usecure Announces New Distribution Partnership with Northamber
usecure has launched a new distribution partnership with Northamber, expanding UK channel access to its Human Risk Management...
Resource Center

usecure has launched a new distribution partnership with Northamber, expanding UK channel access to its Human Risk Management...
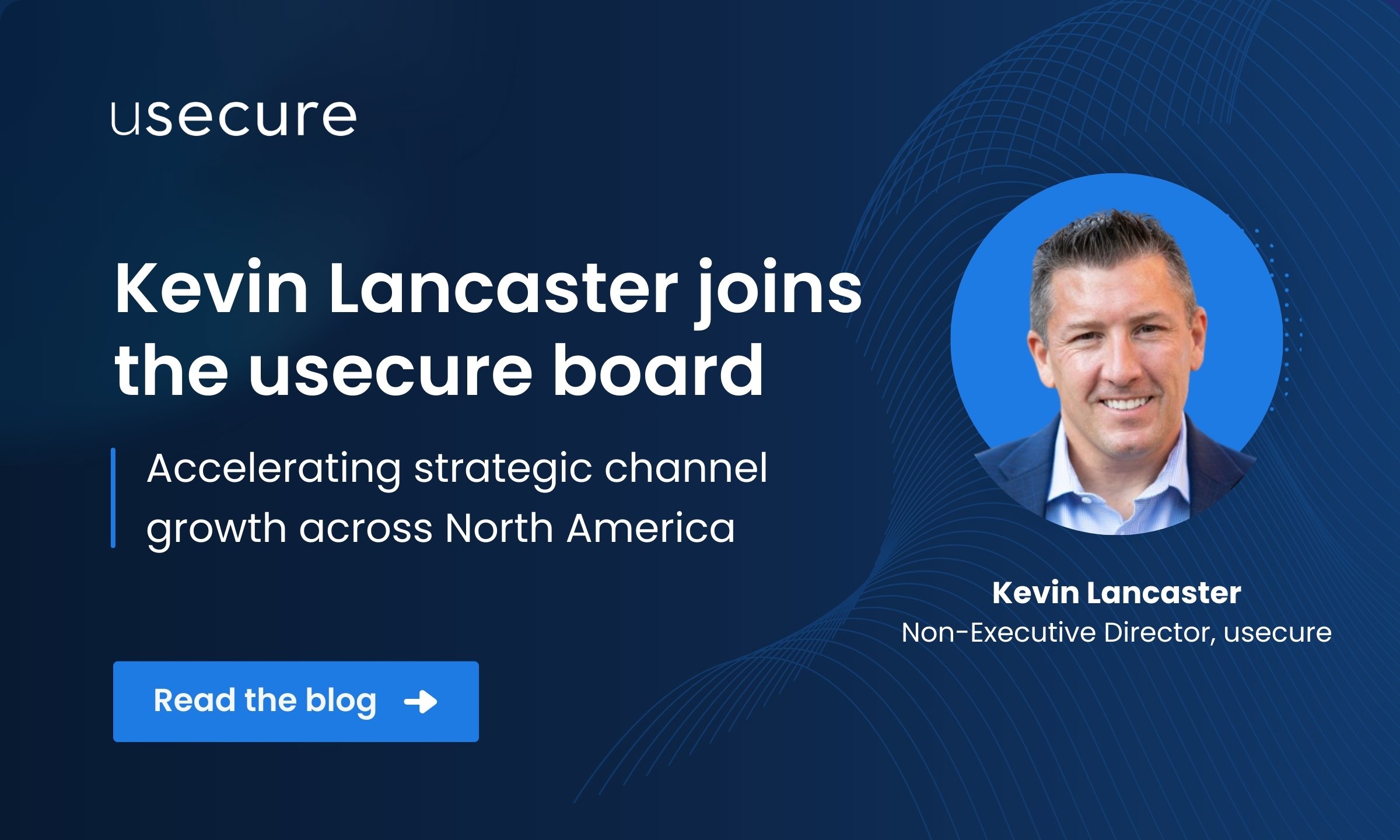
Kevin Lancaster joins usecure as a Non-Executive Director, strengthening our North American channel growth and accelerating...
-2.png)
Seasonal scams rise sharply from Black Friday through the new year. Explore targeted training, realistic phishing simulations and...
-3.jpg)
Ten Channel experts share quick tips on using AI to stay competitive in 2026.
.png)
Watch usecure’s final 2025 webinar on-demand. Explore key cybersecurity lessons, human risk trends, and 2026 predictions - plus a...
.jpg)
usecure Sponsors Channel Program’s Holidaze 2025 The most festive event of the MSP year is here — and usecure are proud to be part...

Learn what the EU’s Digital Operational Resilience Act (DORA) means for SaaS vendors in the years ahead, how it affects...

Discover November's updates: new AI courses, fraud awareness resources, and platform improvements to help partners and customers...
.png)
Join usecure’s final 2025 webinar to explore key cybersecurity lessons, human risk trends, and 2026 predictions - plus a first...

Discover October's latest updates from usecure, including enhanced phishing simulations, new training resources, & tools for...