Overcoming MFA fatigue attacks
Multi-factor authentication (MFA) fatigue is a relatively new kind of threat that has garnered increased attention lately, making headlines as the main technique used in several high-profile attacks and breaches.
Imagine being constantly bombarded with authentication requests to your mobile device, each vying for your attention and approval. For many, the reaction might be to simply approve the request to make the notifications stop. This, unfortunately, is exactly what certain threat actors bank on.
We’ll delve into the world of MFA fatigue attacks, shedding light on its mechanisms, manifestations, and most importantly, how you can safeguard against it.
In this blog, we’ll cover:
- What is multi-factor authentication (MFA)?
- What is MFA fatigue?
- The impact of MFA fatigue
- How do MFA fatigue attacks work?
- What are the platforms of MFA fatigue attacks?
- How to stop MFA fatigue attacks?
- Train your employees on MFA fatigue attacks
What is multi-factor authentication (MFA)?
Multi-factor authentication (MFA) is a security measure that adds an extra layer of protection to your online accounts. It requires users to provide two or more verification factors, such as a password, fingerprint, or a unique code sent to their mobile device. While MFA is an effective method to enhance security, it can also lead to a phenomenon known as MFA fatigue.
What is MFA fatigue?
MFA fatigue, also known as MFA bombing, refers to the weariness or frustration users may feel due to repeatedly going through multiple steps or processes to authenticate themselves when accessing various services or systems.
Attackers would send an endless stream of MFA push requests to the account holder’s chosen authentication devices, aiming to get the target people overwhelmed and finally get them to accidentally click the “Approve” button or simply accept the MFA request to end the flood of notifications sent to their devices.
These attacks rely on the users to approve a simple voice, SMS or click in an email or push notification that doesn’t require the users to have context of the session they are authenticating.
-
According to research findings provided by Azur, MFA fatigue attacks are on the rise, and this is expected to continue as basic multifactor authentication coverage increases.
The impact of MFA fatigue
MFA fatigue can have a significant impact on an organisation's security. When users experience fatigue, they may resort to using weaker authentication methods or disabling MFA altogether, leaving their accounts vulnerable to attacks.
additionally, MFA fatigue can negatively affect productivity and user experience. It can slow down the login process and create frustration, especially in situations where quick access is required.
-
Who can be targeted by MFA fatigue attacks?
Any user of MFA can be a target, especially if they aren't well-acquainted with the MFA attacks.
However, entities that don't have clear and secure communication channels for support-related queries and organisations that don't regularly update and educate their users about security best practices suffer a higher risk.
How do MFA fatigue attacks work?
Fake MFA prompts look exactly like genuine ones. Victims would receive emails, messages or phone calls urging actions relevant to accepting an MFA request.
An international extortion-focused hacker group, Lapsus$, highlighted the weaknesses of certain MFA options, specifically push approvals. One of their members has revealed the method their hackers utilise to steal notification approvals. Once they have the victim’s credentials, they would simply spam users with MFA prompts until they get approved.
-
Real-life example from Lapsus$
A member of Lapsus$ wrote on the group’s official Telegram chat channel, saying
“Call the employee 100 times at 1 a.m. while he is trying to sleep, and he will more than likely accept it. Once the employee accepts the initial call, you can access the MFA enrollment portal and enrol another device.”
Source: LAPSUS$ Telegram
What are the platforms of MFA fatigue attacks?
The MFA code or approval request will usually come through some type of “push” message. Users can receive it in a few ways:
-
Emails
Knowing that users are often bombarded with MFA prompts, a hacker might mimic these prompts in phishing campaigns, hoping that tired users will input their credentials without second-guessing the authenticity of the request. -
Work messaging platforms
Attackers could pose as IT support on work messaging apps, such as Teams, Slack or Discord. They could claim they are helping streamline or troubleshoot an MFA process, thereby tricking the user into sharing codes or even disabling MFA. -
SMSs
Attackers could make use of a leaked phone number and send a one-time passcode (OTP) in an SMS authentication prompting users to accept the request for authentication. -
Voice calls
Attackers could deliver a one-time passcode (OTP) in a voice call to the user's phone. Both a phone number for both mobile phones or landline, or even extension numbers could be possibly exploited.
If a user, frustrated by MFA, opts for weaker security alternatives, attackers might target these less secure points of entry.
How to stop MFA fatigue attacks?
Always keep in mind that human is often the weakest link in security. To overcome MFA fatigue attacks and maintain strong security, we can consider the following methods.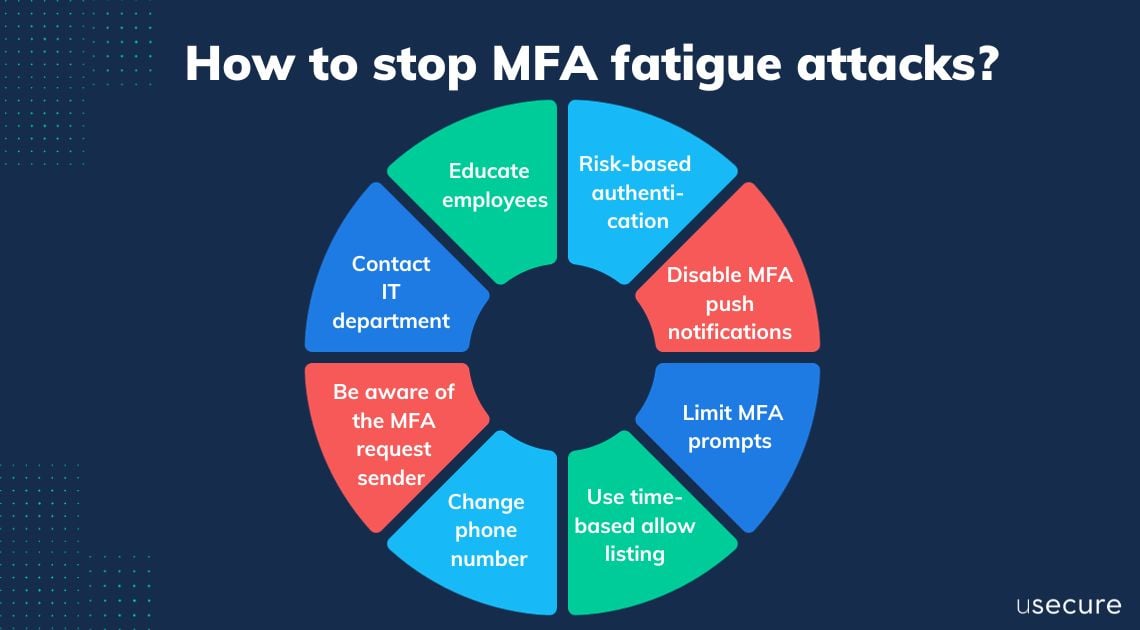
-
Use risk-based authentication
Risk-based authentication uses algorithms to assess the risk level of a login attempt. If the risk is deemed low, the user may be granted access without additional authentication steps, reducing the burden of MFA fatigue. -
Disable MFA push notifications
The MFA fatigue technique is only possible when the company’s multi-factor authentication is configured to use push notifications. This type of notification allows employees to see a prompt on their mobile device when someone tries to log in with their login credentials, so one way to counter MFA fatigue is to disable MFA push notifications or enable number matching to increase security. -
Limit MFA prompts
Implement a limit on the number of MFA prompts that can be sent within a certain timeframe to prevent attackers from bombarding users with requests. -
Use time-based allow listing
Allow MFA prompts only during the user's typical login hours or based on typical behaviour patterns. -
Change phone number
Users can change the phone number to which OTP codes are sent by removing the Voice call authentication factor and then setting it up again with another uninfected phone number. -
Be aware of the MFA request sender
Employees are encouraged to ensure that they are not speaking to unknown individuals pretending to be from their organisations before they approve MFA requests. -
Contact IT department
Employees are advised to contact their IT department and report account compromises. It is also important that they change the password for the account. As soon as the password is changed, the threat actor can no longer issue MFA spam. -
Organisations should educate their employees
Education is a critical component of avoiding an MFA fatigue attack. The best defence is to provide the workforce with information that explains what an MFA fatigue attack is, how it happens, and how to avoid falling victim to one.
Train your employees on MFA fatigue attacks today!
Be vigilant about evolving threats and stay updated on best practices in MFA and cybersecurity. As attackers adapt, organisations must continually refine their defences and user training.
Check out our new course with engaging animation explaining what MFA fatigue attacks are. We are confident to help your end users defeat these attacks by increasing their awareness through continuous education. Alternatively, try our 14-day free trial to experience how we can help you strengthen your cybersecurity defence.
.png)
-1.png)