PCI DSS v4.0: Is your business ready to navigate the changes?
The Payment Card Industry Data Security Standard (PCI DSS) is a global standard that provides a baseline of technical and operational requirements designated to protect payment data. PCC DSS is constantly updated to address emerging threats or to incorporate best practices in data security.
With the new version – PCI DSS v4.0 coming into effect on 1st April 2024, the standard reaffirms its commitment to securing cardholder data by adding new requirements to its compliance process. Let's dive into the details of PCI DSS to learn more about its crucial updates and new requirements for handling payment card data.
In this blog, we’ll cover:
- What is PCI DSS?
- Who does PCI DSS apply to?
- What are the differences between PCI DSS v3.2.1 and v4.0?
- What are the major highlights of PCI DSS v4.0?
- What are the consequences of non-compliance with PCI DSS?
- Comply with PCI DSS in 6 actionable steps
What is PCI DSS?
PCI DSS is an information security standard aimed at managing credit card information securely, enhancing the security of cardholder information and diminishing the incidence of credit card fraud.
The standard is administered by the Payment Card Industry Security Standards Council (PCI SSC). The Executive Committee of the PCI Security Standards Council is composed of six leading payment brands: American Express, Discover Financial Services, JCB International, MasterCard, Visa Inc., and UnionPay. These major entities collaborate to set and enforce the PCI SSC.
Who does PCI DSS apply to?
PCI DSS is a compulsory standard to which any entity is involved in handling cardholder data. Whether through processing, transmission, or storage, any entity is required to adhere to the PCI DSS.
Merchants of any size accepting credit cards must be in compliance with PCI DSS. It's important to note that the requirements of PCI DSS extend to merchants who have outsourced their payment card operations to a third-party provider.
What are the differences between PCI DSS v3.2.1 and v4.0?
At its core, PCI DSS is built upon 12 foundational requirements, structured around six goals. The standard can be updated from time to time to address emerging threats or to incorporate best practices in data security. Here is a comparison of PCI DSS v3.2.1 and v4.0.
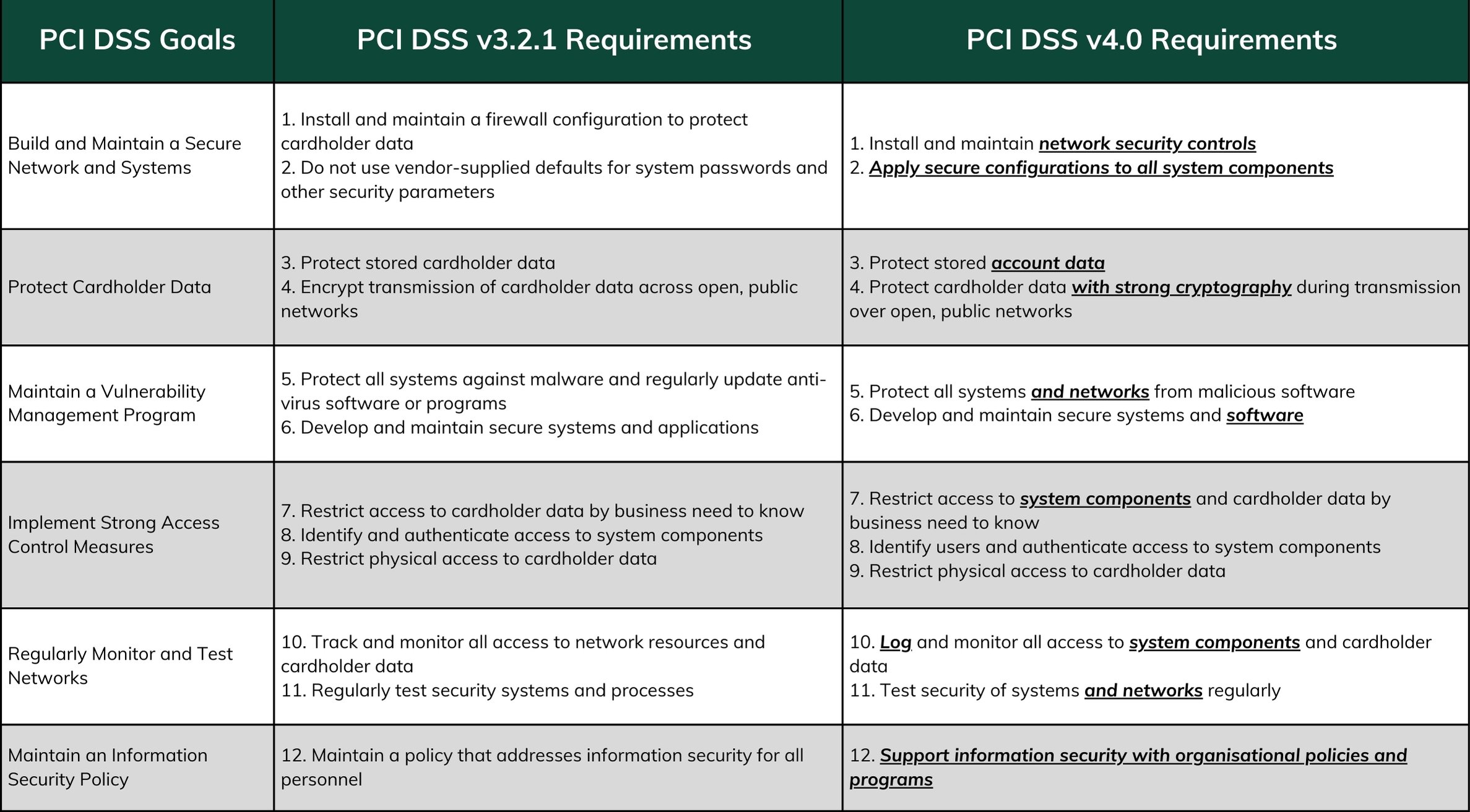 Source of information: PCI SSC
Source of information: PCI SSC
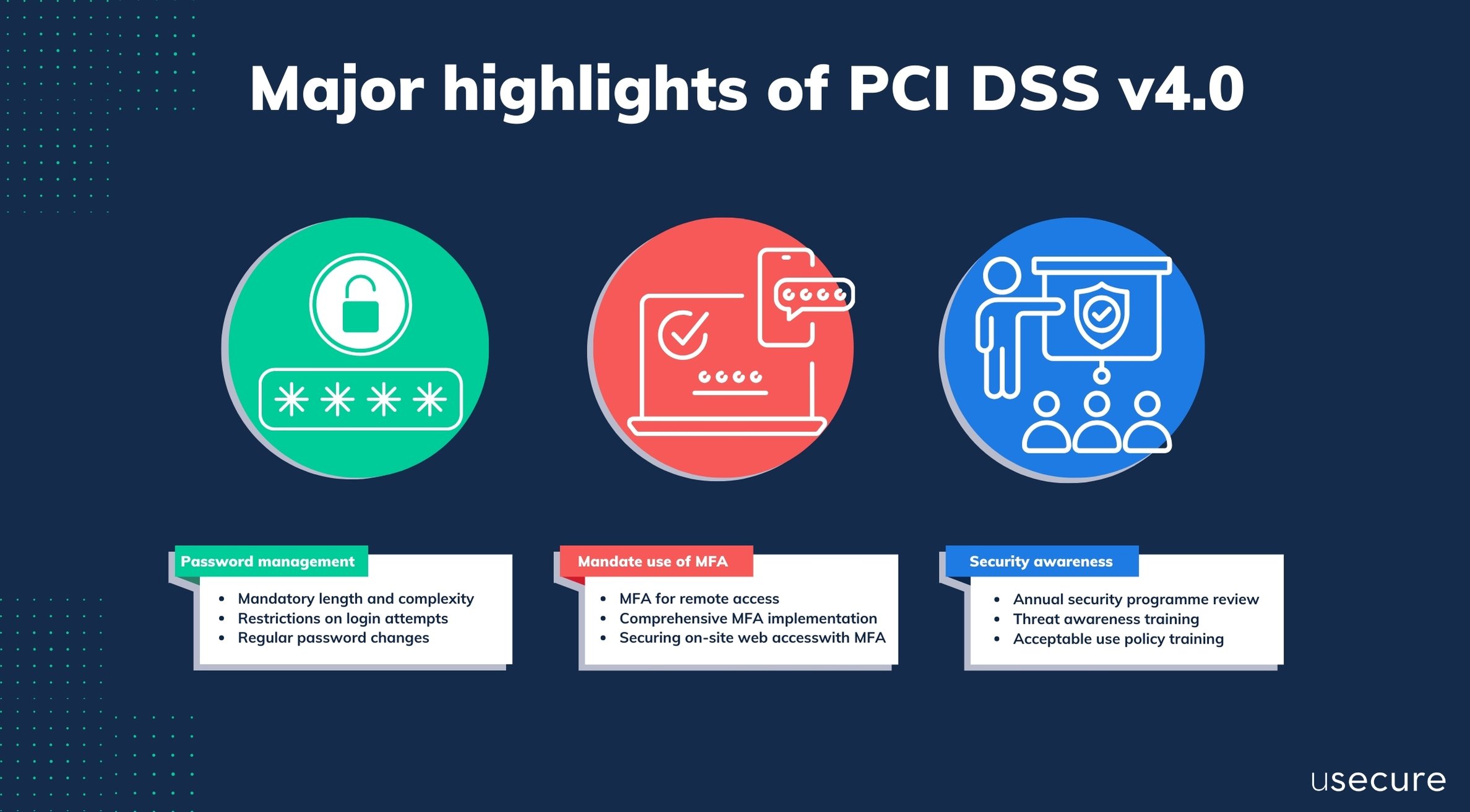
What are the major highlights of PCI DSS v4.0?
-
More rigorous requirements for password management
The new version of PCI DSS v4.0 introduces more rigorous requirements for password management. The detailed requirements are outlined in sections 8.3.4 to 8.3.9.- Mandatory length and complexity: Passwords now need to be at least 12 characters long, emphasising the necessity for both length and complexity to bolster security.
- Restrictions on login attempts: The standards specify that after 10 unsuccessful attempts to log in, a user account should be temporarily locked for a minimum duration of 30 minutes or until the user successfully verifies their identity, possibly through a help desk or similar verification process.
- Regular password changes: It is now mandatory to update passwords every 90 days, with a prohibition on recycling previous passwords. However, risk-based authentication that evaluates the security status of accounts in real-time, can be exempt from the regular reset requirement.
-
Mandate the use of multi-factor authentication (MFA)
The new version of PCI DSS specifically requires the use of MFA for access control. Details can be found in section 8.4.
-
MFA for remote access: PCI DSS v4.0 now mandate the use of MFA for remote access, broadening its scope beyond just accessing the cardholder data environment (CDE).
-
A comprehensive MFA implementation: This expansion of MFA requirements extends to every individual—be they employees, administrators, or external partners like third parties and vendors—attempting to connect from outside the organisation's secured network perimeter, regardless of their intention to access the CDE.
-
Securing on-site web access: The requirement encompasses web-based access within the organisation, necessitating MFA for all online application use on-site as well.
-
-
New emphasis on security awareness training
PCI DSS v4.0 has new emphasises outlined in sections 12.2 and 12.6 regarding the importance of security awareness training.
-
Annual security programme review: PCI DSS v4.0 requires organisations to review and update (as needed) the security awareness program at least once every 12 months.
-
Threat awareness training: There is a new requirement for security awareness training to include awareness of threats that could impact the security of the CDE. SAT should also include phishing and related attacks and social engineering topics.
-
Acceptable use policy training: The new version of PCI DSS also requires security awareness training to include awareness about the acceptable use of end-user technologies in accordance with the requirement.
-
These updates to the password, MFA and SAT requirements in PCI DSS 4.0 reflect a significant enhancement towards data protection and access control. Take a look at our video to learn the basics of reducing the risk of unauthorised access.
What are the consequences of non-compliance with PCI DSS?
PCI DSS itself does not directly impose penalties; instead, penalties for non-compliance are enforced by the payment card brands and acquiring banks.
Businesses that fail to comply with PCI DSS may suffer from substantial fines, increased transaction fees, and in severe cases, revocation of card processing privileges.
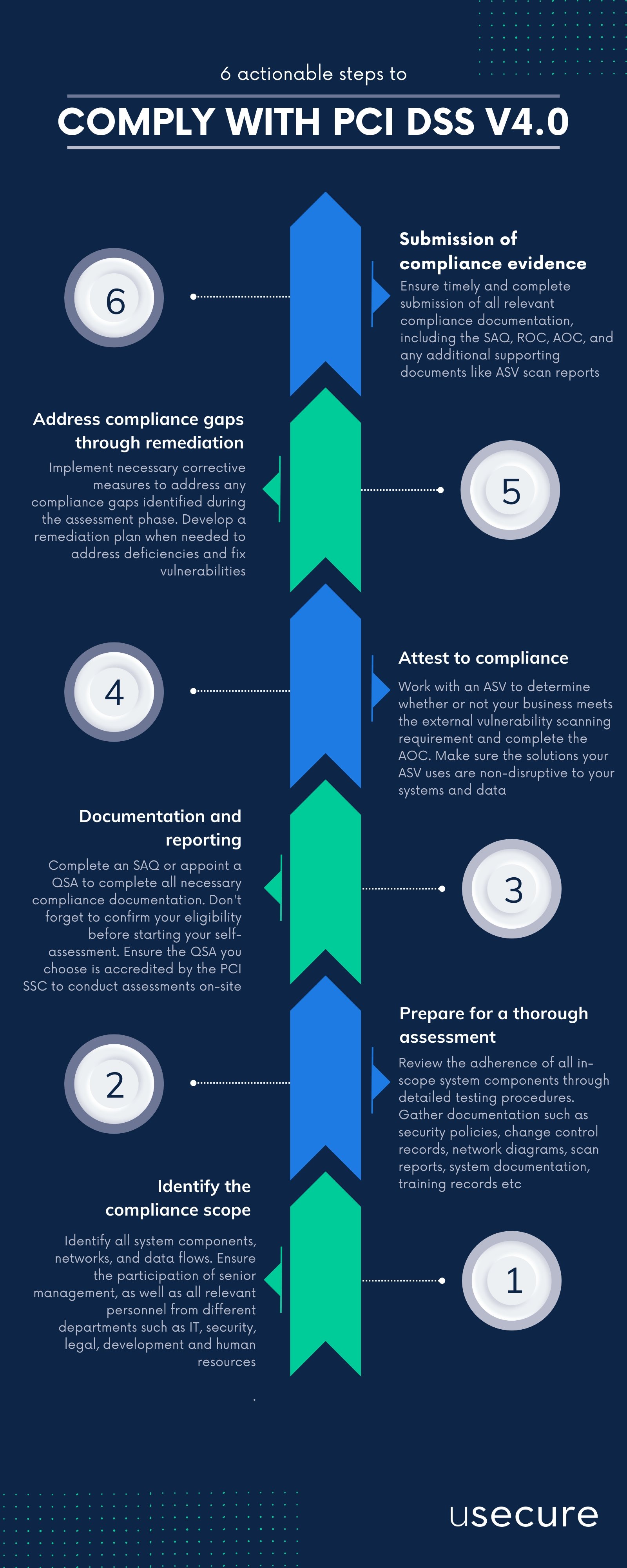
Comply with PCI DSS in 6 actionable steps
The path to comply with PCI DSS can be a complex process for merchants and organisations involved in the handling of cardholder data. Depending on an entity’s classification or risk level, processes for compliance usually follow these six steps.
-
Identify the compliance scope
Objective: Identify all system components, networks, and data flows that come into contact with cardholder data to clearly define the compliance scope.
Action points: Ensure the participation of senior management, as well as all relevant personnel from different departments such as IT, security, legal, development and human resources. -
Prepare for a thorough assessment
Objective: Review the adherence of all in-scope system components to the PCI DSS requirements through detailed testing procedures.
Action points: Engage in data gathering. Gather documentation such as security policies, change control records, network diagrams, scan reports, system documentation, training records and so on to ensure no aspect of the system that interacts with payment data is overlooked. -
Documentation and reporting
Objective: You could either use the PCI DSS Self-Assessment Questionnaires (SAQs) if your business is SAQ-eligible. You could also appoint a Qualified Security Assessor (QSA) to complete all necessary compliance documentation such as the SAQ or a Report on Compliance (ROC).
Action points: Businesses are responsible for confirming that they meet all eligibility criteria for a particular SAQ before starting their self-assessment. If a business chooses to work with a QSA, they should ensure the QSA is accredited by the PCI SSC to conduct assessments on-site. When choosing a QSA, make sure to select one that has a solid understanding of your business and has a proven track record in evaluating the security frameworks of businesses akin to yours. A list of QSAs is available at: www.pcisecuritystandards.org/assessors_and_solutions/qualified_security_assessors -
Attest to compliance
Objective: Work with an Approved Scanning Vendor (ASV) to determine whether or not your business meets the PCI DSS external vulnerability scanning requirement and complete the Attestation of Compliance (AOC).
Action points: An ASV is a data security firm qualified by the PCI Security Standards Council to perform external network and system scans as required by the PCI DSS.
You should be aware that an ASV is allowed to utilise its own software or an approved commercial or open-source solution to implement the scan. However, the solutions must be non-disruptive to your systems and data, meaning that they must never cause you a system reboot, or interfere with or change your domain name server (DNS) routing, switching, or address resolution. A list of ASVs is available at: www.pcisecuritystandards.org/assessors_and_solutions/approved_scanning_vendors. -
Address compliance gaps through remediation
Objective: Implement necessary corrective measures to address any compliance gaps identified during the assessment phase.
Action points: You may need to develop a remediation plan to address deficiencies and fix vulnerabilities that could threaten unauthorised access to cardholder data. After that, you should submit an updated compliance report demonstrating the resolution of previously identified issues. -
Submission of compliance evidence
Objective: Submit all relevant compliance documentation, including the SAQ, ROC, AOC, and any additional supporting documents like ASV scan reports, to the appropriate acquiring entity or payment brand.
Action points: Ensure timely and complete submission of all required documentation to facilitate the compliance verification process.
Keep pace with PCI DSS v4.0!
As businesses set sail towards compliance with PCI DSS v4.0, understanding the changes and starting the transition early is paramount. In usecure, we devote our expertise to help you learn and keep pace with the advancements in PCI DSS! Get to know more by watching a short demo or get in touch with us to unlock the 14-day free trial to experience our renowned security awareness training programme. Alternatively, you can take a look at our blog to learn how usecure could help you navigate regulations and standards around the world.


