program
- CIS Safeguard 14.2 – Train Workforce Members to Recognize Social Engineering Attacks
- CIS Safeguard 14.3 – Train Workforce Members on Authentication Best Practices
- CIS Safeguard 14.4 – Train Workforce on Data Handling Best Practices
- CIS Safeguard 14.5 – Train Workforce Members on Causes of Unintentional Exposure
- CIS Safeguard 14.6 – Train Workforce Members on Recognizing and Reporting Security Incidents
- CIS Safeguard 14.7 – Train Workforce on Identifying and Reporting if their Enterprise Assets are Missing Security Updates
- CIS Safeguard 14.8 – Train Workforce on the Dangers of Connecting to and Transmitting Enterprise Data Over Insecure Networks
- CIS Safeguard 14.9 – Conduct Role-Specific Security Awareness and Skills Training
Why is Control 14 important?
CIS Control 14 highlights the human element of cybersecurity, which is often the weakest link in an organization’s defense against cyber threats. This control is important because it reminds us of the following risks:
- Human Risks in Security: Attackers often target users with tactics like social engineering attacks besides finding network exploits. The response of humans is crucial in the success or failure of an enterprise’s security defense.
- User-Caused Incidents: Users can cause security incidents intentionally or unintentionally. These incidents can compromise the security of an organization’s data, systems, or networks.
- Role-Based Security Risks: Role-based security risks refer to the specific vulnerabilities and threats associated with different roles which present distinct security challenges. Effective cyber risk management should be able to identify different roles and provide unique rights for them to access systems, networks and data.
What are the Control 14 Safeguards and how to implement them?
CIS emphasize that an effective security awareness training program should not just be a canned, once-a-year training video coupled with regular phishing testing. While annual training is needed, there should also be more frequent, topical messages and notifications about security. CIS suggest training programs to be:
- Continuous and Contextual: Security awareness training should be ongoing, with frequent, topical messages and notifications related to current threats, rather than just an annual training video.
- Role-Specific: Training programs should be tailored to the different roles within an organization. For example, credit card data handling training should be offered to the financial teams, while secure coding practices should be provided to software developers.
- Social Engineering Focused: Training should include awareness of social engineering tactics, such as phishing, psychological manipulation and other
advanced social engineering techniques.
As a recognized market leader in security awareness training, we are well-known for our comprehensive, engaging, and effective training programs. Our expertise and innovative approach ensure your workforce is well-equipped to recognize and respond to cyber threats. Join us and discover why so many organizations trust us to keep their workforce informed.
CIS Safeguard 14.1 – Establish and Maintain a Security Awareness Program
Requirements of CIS Safeguard 14.1 
What is a "Security Awareness Program"?
A security awareness program is a systematic training an organization should provide to its employees. The program is designed to educate employees about cybersecurity-related topics, such as security best practices, the importance of protecting sensitive information, how to recognize and respond to potential security threats etc. Click here to learn more.
Establishing and maintaining a security awareness program is crucial because employees often serve as the first line of defense against cybersecurity threats. A well-informed and trained workforce can significantly reduce the risk of security incidents.
How to choose a security awareness program that suits your business?
An efficient and effective way for SMBs to provide comprehensive training for employees is to purchase a security awareness program from a vendor. By choosing a reputable vendor, evaluating the program's features, and implementing it strategically, you can build a culture of security awareness in your organization at a low cost.

The content of a security awareness program can directly affect employees' ability to respond to security threats. Before you purchase any training program from a vendor, make sure the content they offer is:
-
Interactive and Engaging
Training should deploy various training methods such as videos, quizzes, simulations, and hands-on activities to make the training more engaging and effective. -
Tailored for Specific Roles
Training content should be customized to address the specific roles and responsibilities of different employee groups. For example, IT staff may require more technical training compared to general office staff. -
Regularly Updated
Training should include short tests or assessments to measure employees' understanding. This can help identify areas where additional training may be needed.
What else should I pay attention to when providing security awareness training to my employees?
-
Training Frequency
- At Hire: New employees should receive security awareness training as part of their onboarding process. This ensures they start their roles with a clear understanding of the organization's security policies and practices.
- Annually (at least): All employees should undergo refresher training at least once a year. This helps to reinforce the knowledge and address any new or evolving security threats.
-
Content Review and Update
- The content of the security awareness program should be reviewed and updated regularly. This ensures that the information remains current and relevant.
- Additionally, the program should be updated whenever significant changes occur within the organization that could impact security. For example, if the company adopts new technologies, undergoes organizational restructuring, or faces new regulatory requirements, the training content should be revised accordingly.
CIS Safeguard 14.2 – Train Workforce Members to Recognize Social Engineering Attacks
Requirements of CIS Safeguard 14.2
Training workforce members to recognize these attacks is crucial in preventing breaches and protecting sensitive data.
What are "Social Engineering Attacks"?
Social engineering attacks exploit human psychology and behavior to gain unauthorized access to an organization's assets, such as information, networks, systems, or physical locations. We've put together the most commonly seen social engineering attacks in the chart below.
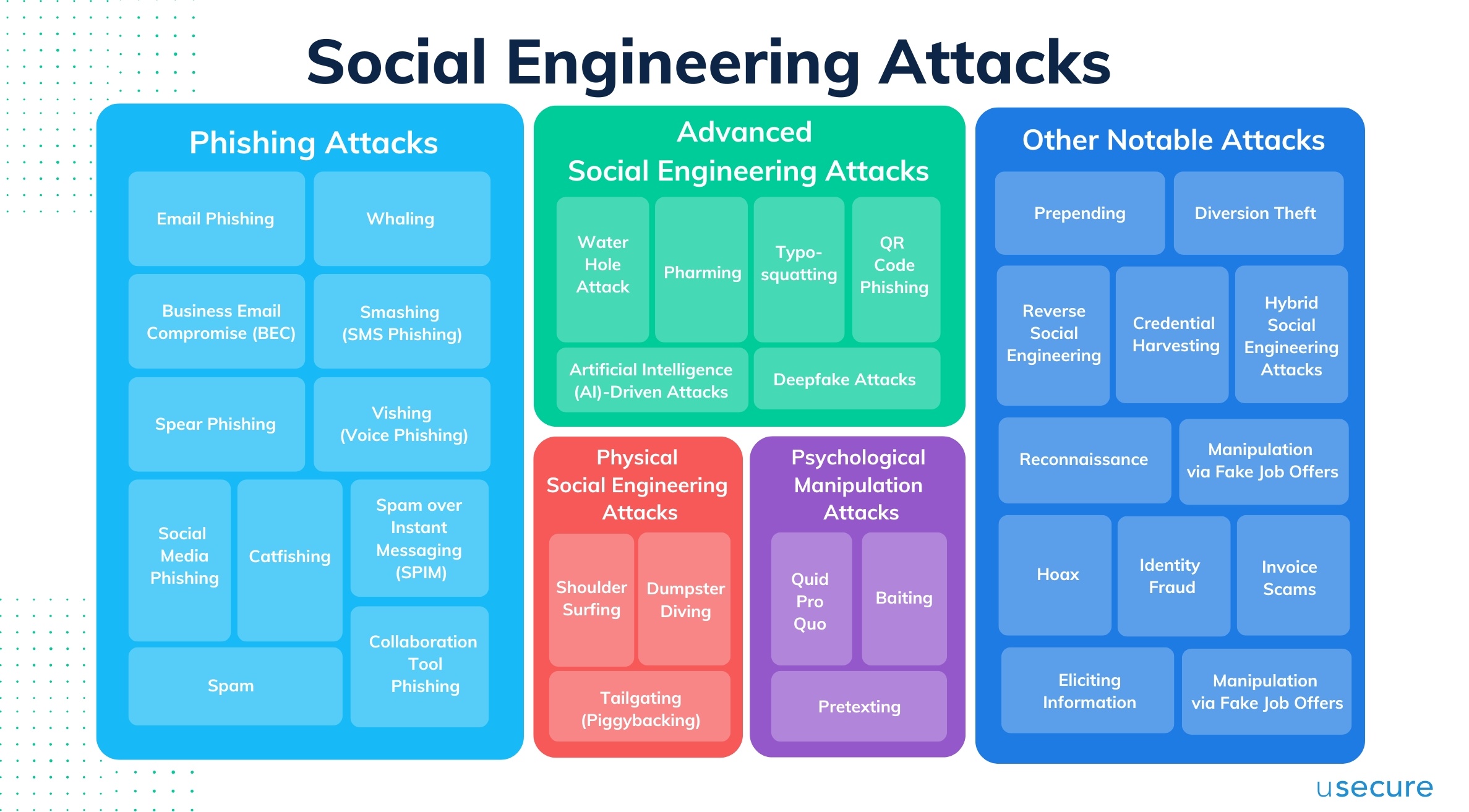
Psychological and behavioral tactics that social engineering attacks exploit
Social engineering attacks exploit various aspects of human psychology and behavior to deceive individuals into divulging confidential information or performing actions that compromise security. Understanding these psychological principles can help in developing effective defenses against such attacks.
- Trust
Attackers often impersonate trusted individuals or entities (e.g., colleagues, friends, reputable companies) to gain the target's confidence. - Authority
People tend to comply with requests from figures of authority or those perceived as having higher status. Bad actors would take advantage of these psychological weaknesses. - Fear and Urgency
Cybercriminals often create a sense of urgency or fear to cause individuals to act quickly without fully considering the consequences. - Reciprocity
People feel obligated to return favors or kindness. Attackers would provide a small gift or helpful information and then request a favour in return, such as access to sensitive data. - Scarcity
Frauds would create scarcity or the perception of a limited-time offer to pressure individuals into making hasty decisions. - Liking
Attackers would build a friendly relationship in the beginning with the target to make them more likely to comply with requests. - Social Proof
People like to take reference of other people's actions and behaviors to determine their own. Attackers would make use of this tendency. For example, attackers would send an email claiming that many other people have already completed a fake security update process to encourage the recipient to do the same. - Commitment and Consistency
Once individuals commit to something, they are more likely to follow through to maintain consistency. An attacker would get the target to agree to a small, seemingly harmless request, followed by larger requests. - Curiosity
Humans have a natural desire to know more, especially about intriguing information. Frauds would send phishing emails with subject lines promising exclusive or shocking news, enticing the recipient to click on a malicious link. - Overconfidence and Cognitive Biases
Overconfidence could limit one’s ability to detect scams or manipulation. For example, an employee who believes they are too savvy to fall for scams may neglect security protocols, making them an easy target.
Our regularly updated, well-designed training content provides insights into new attack vectors, real-world examples and tips for enhancing security, to help you better protect your organizational data.
CIS Safeguard 14.3 – Train Workforce Members on Authentication Best Practices
Requirements of CIS Safeguard 14.3
What is "Authentication"?
Authentication is the process of verifying the identity of a user, device, or entity in a system. Various types of authentication methods can be employed to ensure secure access.
What authentication best practices should be included in the training?
Authentication best practices are essential for ensuring the security of user accounts and protecting sensitive information. Teach your employees these key best practices to defend your organization's security. 
- Use Strong and Unique Passwords
Encourage the creation of complex passwords that include a mix of letters, numbers, and special characters. Avoid using easily guessable information such as birthdays or common words. - Implement Multi-Factor Authentication (MFA)
Implement MFA wherever possible to add an extra layer of security. This typically involves something the user knows (password) and something the user has (a mobile device or hardware token). - Perform Regular Password Updates
Require users to change their passwords periodically and ensure they do not reuse old passwords. Implement password expiration policies to enforce this practice. - Use Password Managers
Encourage the use of password managers to store and generate strong passwords securely, reducing the risk of weak or reused passwords. - Implement Account Lockout Mechanisms
Implement account lockout mechanisms after a certain number of failed login attempts to protect against brute force attacks. - Secure Password Recovery Options
Ensure that password recovery options are secure, such as using MFA for password resets and avoiding security questions with easily guessable answers. - Monitor Suspicious Activity
Use monitoring tools to detect unusual login activities and set up alerts for potential security breaches, such as logins from unfamiliar locations or devices. - Encrypt Authentication Data
Ensure that all authentication data, including passwords and tokens, is encrypted both in transit and at rest to prevent unauthorized access. - Implement Secure Authentication Protocols
Implement secure authentication protocols such as OAuth, SAML, or OpenID Connect for application integration and single sign-on (SSO) to enhance security.

What is "Multi-Factor Authentication" (MFA) and how should I train employees on it?
MFA is using two or more ways to authenticate to a system. The three common factors for authentication are “something you know,” “something you have,” and “something you are.”
Example Training Content about Multi-Factor Authentication
When planning MFA training, you should do the following:
- Set the Objectives
For example, to educate employees on the importance of MFA to enhance account security. - Explain What MFA Is
Explain what MFA is and how it works by combining two or more independent credentials: something you know (password), something you have (smartphone or hardware token), and something you are (biometrics). - Highlight the Importance
Highlight the added security that MFA provides by making it more difficult for attackers to gain access even if they obtain the password. - Give Examples
Demonstrate the use of authentication apps like Google Authenticator, Microsoft Authenticator, or physical security keys like YubiKey. - Add Interactive Components
You could conduct a live demo of setting up MFA on a commonly used platform and have employees follow along on their own devices.
What is "Password Composition" and how to train employees on it?
Password composition refers to the specific elements and criteria used to create a strong, secure password. A well-composed password is designed to be difficult for attackers to guess or crack while remaining manageable for users to remember.
Example Training Content about Password Composition
When planning training, you should do the following:
- Set the Objective
For example, to teach employees how to create strong, unique passwords. - Explain the Characteristics of Strong Passwords
Let staff know that strong passwords should be at least 12 characters long, and include a mix of uppercase and lowercase letters, numbers, and special characters. - Help Employees Avoid Common Pitfalls
Warn against using easily guessable information like birthdays, common words, or patterns (e.g., “password123”). - Introduce Password Managers
Introduce password managers as tools to generate and store complex passwords securely. Provide examples of popular password managers like LastPass, Dashlane, or 1Password. - Encourage Regular Updates
Emphasize the importance of changing passwords regularly and avoiding password reuse across multiple accounts. - Add Interactive Components
You could conduct a password strength challenge where employees test the strength of their passwords using a password checker tool.
What is "Credential Management" and how to train employees on it?
Credential Management refers to the processes and tools used to securely store, manage, and handle authentication information, such as usernames, passwords, security tokens, and digital certificates. Effective credential management helps ensure that sensitive authentication data is protected from unauthorized access, breaches, and misuse.
Example Training Content about Credential Management
When planning training, you should do the following:
- Set the Objectives
For example, to educate employees on how to manage and protect their credentials effectively. - Introduce Secure Storage
Reinforce the importance of storing passwords in secure places, such as password managers, and avoiding writing them down on paper or storing them in plain text files. - Train Employees to Recognise Phishing
Train employees to recognize phishing attempts aimed at stealing credentials by showing examples of phishing emails and explaining the red flags. - Train Employees to Use Secure Password Recovery
Teach employees to use secure methods for password recovery, such as security questions and recovery email addresses. - Encourage Employees to Monitor Suspicious Activities
Encourage employees to set up alerts for suspicious activities on their accounts, such as login attempts from unknown locations or devices. - Add Interactive Components
You could conduct a phishing simulation exercise to help employees practise recognizing and reporting phishing attempts.
There is so much more about authentication we should get to know about, such as how different types of authentication work, their unique characteristics and benefits, and how to choose the best type that suits your business. Contact us to learn more about them and strengthen your security defense.
CIS Safeguard 14.4 – Train Workforce on Data Handling Best Practices
Requirements of CIS Safeguard 14.4

What should I teach my employees about data?
Data is prolific in today’s business and computing environment, from PII to credit card information to browsing history. Numerous regulations, laws, and industry standards must be considered to maintain the security of this massive amount of data.
Data can be classified into different types and grades depending on its nature and confidentiality. Each data classification type is subject to specific rules and regulations about usage, storage, and retention. For example, medical data has to adhere to the Health Insurance Portability and Accountability Act (HIPAA) regulations, while credit card data is required to meet the PCI DSS standards.
- Data classification
Data can be classified with specific designations and can vary from entity to entity. Generally, it can be categorized as public data, private data, sensitive data, confidential data, critical data and proprietary data. - Data types
There are many different types of data, but the most common ones that we come across nowadays are personally identifiable information (PII), health information, financial information, government data and customer data.
How to train the workforce on data handling?
Data handling refers to the processes and practices involved in managing data throughout its lifecycle. This includes identifying, storing, transferring, archiving, and destroying data. Effective data handling is critical to ensure data integrity, confidentiality, and availability, as well as compliance with legal and regulatory requirements.

To effectively educate your staff on data handling, follow our best practices below to map out your training:
1. Identify Sensitive Data
- Teach employees how to recognize different types of sensitive data.
- Explain what constitutes sensitive data, such as personally identifiable information (PII), financial records, healthcare information, and confidential business information.
- Provide specific examples relevant to your organization, such as customer contact details, employee social security numbers, financial statements, and intellectual property.
- Include a quiz with various scenarios asking employees to identify which information is considered sensitive.
2. Properly Store Sensitive Data
- Ensure employees know how to securely save sensitive data in physical or digital formats.
- Stress the importance of encrypting sensitive data both in transit and at rest.
- Implement role-based access controls (RBAC) to ensure only authorized personnel can access sensitive data.
- For physical documents, use locked cabinets and restrict access to authorized personnel only.
- Give employees opportunities to practise setting up encryption on files and using secure storage solutions.
3. Transfer Sensitive Data
- Train employees on securely distributing data to authorized users or systems.
- Provide secure transfer methods. In your organization, use secure transfer methods like encrypted emails, secure file transfer protocols (SFTP), and virtual private networks (VPNs).
- Practise verification. Always remind employees to verify the recipient's identity before sending sensitive data.
- Remind employees to avoid transferring sensitive data over unsecured public networks.
- Simulate a situation where employees must transfer sensitive data securely, highlighting the steps to take and common pitfalls to avoid.
4. Archive Sensitive Data
- Ensure employees understand how to archive sensitive data that is no longer actively used to a separate storage system for long-term retention.
- Provide secure, encrypted storage solutions to your employees for archiving sensitive data.
- Archived data should be stored securely and remain accessible when needed.
- Determine appropriate retention periods based on legal and business requirements.
- Apply access control to limit access to archived data to authorized personnel only.
- You could review a case where proper archiving prevented a data breach, discussing the best practices with your employees.
5. Destroy Sensitive Data
- Teach employees how to properly dispose of sensitive data that is no longer needed.
- Teach them how to destructure digital data. For example, use secure methods such as data wiping software, degaussing, or physical destruction of storage devices.
- Teach them how to destructure physical data. For example, shred paper documents containing sensitive information before disposal.
- Ensure data destruction methods comply with relevant regulations and industry standards.
- Demonstrate how to securely destroy both digital and physical data.
How to train employees on Clear Screen and Desk best practices?
Clear Screen and Desk Policies are practices that help protect sensitive information from unauthorized access and ensure that workspaces remain tidy and professional. Follow these key points to train your employees on this topic.
Clear Screen and Desk Best Practices Training
- Develop Daily Routines: Incorporate clear screen and desk practices into daily routines.
- Advocate End-of-Day Routine: Clear desks of all papers, lock away sensitive documents and log off or shut down computers.
- Meeting Practices: Ensure meeting rooms are cleared of all materials and whiteboards are erased after each use.
- Regular Reminders: Provide regular reminders through emails, posters, or internal communications to reinforce these practices.
- Checklist: Provide a checklist for employees to follow at the end of each day to ensure all clear screen and desk practices are followed.
Want your employees to learn how to classify the data your organization possess and what their roles and responsibilities are in protecting data? We have more to offer. Get in touch with us today!
CIS Safeguard 14.5 – Train Workforce Members on Causes of Unintentional Exposure
Requirements of CIS Safeguard 14.5
Unintentional data exposure occurs when sensitive information is inadvertently made accessible to unauthorized individuals or the public. This can happen due to a variety of causes, often rooted in human error or technical misconfigurations. The following are the five common causes of unintentional data exposure that your employees should be aware of:
Mis-Delivery of Sensitive Data
- Sending sensitive information to the wrong recipient by mistake. For example, an email containing confidential information sent to the wrong person due to a typo or autofill error.
- How to prevent it?
Double-check email recipients, use email encryption, and implement a review process before sending sensitive information.
- How to prevent it?
Losing Portable End-User Devices
- Loss of devices such as laptops, smartphones, or USB drives that contain unencrypted sensitive client data.
- How to prevent it?
Use device encryption, enforce strong passwords, and establish policies for reporting lost or stolen devices immediately.
- How to prevent it?
Publishing Data to Unintended Audiences
- Restricted internal data accidentally being made publicly accessible through incorrect settings on websites, cloud services, or collaboration platforms.
- How to prevent it?
Review access permissions, implement access controls, and train employees on proper data-sharing practices.
- How to prevent it?
Phishing and Social Engineering Attacks
- Employees are tricked into divulging sensitive information such as login credentials through deceptive emails to a fake website linked in a phishing attack.
- How to prevent it?
Conduct regular phishing awareness training, use email filters, and implement multi-factor authentication.
- How to prevent it?
Human Error in Data Handling
- Mistakes made while handling data, such as copying sensitive files to insecure locations, such as a publicly accessible folder on a server, or misconfiguring access controls.
- How to prevent it?
Train employees on data handling best practices and implement automated tools to monitor and manage data access.
- How to prevent it?
Unintentional data exposure can have serious consequences. Learn with us to understand what technologies can be applied to monitor and manage data access to reduce the risk of accidental data exposure.
CIS Safeguard 14.6 – Train Workforce Members on Recognizing and Reporting Security Incidents
Requirements of CIS Safeguard 14.6

What is a "Security Incident"?
A security incident is an event that threatens the integrity, confidentiality, or availability of an information system, data, or network. Security incidents can range from minor data breaches to significant cyber-attacks and can result from both intentional and unintentional actions.
Types of security incidents your IT team should be aware of:
- Unauthorized Access: Someone gains access to data, systems, or networks without permission.
- Data Breach: Unauthorized acquisition, disclosure, or use of data.
- Malware Infection: Malicious software infiltrates a system, causing damage or unauthorized actions.
- Denial of Service (DoS) Attack: An attack that aims to make a service unavailable by overwhelming it with traffic.
- Insider Threat: Security risks that originate from within the organization.
- Social Engineering Attack: Manipulating individuals into divulging confidential information.
- Physical Security Breach: Unauthorized physical access to facilities or hardware.
- Configuration Errors: Misconfigurations in systems or networks that expose them to vulnerabilities.
- Loss of Devices: Loss of physical devices containing sensitive information.
How to look for potential incidents on my network?
These are some useful indicators of a security incident:
- Unusual System Behavior: Unexpected crashes, slow performance, or abnormal application behavior.
- Unauthorized Changes: Unexplained modifications to files, settings, or system configurations.
- Unexpected Network traffic: Unusual patterns or volumes of network traffic that deviate from the norm.
- Security Alerts: Warnings from security software about potential threats or breaches.
- Suspicious Emails: Receiving emails that request sensitive information or contain unfamiliar attachments/links.
- Access Attempts: Multiple failed login attempts or access from unusual locations/IP addresses.
What steps should your IT team follow to tackle an incident?

Reporting a security incident promptly and effectively is crucial for minimizing damage and ensuring a swift response. To achieve this, you should have procedures in place.
- Identification: Identify and verify what security incident has occurred.
- Containment: Limit the scope and impact of the incident to prevent further damage.
- Eradication: Remove the cause of the incident, such as deleting malware or closing vulnerabilities.
- Recovery: Restore affected systems and data to normal operation.
- Communication: Inform relevant stakeholders about the incident and response measures.
- Documentation: Document all aspects of the incident and response efforts for future reference and improvement.
- Post-Incident Analysis: Analyze the incident to identify lessons learned and improve future response strategies.
Want to establish an incident reporting process within your organization? Contact us to learn more about our related courses.
CIS Safeguard 14.7 – Train Workforce on How to Identify and Report if Their Enterprise Assets are Missing Security Updates
Requirements of CIS Safeguard 14.7

What are "Security Updates"?
Security updates are patches or software modifications issued by software vendors to fix vulnerabilities and enhance the security of their products. These updates are designed to protect systems from potential threats and are crucial for maintaining the integrity and security of software applications.
How your IT team can teach users to report out-of-date software patches and failures
Ensuring employees can verify and report out-of-date patches or failures is important for maintaining a secure and efficient IT environment. Consider these training components:
-
Educate Users about the Importance of Software Updates
Your IT team could explain how outdated software can be exploited by attackers, and highlight how updates can improve software performance. They could also share case studies or examples of security breaches caused by outdated software.
-
Verifying Software Updates
IT team could train employees on implementing software updates. For example, they could explain the difference and importance of both automatic and manual updates. demonstrate how to check for updates on different operating systems (e.g., Windows, macOS). They could also show users how to check for updates in commonly used applications (e.g., browsers, office suites). Hands-on practice is useful. You should invite your employees to practice checking for updates on their devices.
-
Identifying Failures in Automated Processes
Your IT team could use automated processes and tools to help users recognize signs of failures. For example, teach users how to identify error messages, unresponsive tools or irregular system behaviour.
-
Reporting Issues
Have your IT staff establish clear procedures for reporting out-of-date software and failures in automated processes. For example, detail the information that should be included in a report, such as the software name, current version, observed issues, and any error messages. They could also introduce the appropriate channels for reporting issues, such as helpdesk tickets, email, or internal reporting systems.
-
Notifying IT personnel
IT team can ensure employees know how to notify them of any failures in automated processes and tools. For example, encourage direct communication with IT personnel for critical issues. They could also simulate a situation where an employee must notify IT personnel of a critical issue.
To fight security incidents together, we have more professional tips for you in our security awareness training courses. Get in touch with us now!
CIS Safeguard 14.8 – Train Workforce on the Dangers of Connecting to and Transmitting Enterprise Data Over Insecure Networks
What is "Network Security"?
How to identify insecure networks?
- Lack of Encryption: Networks that do not use WPA2 or WPA3 encryption are insecure. Older protocols like WEP are considered weak and easily compromised.
- Open Networks: Networks that do not require a password to connect are open and insecure, making them susceptible to eavesdropping and unauthorized access.
- Unrecognized Network Names: Connecting to networks with unfamiliar names, especially in public places, can be risky. Attackers may set up rogue access points with names similar to legitimate networks to deceive users.
- No HTTPS: When accessing websites over an insecure network, ensure the connection is HTTPS. If it’s not, any data transmitted can be intercepted easily.
- Unusual Network Behavior: Slow network performance, frequent disconnections, and unexpected pop-ups can indicate a compromised network.
- Warnings from Security Software: Alerts or warnings from anti-virus or security software about the network or specific activities on the network.
How to ensure your remote workers securely configure their home network infrastructure?
1. Raise Their Awareness
- Educate them on the importance of securing home networks.
- Highlight the risks associated with unsecured home networks and the benefits of securing them.
- Explain how unsecured networks can be exploited by attackers, leading to data breaches and unauthorized access.
- Share case studies or incidents where insecure home networks led to security breaches.
2. Teach Them to Configure Their Home Routers
- Teach employees how to securely configure their home routers.
- Changing default settings is important. Explain why it's a must to change default usernames and passwords for routers.
- Pay attention to firmware updates. Show how to regularly check for and install firmware updates to keep routers secure.
- Encryption settings are crucial. Guide employees on setting up WPA3 or WPA2 encryption for their Wi-Fi network.
3. Set Up a Guest Network for Remote Workers
- You could set up a separate guest network for your remote staff and encourage them to use it. This is a network segmentation strategy to isolate them and their IoT devices from your organization's main network.
4. Enable Firewalls
- Teach remote workers how to enable and configure their router’s built-in firewall as well as the firewalls on their devices (e.g., computers, smartphones).
5. Promote the Use of VPNs
- Promote the use of Virtual Private Networks (VPNs) for secure remote access.
- Explain how VPNs encrypt internet traffic, providing a secure connection to the enterprise network.
- Guide them on setting up and connecting to the company’s VPN.
6. Router Recommendations
-
Suggest reliable and secure router models and if possible, provide discounts or purchase support.
7. Use a Secure Remote Access Tool
- Use a trusted and secure remote access tool to ensure remote workers' configuration processes are safe and encrypted.
- You should ensure that workers are aware of and agree to the remote session to respect their privacy.
Ensuring that remote workers securely configure their home network infrastructure is essential to protect sensitive enterprise data. Learn more about it with our security courses.
CIS Safeguard 14.9 – Conduct Role-Specific Security Awareness and Skills Training
Requirements of CIS Safeguard 14.9

Conducting role-specific security awareness and skills training to address the unique challenges and threats each role faces can rapidly improve your organization's overall security posture.
Steps to conduct role-specific security awareness and skills training
-
Identify Roles and Responsibilities
Understand each role within the organization and its associated responsibilities. Create a comprehensive list of roles and map out their access to systems, data, and their potential impact on security. -
Assess role-specific risks
Identify the unique security risks and challenges associated with each role. Conduct a risk assessment for each role to determine the specific security threats they face. -
Develop customized training content
Create training content tailored to the needs and responsibilities of each role. Design training modules that address the specific security risks, best practices, and compliance requirements relevant to each role.
Examples of role-based training

Secure System Administration Courses for IT Professionals
- Objective:
Ensure IT professionals understand secure system administration practices and can effectively manage and protect IT infrastructure. -
Key topics to cover:
-
Access Control and Privilege Management: Best practices for managing user privileges and access controls.
-
Patch Management: Procedures for applying security patches and updates.
-
Network Security: Configuring firewalls, intrusion detection/prevention systems, and VPNs.
-
Incident Response: Steps for identifying, responding to, and mitigating security incidents.
-
Backup and Recovery: Implementing and managing backup and disaster recovery plans.
-
OWASP Top 10 Training for Web Application Developers
- Objective:
Educate web application developers on common vulnerabilities and secure coding practices to prevent security flaws. - Key topics to cover:
- OWASP Top 10: Detailed overview of the OWASP Top 10 vulnerabilities, including injection attacks, broken authentication, and cross-site scripting (XSS).
- Secure Coding Practices: Techniques for writing secure code, input validation, and output encoding.
- Code Review and Testing: Methods for conducting secure code reviews and using automated testing tools to identify vulnerabilities.
- Authentication and Authorization: Best practices for implementing secure authentication and authorization mechanisms.
- Secure Development Lifecycle (SDL): Integrating security into the software development lifecycle.
Advanced Social Engineering Awareness Training for High-Profile Roles
- Objective: Equip high-profile employees (e.g., executives and finance personnel) with the knowledge to recognize and defend against sophisticated social engineering attacks.
- Key topics to cover:
- Types of Social Engineering Attacks: Phishing, spear-phishing, vishing (voice phishing), whaling and physical social engineering etc.
- Recognizing Red Flags: Identifying suspicious emails, phone calls, and other communication attempts.
- Personal Security: Best practices for protecting personal information online and offline.
- Incident Response: Steps to take if targeted by a social engineering attack, including reporting and mitigation.
- Real-World Scenarios: Case studies of high-profile social engineering attacks and their impact.
Master CIS Controls and build your security defense today!
We offer a comprehensive and adaptive training platform that tailors security awareness programs to the specific needs of each role within an organization, ensuring that all employees, regardless of their technical background, receive relevant and up-to-date training to effectively counter emerging threats. Get in touch with us now! Alternatively, you can take a look at our blog to learn how usecure could help you navigate regulations and standards around the world.

.png)
.png)